- 1概念解析 | 端边云协同智能计算
- 2牛客选择题练习【二】(20道)(含答案和解析)_c语言socket编程选择题
- 3LangChain + ChatGLM-6B / ChatGLM2-6B 新手踩坑指南!_langchain结合chatglm2
- 4贵州计算机学校排名专科,贵州省2021年计算机学校好点的大专学校
- 5vue+element-ui carousel走马灯一次轮播(显示)5张图片_element-plus 走马灯实现单页多张图片轮播
- 6数字图像处理之matlab大作业:美图秀秀_matlab图像处理系统滤镜怀旧色功能
- 7Windows 环境下,cmake工程导入OpenCV库_opencvconfig.cmake
- 8canvas画圆,canvas圆环进度条效果,vue_vue canvas圆圈
- 9NSFW检测 (色情检测)
- 10数据结构 | 红黑树、平衡二叉树旋转、并查集_左根右,根叶黑,不红红,黑路同
ubuntu20.04server版本使用CLIENT-GO开发K8S——集群外的主机通过CLIENT_GO访问集群内资源(POD)_goclient 使用serviceaccount 访问k8s资源
赞
踩
一、在windows上安装OPENSSH服务于LINUX主机相互传文件
1.1、在WIN10 设置-应用-可选应用-添加应用 中选择安装OPENSSH的客服端和服务端
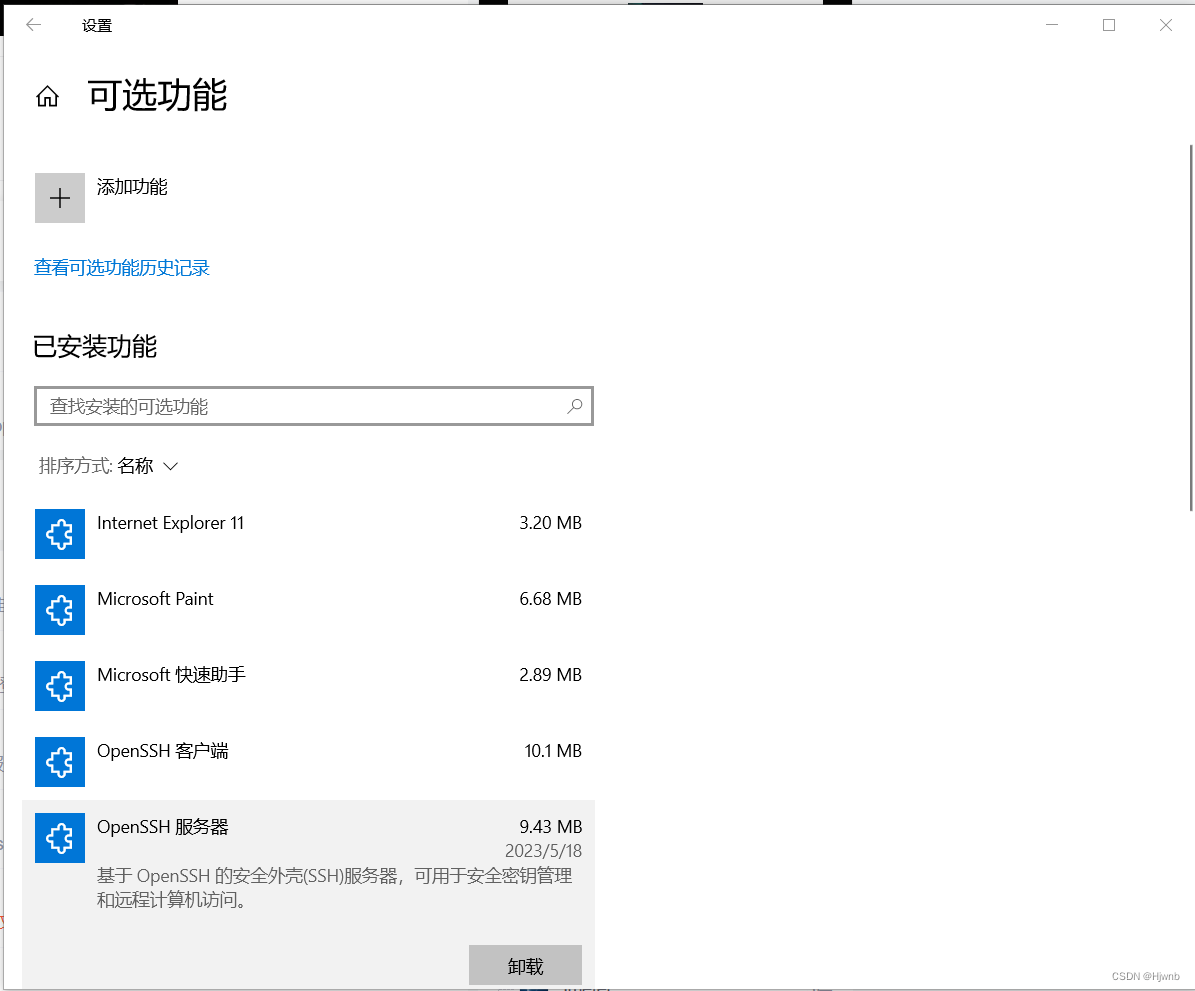
1.2、打开OPENSSH服务
在WIN10系统中按下win+r,输入services.msc,找到OpenSSH SSH Server,启动它。
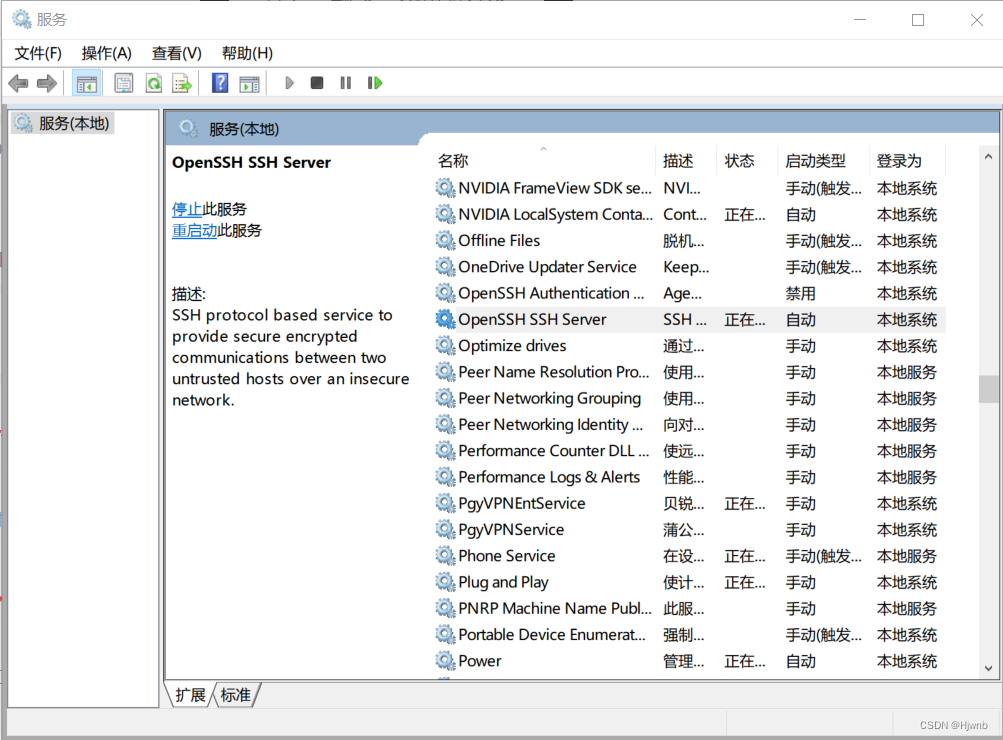
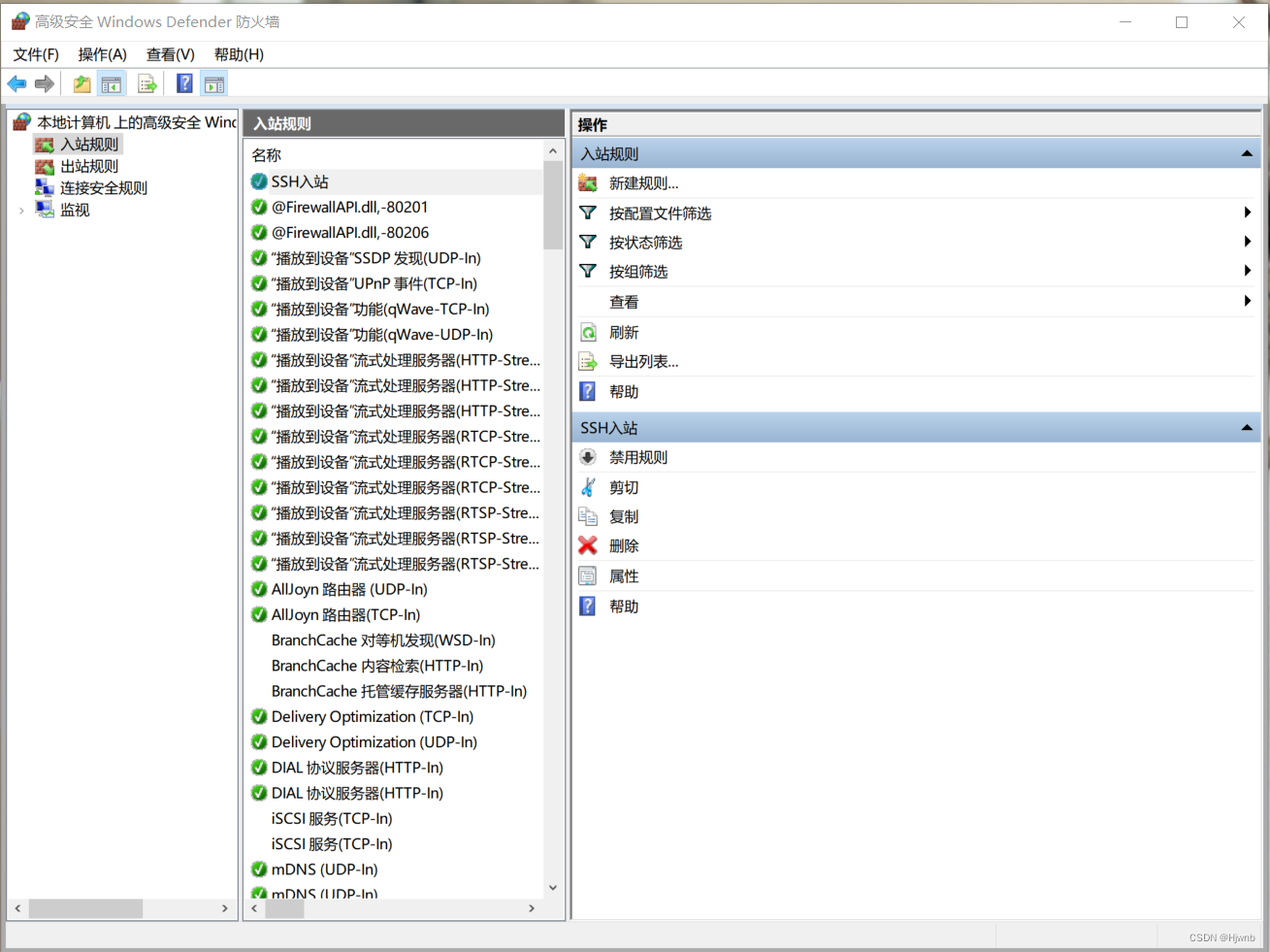
1.3、在防火墙中新建规则
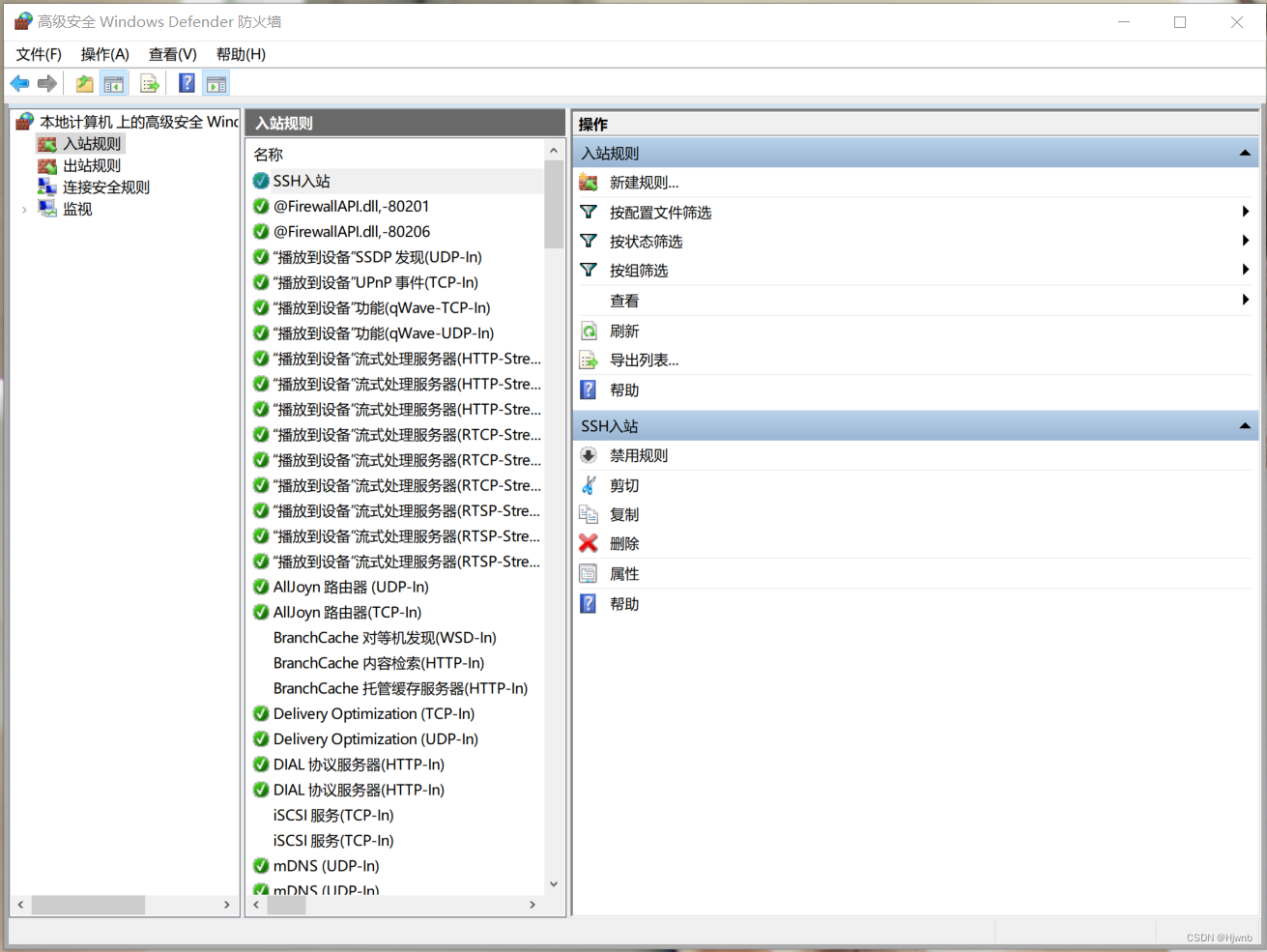
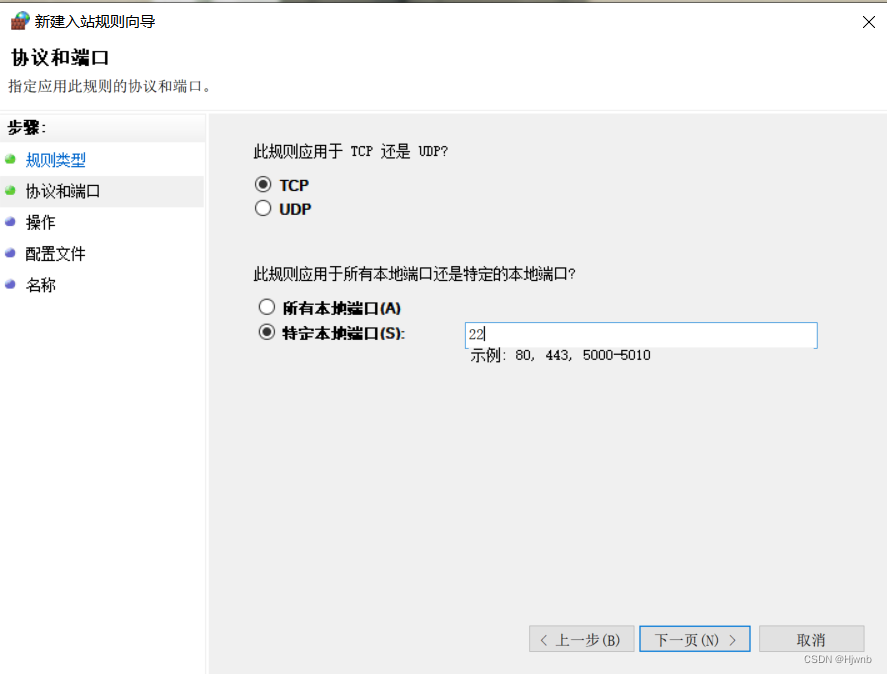
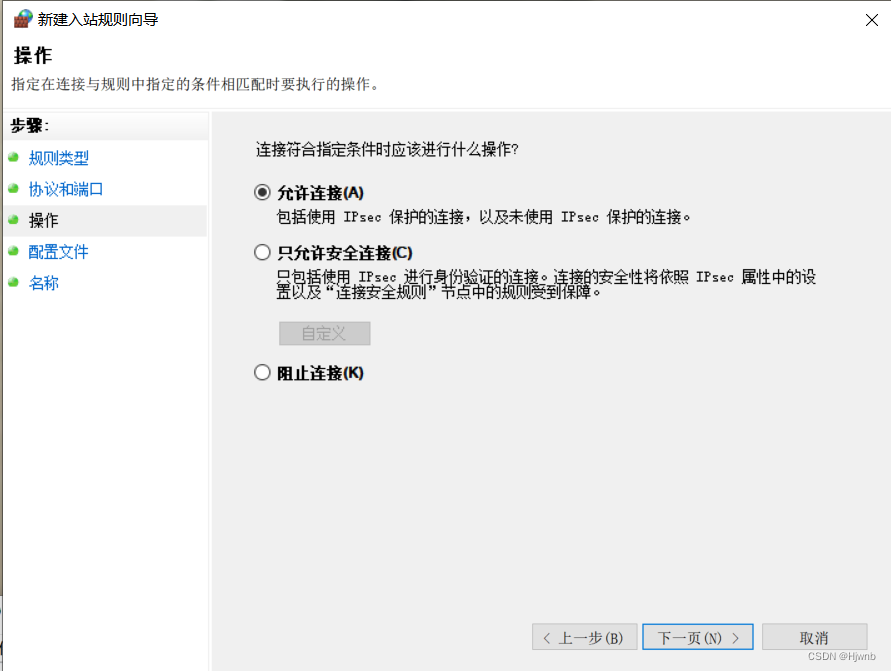
然后再自己起个名字就结束了。
1.4、使用SCP在LINUX和WIN之间相互发送文件

1.5、ssh登录远程主机报错:Someone could be eavesdropping on you right now (man-in-the-middle attack)!
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that a host key has just been changed. The fingerprint for the RSA key sent by the remote host is SHA256:这里每个人都不同 Please contact your system administrator. Add correct host key in /Users/Anan/.ssh/known_hosts to get rid of this message. Offending RSA key in /Users/Anan/.ssh/known_hosts:1 RSA host key for 这里是服务器的IP has changed and you have requested strict checking. Host key verification failed.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
会出现这些信息是因为,第一次SSH连接时,会生成一个认证,储存在客户端(也就是用SSH连线其他电脑的那个,自己操作的那个)中的known_hosts,但是如果服务器验证过了,认证资讯当然也会更改,服务器端与客户端不同时,就会跳出错误啦~因此,只要把电脑中的认证资讯删除,连线时重新生成,就一切完美啦~要删除很简单,只要在客户端输入一个指令
ssh-keygen -R +输入服务器的IP
- 1
接下來再次连接一次,會出現
Are you sure you want to continue connecting (yes/no)?
- 1
输入yes,
就完成连接啦!同時,新的认证也生成了
二、K8S配置文件
- 用于配置集群访问的文件被称为kubeconfig文件,这是引用配置文件的常用方法,但并不是说有一个名为kubeconfig的文件。
- 用于配置集群访问信息的文件叫做kubeconfig文件,在开启了TLS的集群中,每次与集群交互的时候都需要身份认证,生产环境一般使用证书进行认证,生产环境一般使用证书进行认证,其认证所需要的信息都会放在kubeconfig文件中。此外,K8S的组件都可以使用kubeconfig连接apiserver,client-go、operator、helm等其他组件也是用kubeconfig访问apiserver。
- 使用kubeconfig文件来组织有关集群、用户、命名空间的身份认证的信息。kubectl命令行根据使用kubeconfig文件来查找选择集群所需要的信息,并与集群的API服务器通信。
- 默认情况下,kubectl 在 ¥HOME/.kube的目录下查找名为config的文件,在linux中的目录是~/.kube/config。可以通过设置KUBECONFIG环境变量或者–kubeconfig参数来指定其他的kubeconfig文件。
2.1、我的linux服务器中config文件内容如下:
apiVersion: v1 clusters: - cluster: certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUMvakNDQWVhZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJek1ESXlNakV4TXpFek1sb1hEVE16TURJeE9URXhNekV6TWxvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTll2CkhNeEx5OVBpSUJSYjJGZ2ZPeCttR3Rpbm1tV0d2Tndkb2I3bGpJRVQ5cmVmam1KS1d0M0lVRGJlN1dFVGxlOCsKUTM0NmZpQ0pqbllpazIxeXpoMGR6eThBSkk1Zkp0VW5ZR3ZUQXp4Q00yV1dUdEIxakR0OU1mUWpra3VnbTE0cApHQms2TFZzc0x5d1VSSkgzZm1Yc0VNamROZzVmWEdzWHZGVnJwSS9GSHl4UDJjRDFVaVpwVVMwdHpDcDRPZjhEClV2aE5EVDVRYVBIM1ZZNFJqMW9HZHZwRkxybW5xVUhwd2l5UEliUDJYaVEwY1p2bkNNSFBUSHU0cU91MUdiUWcKZ013U2xvUGkzT1hPclFwYjdaMFhYWlpReTAySUhTaWFMRVk2eTNEKzJVMUNRMnNxVDhWNk03NTJqbkZqalgvZwpEV2FOTTFVVTFSaW1nR0pHL1I4Q0F3RUFBYU5aTUZjd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZLa2kvWmFvcFJjV2Q3Y0tFTEsveHRjYlZGVWtNQlVHQTFVZEVRUU8KTUF5Q0NtdDFZbVZ5Ym1WMFpYTXdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBQ0FRakRNM1JpU09IWE5TUXlldwpIeDBDMjFWaW9EdmF3MmlnWTNlMk5oM0JEQUlDK2lFeEp5NW5hNmFPTkN3ZlFKSmVidGhSeHNJSmlpdTlqaEZ1Ckt3ZkRuMDdDZHBiMk12d0Z4Y2MycFZndjBJd1d3Tk90OXU2TnAydjRoZ0Q0Z1lBWTlEQUN3anU5WldPWVMwS3kKVis3WDhhTk5LMk5kMVdPbmVOSTZSdFU1T2VhaVJMT0tvNGpuK3JOUnJrUSswUThNeWxxc0RZLzY1VGdHOXpJSQpDUUtRU2ZkeisrWmNPSnc3dDY2ZXdwZUJ6UVJGNmpXNDI3aVNnL21PVFVGdHNJd1gvenJvZ0Z4QWlUYzFZSW1LCmpUeG5vWjFUamc2OEZkNitHNXdJRG1pbEpIQ25mOC9NSElZTlBld2dmSXk3bkFqQWh5dkxLbnUxT3RDL2FMc3cKVldVPQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg== server: https://192.168.1.105:6443 name: kubernetes contexts: - context: cluster: kubernetes user: hjw name: hjw - context: cluster: kubernetes user: kubernetes-admin name: kubernetes-admin@kubernetes current-context: hjw kind: Config preferences: {} users: - name: hjw user: client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUNxakNDQVpJQ0ZFdkRsY24vQWJqcit1OEJoRDQ2SkFnUGVJdUtNQTBHQ1NxR1NJYjNEUUVCQ3dVQU1CVXgKRXpBUkJnTlZCQU1UQ210MVltVnlibVYwWlhNd0hoY05Nak13TlRFNU1UTTBNakUxV2hjTk1qUXdOVEU0TVRNMApNakUxV2pBT01Rd3dDZ1lEVlFRRERBTm9hbmN3Z2dFaU1BMEdDU3FHU0liM0RRRUJBUVVBQTRJQkR3QXdnZ0VLCkFvSUJBUUNtQWdSVEt3dmswc0NSOHRCZEpvYkpSelBJTFBjVFMrbkYvNENzdTc5UW56cVpTeStrS2Zla3R2UXgKZk1NMXBXYStuTG5QMEpaQ1VnMFcrYnIySzZ6OE9EM0pKcHpodC9oQTZXclhsRDZaY0lDeEd0bzZxY0JJQ3hHMgozRlNubEhrZkdTWG5iK24rc0dqaStwTTBmTjNzc2VvRks5cnNCTS9QRWpSS0V2cldOUUx6WFAzUWdLc0NuYjZWCjMwWTI5ZThlUnpOMC9uSytnWHJaTjU3Ym4weDRSbTFLWFVhcjlEeDJ5b1JHdElnK0pBTDVScDUrR3FXczZOZ2MKRHZHTVFvTVpwMUhOQ0h6N0xUVkdJVGVtQ2xaSTdnVmxmUk1UV3VCWE11WTByMGVpWWZZYlgrSzhTNXNHWTFjSAp0RXZaRTBRQlhKZUNOb0xHNVZyc2xmRnlOOUVEQWdNQkFBRXdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBTVpICm9GTEc0aHFoVStDR0JjQWd5dFJtQ2hGT3dqalRyMGduYzdwK2N6T0lCbnZqWGluNVRsSEFTSS9qRHAxYloxdnMKQVoydk41QUFUbWREUVptK2lHV3FVUnlUbDM0LzJlWWFjTCtLcFozN1pObnk1Wk9YZ2k0WFhOT0pPZW5NRzNBNgpxMHpzUkZ1MFFvNWRFSnVXUUhsaE50dXAzdVIwU0xQVVFtei9xMnFwMlRRdmlVVFF2SnlRaERYWlFEZ0VtRXY5ClRLUVlEQWlqNWdNT3ZWR3pKalZaejIwRVhhU3N3djZlNE50MEozNUJqZmZpNEthckJrR3hmVWRYa3YwZGdTeEMKMEs4NE5KdUdJTWVCdUpwTmRwQnVrc3VWQ1Y0SkJhVDF0aWVWN2JSTG9Lb2tsbUtSMmFjZUtQbVA2NHRxVTY4bwo1OC8vckFxR2dkYWwyeHYrVTlRPQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg== client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb3dJQkFBS0NBUUVBcGdJRVV5c0w1TkxBa2ZMUVhTYUd5VWN6eUN6M0UwdnB4ZitBckx1L1VKODZtVXN2CnBDbjNwTGIwTVh6RE5hVm12cHk1ejlDV1FsSU5Gdm02OWl1cy9EZzl5U2FjNGJmNFFPbHExNVErbVhDQXNScmEKT3FuQVNBc1J0dHhVcDVSNUh4a2w1Mi9wL3JCbzR2cVROSHpkN0xIcUJTdmE3QVRQenhJMFNoTDYxalVDODF6OQowSUNyQXAyK2xkOUdOdlh2SGtjemRQNXl2b0Y2MlRlZTI1OU1lRVp0U2wxR3EvUThkc3FFUnJTSVBpUUMrVWFlCmZocWxyT2pZSEE3eGpFS0RHYWRSelFoOCt5MDFSaUUzcGdwV1NPNEZaWDBURTFyZ1Z6TG1OSzlIb21IMkcxL2kKdkV1YkJtTlhCN1JMMlJORUFWeVhnamFDeHVWYTdKWHhjamZSQXdJREFRQUJBb0lCQVFDRG56SENwMnpFdnYwRQpPeHRONEJBYVlxUUI0UFQ5amNFS3hleEdDSTVGNUJuWUZTN3U0SCtEVDdRSjBMd09PdGhkNVhIRi9jSkZUejBsCnJGZTZleUtxMEFUZENncDFSU0pHaFV1N0pjVUViNWo1MHlxWVBLTkIrOVROd2FBMVJwbEtPT3crdGhNM1pyT2kKMDc0SGJjR2Z1K2lxdFB6ZENXdWk2UElna1Mva3lkaG1YV0hYUlNGcTF6VC83d1d3ODRzajMxZ2NtejdxMXVWUgpYOGVZd3NRc1lCMGwzNGFKWW12TmlJa3BZTnFybmtYZmxyc3Z5Y0lYYWdVUzFkZGpsYkVGcW9iUFBseGxwUFhJCk56VTFmVVIyaGZtYkZBZGRZb1lrcEtZS213TmpRczdhbmZiMjMvK0I1YkM0RTBaZy9vZm16bDJxOTgrZlhyY1IKem5VY0hhMHhBb0dCQU05S1RxTW9YQ0RqS21TNmp5eTN1S0NkcG1udDgzdWNLaVAzRFJlQlQ4cWF5S3VhV3JJbQp4RnlCV2ZETFZnbHBNcDlLWVRZMy84VHdtQXhjZVByS1RUVVk0cVA0bUFsYnBLOUtDV0dCdi9YTlpyMGhBZXV0CnNrRmxKa2pSbmkydDBweTFyYlk4b3Q5VlhQQ3U0OHlmVUQvVm9GQ0N1UkFsQXZDbTNNcFhnUEcxQW9HQkFNMEUKVnEvRVVZdlk2czNUTnB4ZWtjeDRlaHBmNFFDVlJZaWFKd1FpQzg5bFIyWGlSMUNzNlRodXAyK24wVWxxR1M0RApQT1EwNzVBb3NTM1REN1g1aEJZdjJZNVI1L2I2Ykg1UUl5a3NLNzQzOFM5OXNRS1pBOURsY1dRN09YaDZLUjYrCk9XN1JSUXQrak5zS2xyUnVzd29pcU1GbzFiWVNuL1pCb3UzTjVNclhBb0dBTVdJVmU5ODRtNGtpNTE1ZWo1dXgKTzJwelk5Y1JZNGhmcmJQRWhhNEQwVk93ck5rWDlFc3lDb3V5WHFCQ2ZmbDIydVlBWk1kUWdwMkN5NmNZRno4cwp4NUtISStNc2JVWk01SW14MUczeHltQkZzcGJ6ZXk4bFFWa1VsdEtCYVlaNG4yYlUzSTV6aXRzdVNoU1FKb1pwCnV0dHMxdUZkcjAveDlGejhTcVF3RHVVQ2dZQXhkR2Q0MU5HYSs0T0FqUCt5YnJtYTZrRUNGYmpRRERJT3hxaTgKdlgyOTFMK0pXekU2eThzaWVzYlhEMU5UODAwSnBXeE4zRnNobWo5TFA0dWRxUWZzMWpRVHVieEwvcEtuVWF0NQpwaGNUTnFsdWZGSnp2dmVGcjZOUHUxMmNxMU02QUVjWWJWRExlZ1orWENxSWNkK3NoVG5TRmZqZmg5U2djYXJjCjFIcnBWd0tCZ0FVUGU5TTdCRW1wenlrMHlsV1pQWU4vV0dsRFc4ekl1TmRKNmlwNVUwd2UvbVZFQnJDZ0k5RXcKWEoxa3IycTVscnBWUGdFUzgwU3ZVZ0x6dkpqL1ZCUU5GTlMrWUJRYlB4WFc2d0Y5R2JZNmpDMG90UVoyUklYeAppODByTTBxM3lyOEZsNVc1TVJINURZRkRNVDllV2J0RDU1VHhCbTBGSjNmVitpK2ZIZmZQCi0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg== - name: kubernetes-admin user: client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURJVENDQWdtZ0F3SUJBZ0lJVm9PMDRzTW5oUkV3RFFZSktvWklodmNOQVFFTEJRQXdGVEVUTUJFR0ExVUUKQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TXpBeU1qSXhNVE14TXpKYUZ3MHlOREF5TWpJeE1UTXhNelJhTURReApGekFWQmdOVkJBb1REbk41YzNSbGJUcHRZWE4wWlhKek1Sa3dGd1lEVlFRREV4QnJkV0psY201bGRHVnpMV0ZrCmJXbHVNSUlCSWpBTkJna3Foa2lHOXcwQkFRRUZBQU9DQVE4QU1JSUJDZ0tDQVFFQXRvc1A0WmRFZW1aRSszNmQKQVdsanlEUld0U1hSTlRkMEpRREpSWUhZMUFMU0JLT0NUWVBoblRjQ2Qrb05ERENPM1JqYXhhZnM4aFFSNDRZYwpkZmhYZTR2L2Zid1FYVHZSeFZFaUNkZkt4UzhzakppZ3ZFTGp5VU5YUTdYb3NCR1VaaDFzQ3dxQkxxNjc0czJRCkR4aFJmYnBUY3pKVjh4S096UTFFcmN3RExLOWhWRTFhYW81WENtQXVaUnY3YXowL0FZV1hwWnpwTUlKS0NObCsKbms4VUpoZExvZU1oYjVuSkJZeS8rMTcwc3ZoRkFqSWpJYklwM2g5bkd5U1RtMEZpOHlTVk9nYm83TEFWek9yZgpJTlh4WElmWTAyeU5ldndtdmhuMUdGaHBNUkcydE1VYzF3YlRya0M2TllaNFRDYWhTQm9SQmRqV1FDUVIvWnVDCkMzQW56d0lEQVFBQm8xWXdWREFPQmdOVkhROEJBZjhFQkFNQ0JhQXdFd1lEVlIwbEJBd3dDZ1lJS3dZQkJRVUgKQXdJd0RBWURWUjBUQVFIL0JBSXdBREFmQmdOVkhTTUVHREFXZ0JTcEl2MldxS1VYRm5lM0NoQ3l2OGJYRzFSVgpKREFOQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBV2p0VnU5VStsVjN6TDNTV0NYVzFzMEU1anJZZDFTeFdUV2NTCnAwRlBjL0NaNDdXNjluaFJVVVMxOHplOVgrTnE4c2x6TXhVVmRJZEZhT2xDUDV3eFNiOXQxemkvNGRLdTFSNysKZkVXZUlUb2psRVJFRTNTM1k2K3AvbEpvUy9Nais2Uno1NWsyalhVYmFQZDFNN08wTy91MTduQUx6bXAxT2pYRAorenhoeEFpdU5pUzBzdlR5OXhIWitsS2NPV1RCL0E0b3FkWm1uL2lGQnRJVm4wRDl2TU9EaXF3VVBQUFdqRzJ3Cll1dUlWeWFBL0wvWlVCcURKVm0rRU1odzBHZHFmUHZyMmRvczIyb0RBMjFZTmdRcEx2NlZyaE9TMkY0V2FDZ2YKa3VVeVVET2NIekVkdnpzOHRUWGw5bGpVbEpLVXhFSXJUOEp5Mi9iamtJekMzd2RWc2c9PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg== client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcEFJQkFBS0NBUUVBdG9zUDRaZEVlbVpFKzM2ZEFXbGp5RFJXdFNYUk5UZDBKUURKUllIWTFBTFNCS09DClRZUGhuVGNDZCtvTkREQ08zUmpheGFmczhoUVI0NFljZGZoWGU0di9mYndRWFR2UnhWRWlDZGZLeFM4c2pKaWcKdkVManlVTlhRN1hvc0JHVVpoMXNDd3FCTHE2NzRzMlFEeGhSZmJwVGN6SlY4eEtPelExRXJjd0RMSzloVkUxYQphbzVYQ21BdVpSdjdhejAvQVlXWHBaenBNSUpLQ05sK25rOFVKaGRMb2VNaGI1bkpCWXkvKzE3MHN2aEZBaklqCkliSXAzaDluR3lTVG0wRmk4eVNWT2dibzdMQVZ6T3JmSU5YeFhJZlkwMnlOZXZ3bXZobjFHRmhwTVJHMnRNVWMKMXdiVHJrQzZOWVo0VENhaFNCb1JCZGpXUUNRUi9adUNDM0FuendJREFRQUJBb0lCQUdHQnNLOEEvVHdnYXRLbwpGRGZQMHRQN1dTR1VITWMvWXRQdE1wWGxRU3dtZ1lhbXpKQ1pWS2VFM2RXdCtPQTlBK01JUnJ2ejhqWnhFQWtuCjl3WHc3Tkg2dXpPdmhGSTVCTmxRZUUwbnJwRmJuSUZSZWZKMkRIVFNlc2VaWUx6RDl6QUFvVmpZZUo2MkNYaWgKODBTTTZlS3Q1NnVPQktrOWpYZnNrWFlBbHVXRHRoRm11eFNnclFSQnZzZlRuVmM3ZDEzZ2VJM1BrREZDNHVGZgpmQWFUczZXaVRGZEdHakJMc2diRlVTTnZCM3cyakRBYU1WSUlQTm96VklVRndYQzV1YndGbXZVNzlDWTBNRGlwCmx5Q3FoTVlKY2RjVE1DL0hGaTdWOHh6MCtGRDV3ZEdMSzFFNDdtSTErVlF0UlZKL1M4eVRUNFZwamNEM1dJR3YKcEtMa1luRUNnWUVBMjZPTmxxdG1sc280cmdvTmRhVU0xSEVsQytZSFpva05HaDBYbUc4TXhQNE8zM2RMSzZaaQpRb1EyQ0I4cWNPSFoxcEs5eVdKV0wxYkJST2p4ZXpyYTJsWmN6ZDRJaEc2Tk5uSnpTSzFYVk1tWHRKaWJ1M0Y0CktVS3Y2V2x1VmRrTTh3bk9CMSthVTMxb0lsZW1lVGJqT2NFR0RIYlNCeGpvVERtU0cxVldzU2NDZ1lFQTFNTmUKZHNpdmgrQmxCaDRmbHVia3UwSXE3TlRUc1BldnFOUkpzK0wxZ2gvU0xScU5weWZXbnU4WUtqd0x0NTUvMERYYgpIVldwdU5zK2xLN2QyS1JNZ3VHS1ZpaDBIbTlKNlp0b0NPeVk5cnl0bE1OUzc0UHg0emNKMHVvY2JmNTFPdEErCi9BdFV4K1JaOEVGMDVYOUhzOEhvdDhhdE4vVHpKVG9sSVF1akxSa0NnWUVBenhXcTVyZGVkNmZjdndOTlkzR2wKNGh0M3dYczEyUkE1SVRqeXlVOVM2OTFhYW9uUWZ5eFdFcjhUTHA4cjVkaWNDanE2NUVocVdDSGxBYkxjRThNUApHN00zdHdhMFl5RFUxZFFkTEJYN2REN0tZWVZOdC9LcFI4WFBsRFJLeW5obVJEUW5aRDVZaElXR0RITTF5NjNiCm1kV0xmVzcrWWFDelRVTXVwY1RWZ3hzQ2dZRUFnRGpkalNpVTRJWlRXOFI3dFMyaFcxa2RGVzJOeG5EKzQvaE0KRXFVTTRFYmRHMkdOVE5ldGVFc1BmU1NDeXo0eU9RQzc5SW5UcHh3Nk10RFAwZWZ5VkU0b1dKUTRwcjdiQkhZcgoxSFVDR25ETEM0UkxUeDF0Z1VtQ0dpSU0wQjB4K1NmWFRYNW1zYkRrb3U1UHpKOVFUdnpsaXh1bytMZ2VjS2tDCkIxQkVIc0VDZ1lCRWRXOWw4N01IVE1mcDBpWUsweXVPN0lkV3B4TDl1VDRPeUtZaWYxK3pOT1hqRjNySlVnamkKMWU0NGN0YUh1cVVFY2diWDcyMmdQZy9TLzlteXdOMUZjaGFCcW1GMzZZVnZJaVpOTGJiMTFJZHp3bXJyY3lVbApCTHV5ZVB0aVBTeGFNQjN4T2VGMVV6ZnNTMCsrQnpTTStFcFBWcEpRN1BHS1JrbXpqcWVhMHc9PQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
其中apiVersion和kind标识客户端解析器的版本和模式,不应手动编辑。preferences指定当前可选(和当前未使用)的kubectl首选项。
2.2、cluseter
cluster中包含k8s集群的端点数据,包括集群的证书颁发机构以及完整的URL。可以使用Kubectl config set-cluster添加或修改cluster条目。多个集群的话直接在后面添加-cluster部分即可。
2.3、contexts
- contexts定义了一个命名的cluster、user、namespace元组,用于使用提供的认证信息和命名空间将请求发送到指定的集群。
- 三个都是可选的,仅使用 cluster、user、namespace 之一指定上下文,或指定none。
- 未指定的值或在加载的kubeconfig中没有相应条目的命名值将被替换为默认值。
- 可以使用kubectl config set-context添加或修改上下文条目。
2.4、current-context
current-context 是作为cluster、user、namespace元组的 key,当 kubectl 从该文件中加载配置的时候会被默认使用。
可以在 kubectl 命令行里覆盖这些值,通过分别传入–context=CONTEXT、 --cluster=CLUSTER、–user=USER 和 --namespace=NAMESPACE。
若不指定 context 则默认使用 cluster1-context。可以使用kubectl config use-context 更改 current-context。
2.5、users
users 定义用于向 k8s 集群进行身份验证的客户端凭据。可用凭证有 client-certificate、client-key、token 和 username/password。username/password 和 token 是二者只能选择一个,但 client-certificate和 client-key 可以分别与它们组合。
可以使用kubectl config set-credentials添加或者修改 user 条目。
2.6、kubectl 生成 kubeconfig 的示例
kubectl 可以快速生成 kubeconfig,以下是一个示例:
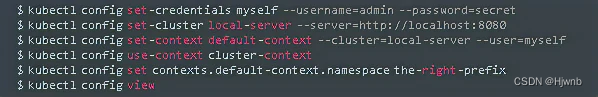
若使用手写 kubeconfig 的方式,推荐一个工具 kubeval,可以校验 kubernetes yaml 或 json 格式的配置文件是否正确。
2.7、使用kubeconfig文件配置kubectl跨集群认证
kubectl 作为操作 k8s 的一个客户端工具,只要为 kubectl 提供连接 apiserver 的配置(kubeconfig),kubectl 可以在任何地方操作该集群。若要使用多个集群, kubeconfig 文件中配置多个集群,kubectl 可以在多个集群间切换。如第一部分的示例文件中就设置了2个集群。
kubectl加载配置文件的顺序:
- kubectl 默认连接本机的 8080 端口
- 从 $HOME/.kube 目录下查找文件名为 config 的文件
3)通过设置环境变量 KUBECONFIG 或者通过设置去指定其它 kubeconfig 文件
#设置KUBECONFIG的环境变量
export KUBECONFIG=/etc/kubernetes/kubeconfig/kubelet.kubeconfig
#指定kubeconfig文件
kubectl get node --kubeconfig=/etc/kubernetes/kubeconfig/kubelet.kubeconfig
#使用不同的 context在多个集群之间切换
kubectl get node --kubeconfig=./kubeconfig --context=cluster1-context
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
三、K8S RBAC
3.1、RBAC介绍
在k8s中授权有ABAC(基于属性的访问控制)、RBAC(基于角色的访问控制)、Webhook、Node、AlwaysDeny(一直拒绝)和AlwaysAllow(一直允许)这6种模式。从1.6版本起,Kubernetes 默认启用RBAC访问控制策略。从1.8开始,RBAC已作为稳定的功能。通过设置–authorization-mode=RBAC,启用RABC。在RABC API中,通过如下的步骤进行授权:1)定义角色:在定义角色时会指定此角色对于资源的访问控制的规则;2)绑定角色:将主体与角色进行绑定,对用户进行访问授权。
1、 角色和集群角色
在RBAC API中,角色包含代表权限集合的规则。在这里,权限只有被授予,而没有被拒绝的设置。在Kubernetes中有两类角色,即普通角色和集群角色。可以通过Role定义在一个命名空间中的角色,或者可以使用ClusterRole定义集群范围的角色。一个角色只能被用来授予访问单一命令空间中的资源。
集群角色(ClusterRole)能够被授予如下资源的权限:
集群范围的资源(类似于Node)
非资源端点(类似于”/healthz”)
集群中所有命名空间的资源(类似Pod)
2、角色绑定和集群角色绑定
角色绑定用于将角色与一个或一组用户进行绑定,从而实现将对用户进行授权的目的。主体分为用户、组和服务帐户。角色绑定也分为角色普通角色绑定和集群角色绑定。角色绑定只能引用同一个命名空间下的角色。
角色绑定也可以通过引用集群角色授予访问权限,当主体对资源的访问仅限与本命名空间,这就允许管理员定义整个集群的公共角色集合,然后在多个命名空间中进行复用。
集群角色可以被用来在集群层面和整个命名空间进行授权。
3、资源
在Kubernets中,主要的资源包括:Pods、Nodes、Services、Deployment、Replicasets、Statefulsets、Namespace、Persistents、Secrets和ConfigMaps等。另外,有些资源下面存在子资源,例如:Pod下就存在log子资源
4、主体
RBAC授权中的主体可以是组,用户或者服务帐户。用户通过字符串表示,比如“alice”、 “bob@example.com”等,具体的形式取决于管理员在认证模块中所配置的用户名。system:被保留作为用来Kubernetes系统使用,因此不能作为用户的前缀。组也有认证模块提供,格式与用户类似。
角色
• Role:授权特定命名空间的访问权限
• ClusterRole:授权 所有命名空间 的访问权限
角色绑定
• RoleBinding:将角色绑定到主体(即subject)
• ClusterRoleBinding:将 集群角色绑定到主体
主体(subject)
• User:用户
• Group:用户组
• ServiceAccount:服务账号
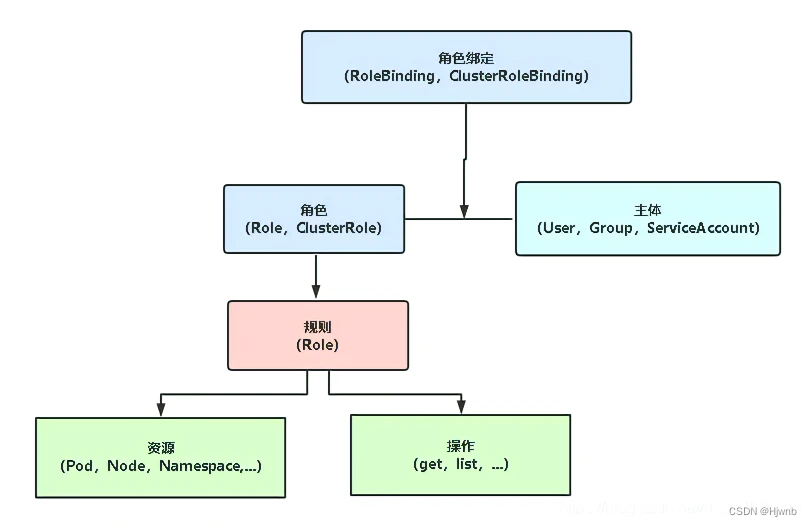
可以参考这篇博客https://www.jianshu.com/p/2a63a8452741
3.2 用户分类
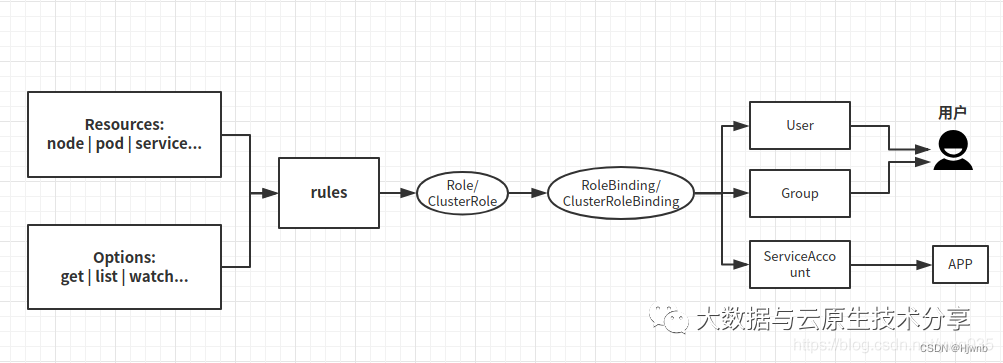
K8s的用户分两种,一种是普通用户,一种是ServiceAccount(服务账户)。
1、普通用户
普通用户是假定被外部或独立服务管理的。管理员分配私钥。平时常用的kubectl命令都是普通用户执行的。
如果是用户需求权限,则将Role与User(或Group)绑定(这需要创建User/Group),是给用户使用的。
2、ServiceAccount(服务账户)
ServiceAccount(服务帐户)是由Kubernetes API管理的用户。它们绑定到特定的命名空间,并由API服务器自动创建或通过API调用手动创建。服务帐户与存储为Secrets的一组证书相关联,这些凭据被挂载到pod中,以便集群进程与Kubernetes API通信。(登录dashboard时我们使用的就是ServiceAccount)
如果是程序需求权限,将Role与ServiceAccount指定(这需要创建ServiceAccount并且在deployment中指定ServiceAccount),是给程序使用的。
相当于Role是一个类,用作权限申明,User/Group/ServiceAccount将成为类的实例。
工作流程图如下:
3.3、为指定用户授权访问不同命名空间的权限
k8s预定好了四个集群角色供用户使用,使用kubectl get clusterrole查看,其中systemd:开头的为系统内部使用。(以system开头的是绝对不能删除的,删除了可能导致集群异常)
内置集群角色 描述
- cluster-admin 超级管理员,对集群所有权限(在部署dashboard的时候,先创建sa,然后将sa绑定到角色cluster-admin,最后获取到token,这就使用了内置的cluster-admin )
- admin 主要用于授权命名空间所有读写权限
- edit 允许对命名空间大多数对象读写操作,不允许查看或者修改角色、角色绑定。
- view 允许对命名空间大多数对象只读权限,不允许查看角色、角色绑定和Secret
root@master-node:~/.kube# kubectl api-resources NAME SHORTNAMES APIVERSION NAMESPACED KIND bindings v1 true Binding componentstatuses cs v1 false ComponentStatus configmaps cm v1 true ConfigMap endpoints ep v1 true Endpoints events ev v1 true Event limitranges limits v1 true LimitRange namespaces ns v1 false Namespace nodes no v1 false Node persistentvolumeclaims pvc v1 true PersistentVolumeClaim persistentvolumes pv v1 false PersistentVolume pods po v1 true Pod podtemplates v1 true PodTemplate replicationcontrollers rc v1 true ReplicationController resourcequotas quota v1 true ResourceQuota secrets v1 true Secret serviceaccounts sa v1 true ServiceAccount services svc v1 true Service mutatingwebhookconfigurations admissionregistration.k8s.io/v1 false MutatingWebhookConfiguration validatingwebhookconfigurations admissionregistration.k8s.io/v1 false ValidatingWebhookConfiguration customresourcedefinitions crd,crds apiextensions.k8s.io/v1 false CustomResourceDefinition apiservices apiregistration.k8s.io/v1 false APIService controllerrevisions apps/v1 true ControllerRevision daemonsets ds apps/v1 true DaemonSet deployments deploy apps/v1 true Deployment replicasets rs apps/v1 true ReplicaSet statefulsets sts apps/v1 true StatefulSet tokenreviews authentication.k8s.io/v1 false TokenReview localsubjectaccessreviews authorization.k8s.io/v1 true LocalSubjectAccessReview selfsubjectaccessreviews authorization.k8s.io/v1 false SelfSubjectAccessReview selfsubjectrulesreviews authorization.k8s.io/v1 false SelfSubjectRulesReview subjectaccessreviews authorization.k8s.io/v1 false SubjectAccessReview horizontalpodautoscalers hpa autoscaling/v2 true HorizontalPodAutoscaler cronjobs cj batch/v1 true CronJob jobs batch/v1 true Job certificatesigningrequests csr certificates.k8s.io/v1 false CertificateSigningRequest leases coordination.k8s.io/v1 true Lease bgpconfigurations crd.projectcalico.org/v1 false BGPConfiguration bgppeers crd.projectcalico.org/v1 false BGPPeer blockaffinities crd.projectcalico.org/v1 false BlockAffinity caliconodestatuses crd.projectcalico.org/v1 false CalicoNodeStatus clusterinformations crd.projectcalico.org/v1 false ClusterInformation felixconfigurations crd.projectcalico.org/v1 false FelixConfiguration globalnetworkpolicies crd.projectcalico.org/v1 false GlobalNetworkPolicy globalnetworksets crd.projectcalico.org/v1 false GlobalNetworkSet hostendpoints crd.projectcalico.org/v1 false HostEndpoint ipamblocks crd.projectcalico.org/v1 false IPAMBlock ipamconfigs crd.projectcalico.org/v1 false IPAMConfig ipamhandles crd.projectcalico.org/v1 false IPAMHandle ippools crd.projectcalico.org/v1 false IPPool ipreservations crd.projectcalico.org/v1 false IPReservation kubecontrollersconfigurations crd.projectcalico.org/v1 false KubeControllersConfiguration networkpolicies crd.projectcalico.org/v1 true NetworkPolicy networksets crd.projectcalico.org/v1 true NetworkSet endpointslices discovery.k8s.io/v1 true EndpointSlice events ev events.k8s.io/v1 true Event flowschemas flowcontrol.apiserver.k8s.io/v1beta3 false FlowSchema prioritylevelconfigurations flowcontrol.apiserver.k8s.io/v1beta3 false PriorityLevelConfiguration ingressclasses networking.k8s.io/v1 false IngressClass ingresses ing networking.k8s.io/v1 true Ingress networkpolicies netpol networking.k8s.io/v1 true NetworkPolicy runtimeclasses node.k8s.io/v1 false RuntimeClass poddisruptionbudgets pdb policy/v1 true PodDisruptionBudget clusterrolebindings rbac.authorization.k8s.io/v1 false ClusterRoleBinding clusterroles rbac.authorization.k8s.io/v1 false ClusterRole rolebindings rbac.authorization.k8s.io/v1 true RoleBinding roles rbac.authorization.k8s.io/v1 true Role priorityclasses pc scheduling.k8s.io/v1 false PriorityClass csidrivers storage.k8s.io/v1 false CSIDriver csinodes storage.k8s.io/v1 false CSINode csistoragecapacities storage.k8s.io/v1 true CSIStorageCapacity storageclasses sc storage.k8s.io/v1 false StorageClass volumeattachments storage.k8s.io/v1 false VolumeAttachment
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
上面这些角色,如果有需要就不要再去自己去创建角色,直接拿来使用即可。
3.3.1、创建RBAC权限策略
需要创建role和rolebinding,role是权限的集合,rolebinding是要将role里面权限绑定到指定的用户,也就是我们上面的lulei用户
比较常见的授权维度:
-
user:用户名
-
group:用户分组
-
资源,例如pod、deployment
-
资源操作方法:get,list,create,update,patch,watch,delete
-
命名空间
-
API组

可以通过kubectl api-resources查看k8s当中所有资源,并且资源属于哪个组
root@master-node:~/.kube# kubectl api-resources NAME SHORTNAMES APIVERSION NAMESPACED KIND bindings v1 true Binding componentstatuses cs v1 false ComponentStatus configmaps cm v1 true ConfigMap endpoints ep v1 true Endpoints events ev v1 true Event limitranges limits v1 true LimitRange namespaces ns v1 false Namespace nodes no v1 false Node persistentvolumeclaims pvc v1 true PersistentVolumeClaim persistentvolumes pv v1 false PersistentVolume pods po v1 true Pod podtemplates v1 true PodTemplate replicationcontrollers rc v1 true ReplicationController resourcequotas quota v1 true ResourceQuota secrets v1 true Secret serviceaccounts sa v1 true ServiceAccount services svc v1 true Service mutatingwebhookconfigurations admissionregistration.k8s.io/v1 false MutatingWebhookConfiguration validatingwebhookconfigurations admissionregistration.k8s.io/v1 false ValidatingWebhookConfiguration customresourcedefinitions crd,crds apiextensions.k8s.io/v1 false CustomResourceDefinition apiservices apiregistration.k8s.io/v1 false APIService controllerrevisions apps/v1 true ControllerRevision daemonsets ds apps/v1 true DaemonSet deployments deploy apps/v1 true Deployment replicasets rs apps/v1 true ReplicaSet statefulsets sts apps/v1 true StatefulSet tokenreviews authentication.k8s.io/v1 false TokenReview localsubjectaccessreviews authorization.k8s.io/v1 true LocalSubjectAccessReview selfsubjectaccessreviews authorization.k8s.io/v1 false SelfSubjectAccessReview selfsubjectrulesreviews authorization.k8s.io/v1 false SelfSubjectRulesReview subjectaccessreviews authorization.k8s.io/v1 false SubjectAccessReview horizontalpodautoscalers hpa autoscaling/v2 true HorizontalPodAutoscaler cronjobs cj batch/v1 true CronJob jobs batch/v1 true Job certificatesigningrequests csr certificates.k8s.io/v1 false CertificateSigningRequest leases coordination.k8s.io/v1 true Lease bgpconfigurations crd.projectcalico.org/v1 false BGPConfiguration bgppeers crd.projectcalico.org/v1 false BGPPeer blockaffinities crd.projectcalico.org/v1 false BlockAffinity caliconodestatuses crd.projectcalico.org/v1 false CalicoNodeStatus clusterinformations crd.projectcalico.org/v1 false ClusterInformation felixconfigurations crd.projectcalico.org/v1 false FelixConfiguration globalnetworkpolicies crd.projectcalico.org/v1 false GlobalNetworkPolicy globalnetworksets crd.projectcalico.org/v1 false GlobalNetworkSet hostendpoints crd.projectcalico.org/v1 false HostEndpoint ipamblocks crd.projectcalico.org/v1 false IPAMBlock ipamconfigs crd.projectcalico.org/v1 false IPAMConfig ipamhandles crd.projectcalico.org/v1 false IPAMHandle ippools crd.projectcalico.org/v1 false IPPool ipreservations crd.projectcalico.org/v1 false IPReservation kubecontrollersconfigurations crd.projectcalico.org/v1 false KubeControllersConfiguration networkpolicies crd.projectcalico.org/v1 true NetworkPolicy networksets crd.projectcalico.org/v1 true NetworkSet endpointslices discovery.k8s.io/v1 true EndpointSlice events ev events.k8s.io/v1 true Event flowschemas flowcontrol.apiserver.k8s.io/v1beta3 false FlowSchema prioritylevelconfigurations flowcontrol.apiserver.k8s.io/v1beta3 false PriorityLevelConfiguration ingressclasses networking.k8s.io/v1 false IngressClass ingresses ing networking.k8s.io/v1 true Ingress networkpolicies netpol networking.k8s.io/v1 true NetworkPolicy runtimeclasses node.k8s.io/v1 false RuntimeClass poddisruptionbudgets pdb policy/v1 true PodDisruptionBudget clusterrolebindings rbac.authorization.k8s.io/v1 false ClusterRoleBinding clusterroles rbac.authorization.k8s.io/v1 false ClusterRole rolebindings rbac.authorization.k8s.io/v1 true RoleBinding roles rbac.authorization.k8s.io/v1 true Role priorityclasses pc scheduling.k8s.io/v1 false PriorityClass csidrivers storage.k8s.io/v1 false CSIDriver csinodes storage.k8s.io/v1 false CSINode csistoragecapacities storage.k8s.io/v1 true CSIStorageCapacity storageclasses sc storage.k8s.io/v1 false StorageClass volumeattachments storage.k8s.io/v1 false VolumeAttachment
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
- 61
- 62
- 63
- 64
- 65
- 66
- 67
- 68
- 69
- 70
- 71
- 72
- 73
- 74
- 75
借鉴别人的方法,创建rbac.yaml然后应用:
[root@k8s-master rbac]# cat rbac.yaml kind: Role apiVersion: rbac.authorization.k8s.io/v1 metadata: namespace: default name: pod-reader rules: #配置授权维度 - apiGroups: ["","apps"] #里面为空,为核心的api组,常用的资源都在核心组里面 resources: ["pods"] verbs: ["get", "watch", "list"] #资源操作方法 --- kind: RoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: read-pods namespace: default subjects: - kind: User name: lulei apiGroup: rbac.authorization.k8s.io roleRef: kind: Role name: pod-reader apiGroup: rbac.authorization.k8s.io [root@k8s-master rbac]# kubectl apply -f rbac.yaml role.rbac.authorization.k8s.io/pod-reader created rolebinding.rbac.authorization.k8s.io/read-pods created
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
当使用kucetl调用其api或者使用ui其实都是向api server组件发送的请求。
提取出证书里面的CN字段,该字段作为你的用户名。也就是从证书当中提取出用户名 “CN”: “hjw”,
使用 ClusterRoleBinding 可以对整个集群中的所有命名空间资源权限进行授权;以下 ClusterRoleBinding 样例展示了授权 manager 组内所有用户在全部命名空间中对 secrets 进行访问
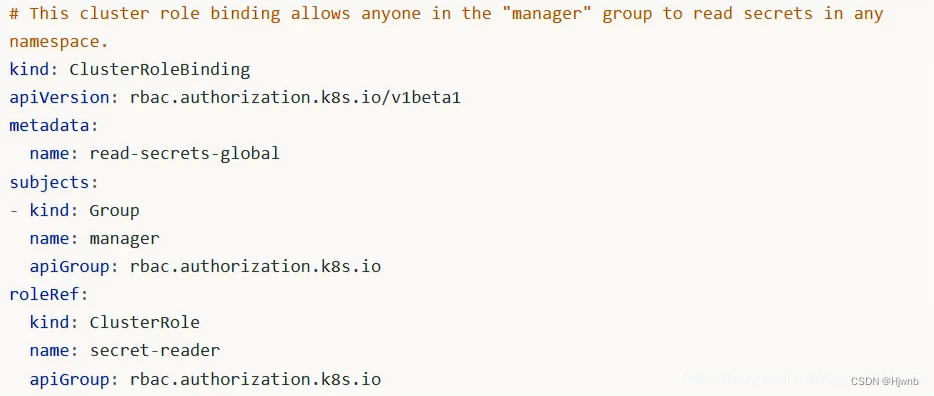
去验证你的身份是不是有效的,也就是你的证书是不是CA颁发的,验证客户端证书没问题进行下一个阶段的授权,也就是创建RBAC,授权之后可以访问。
使用kubeconfig还需要注意用户已经经过授权(如RBAC授权),上述例子中用户的证书中CN字段为"CN": “lulei”,kube-apiserver 预定义的 RoleBinding read-pods 将User lulei 与 Role pod-reader 绑定,该 Role 授予了调用kube-apiserver 相关 API 的权限。
4、使用创建好的role+kubeconfig+clientgo实现集群外win主机访问集群资源。
package main import ( "context" "fmt" v1 "k8s.io/apimachinery/pkg/apis/meta/v1" "k8s.io/client-go/kubernetes" "k8s.io/client-go/tools/clientcmd" ) func main() { // uses the current context in kubeconfig // path-to-kubeconfig -- for example, /root/.kube/config config, err := clientcmd.BuildConfigFromFlags("", "C:\\Users\\HJW\\.kube\\config_linux") if err != nil { panic(err) } // creates the clientset clientset, err := kubernetes.NewForConfig(config) if err != nil { panic(err) } stopCh := make(chan struct{}) defer close(stopCh) // sharedInformers := informers.NewSharedInformerFactory(clientset, time.Minute) // informer := sharedInformers.Core().V1().Pods().Informer() // access the API to list pods pods, err := clientset.CoreV1().Pods("default").List(context.TODO(), v1.ListOptions{}) if err != nil { panic(err) } fmt.Printf("There are %d pods in the cluster\n", len(pods.Items)) for _, d := range pods.Items { fmt.Printf("namespace:%v \t name:%v \t statu:%+v \n", d.Namespace, d.Name, d.Status.Phase) } // informer.AddEventHandler(cache.ResourceEventHandlerFuncs{ // AddFunc: func(obj interface{}) { // mObj := obj.(v1.Object) // log.Printf("New Pod Added to Stror: %s", mObj.GetName()) // }, // UpdateFunc: func(oldObj, newObj interface{}) { // oObj := oldObj.(v1.Object) // nObj := newObj.(v1.Object) // log.Printf("%s Pod Updated to %s", oObj.GetName(), nObj.GetName()) // }, // DeleteFunc: func(obj interface{}) { // mObj := obj.(v1.Object) // log.Printf("Pod Delete from Store: %s", mObj.GetName()) // }, // }) // informer.Run(stopCh) }
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
- 33
- 34
- 35
- 36
- 37
- 38
- 39
- 40
- 41
- 42
- 43
- 44
- 45
- 46
- 47
- 48
- 49
- 50
- 51
- 52
- 53
- 54
- 55
- 56
- 57
- 58
- 59
- 60
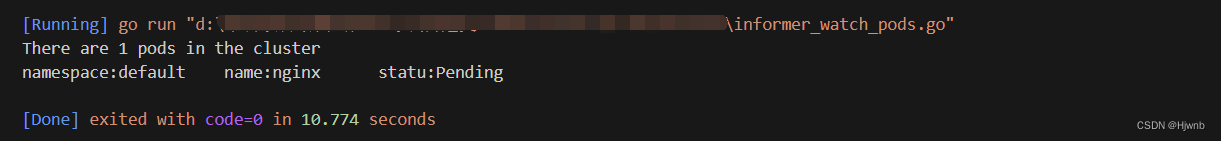
这是运行结果,可以看出来已经找出了default命名空间中的pod,使用的是hjw的role。
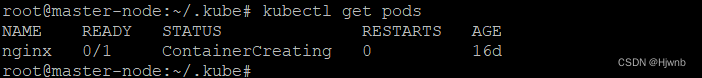
在集群中进行求证,发现没问题。



