- 1LangChain 44 深入理解LangChain 表达式语言八 Runnable接口输入输出模式 LangChain Expression Language (LCEL)_langchain chains 流输出接口
- 2Mysql数据库SQL执行流程_mysql sql执行过程
- 3ChatGLM 金融大模型决赛方案总结
- 4android开机自启动apk_开机启动apk下载软件
- 5发现一款提高工作效率的利器——ONLYOFFICE办公软件_only office
- 6自动化测试经验分享系列----自动化测试理解误区
- 7栈的表示和实现_(a[i]!=s[top])
- 8sklearn朴素贝叶斯分类器_机器学习算法(二)朴素贝叶斯(Naive Bayes)
- 9secure boot (二)基本概念和框架_secureboot
- 10单链表的定义初始化、CRUD (超详细、完整代码)_初始化单链表代码
IPSec简介_ipsec保护子网能为具体ip吗
赞
踩
起源
随着Internet的发展,越来越多的企业直接通过Internet进行互联,但由于IP协议未考虑安全性,而且Internet上有大量的不可靠用户和网络设备,所以用户业务数据要穿越这些未知网络,根本无法保证数据的安全性,数据易被伪造、篡改或窃取。因此,迫切需要一种兼容IP协议的通用的网络安全方案。
为了解决上述问题,IPSec(Internet Protocol Security)应运而生。IPSec是对IP的安全性补充,其工作在IP层,为IP网络通信提供透明的安全服务。
定义
IPSec是IETF(Internet Engineering Task Force)制定的一组开放的网络安全协议。它并不是一个单独的协议,而是一系列为IP网络提供安全性的协议和服务的集合,包括认证头AH(Authentication Header)和封装安全载荷ESP(Encapsulating Security Payload)两个安全协议、密钥交换和用于验证及加密的一些算法等。
通过这些协议,在两个设备之间建立一条IPSec隧道。数据通过IPSec隧道进行转发,实现保护数据的安全性。
受益
IPSec通过加密与验证等方式,从以下几个方面保障了用户业务数据在Internet中的安全传输:
- 数据来源验证:接收方验证发送方身份是否合法。
- 数据加密:发送方对数据进行加密,以密文的形式在Internet上传送,接收方对接收的加密数据进行解密后处理或直接转发。
- 数据完整性:接收方对接收的数据进行验证,以判定报文是否被篡改。
- 抗重放:接收方拒绝旧的或重复的数据包,防止恶意用户通过重复发送捕获到的数据包所进行的攻击。
配置Efficient VPN采用Client模式建立IPSec隧道示例
组网需求
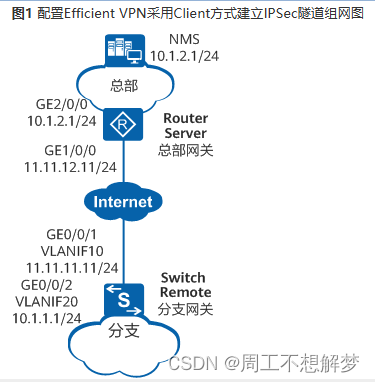
如图1所示,Switch为企业远程小型分支网关,Router为企业总部网关,分支与总部通过公网建立通信,并且总部与分支的网络未做统一规划。
企业希望通过网管系统(NMS)管理分支网关,并对分支网关与NMS之间相互访问的流量进行安全保护,并且分支网关配置能够尽量简单,由总部网关对分支网关进行集中管理。此时,可以在分支网关与总部网关之间采用Efficient VPN Client模式建立一个IPSec隧道来实施安全保护,便于IPSec隧道的建立与维护管理。
Efficient VPN Client模式下,Switch向Router申请IP地址用于建立IPSec隧道,同时申请DNS域名、DNS服务器地址和WINS服务器地址,提供给分支使用。
华为S交换机仅支持作为Efficient VPN的Remote端,本举例使用AR3200系列路由器作为Efficient VPN的Server端,以V200R008版本的AR3260路由器给出配置。现网中请根据实际情况选择Efficient VPN的Server端设备,并参考对应手册完成配置。
分支网关的VLANIF10接口通过DHCP获取IP地址,这里假设获取的IP地址为11.11.11.11。
配置思路
采用如下思路配置Efficient VPN采用Client模式建立IPSec隧道示例:
-
在Switch和Router上配置接口的IP地址和到对端的静态路由,保证路由可达。
-
Router作为IPSec隧道协商响应方,采用策略模板方式与Switch建立IPSec隧道。
-
Router上配置要推送的资源属性,包括IP地址、DNS域名、DNS服务器地址和WINS服务器地址。
-
在Switch上采用Client方式配置Efficient VPN,作为协商发起方与Router建立IPSec隧道。
操作步骤
- 配置接口的IP地址和到对端的静态路由
# 在Switch上配置接口的IP地址。
- <span style="color:#333333"><span style="background-color:#ffffff"><span style="background-color:#dddddd"><HUAWEI> <strong>system-view</strong>
- [HUAWEI] <strong>sysname Switch</strong>
- [Switch] <strong>vlan batch 10 20</strong>
- [Switch] <strong>interface gigabitethernet 0/0/1</strong>
- [Switch-GigabitEthernet0/0/1] <strong>port link-type trunk</strong>
- [Switch-GigabitEthernet0/0/1] <strong>port trunk allow-pass vlan 10</strong>
- [Switch-GigabitEthernet0/0/1] <strong>quit</strong>
- [Switch] <strong>interface gigabitethernet 0/0/2</strong>
- [Switch-GigabitEthernet0/0/2] <strong>port link-type trunk</strong>
- [Switch-GigabitEthernet0/0/2] <strong>port trunk allow-pass vlan 20</strong>
- [Switch-GigabitEthernet0/0/2] <strong>quit</strong>
- [Switch] <strong>interface vlanif 10</strong>
- [Switch-Vlanif10] <strong>ip address dhcp-alloc</strong>
- [Switch-Vlanif10] <strong>quit</strong>
- [Switch] <strong>interface vlanif 20</strong>
- [Switch-Vlanif20] <strong>ip address 10.1.1.1 255.255.255.0</strong>
- [Switch-Vlanif20] <strong>quit</strong></span></span></span>
# 在Switch上配置到对端的静态路由,此处假设到对端的下一跳地址为11.11.11.12。
<span style="color:#333333"><span style="background-color:#ffffff"><span style="background-color:#dddddd">[Switch] <strong>ip route-static 0.0.0.0 0.0.0.0 11.11.11.12</strong></span></span></span># 在Router上配置接口的IP地址。
- <span style="color:#333333"><span style="background-color:#ffffff"><span style="background-color:#dddddd"><HUAWEI> <strong>system-view</strong>
- [HUAWEI] <strong>sysname Router</strong>
- [Router] <strong>interface gigabitethernet 1/0/0</strong>
- [Router-GigabitEthernet1/0/0] <strong>ip address 11.11.12.11 255.255.255.0</strong>
- [Router-GigabitEthernet1/0/0] <strong>quit</strong>
- [Router] <strong>interface gigabitethernet 2/0/0</strong>
- [Router-GigabitEthernet2/0/0] <strong>ip address 10.1.2.1 255.255.255.0</strong>
- [Router-GigabitEthernet2/0/0] <strong>quit</strong></span></span></span>
# 在Router上配置到对端的静态路由,此处假设到对端的下一跳地址为11.11.12.12。
- <span style="color:#333333"><span style="background-color:#ffffff"><span style="background-color:#dddddd">[Router] <strong>ip route-static 11.11.11.0 255.255.255.0 11.11.12.12</strong>
- [Router] <strong>ip route-static 10.1.1.0 255.255.255.0 11.11.12.12</strong>
- [Router] <strong>ip route-static 100.1.1.0 255.255.255.0 11.11.12.12</strong></span></span></span>
- Router作为IPSec隧道协商响应方,采用策略模板方式与Switch建立IPSec隧道
# 配置要推送的资源属性,推送IP地址、DNS域名、DNS服务器地址和WINS服务器地址。
- <span style="color:#333333"><span style="background-color:#ffffff"><span style="background-color:#dddddd">[Router] <strong>ip pool po1</strong>
- [Router-ip-pool-po1] <strong>network 100.1.1.0 mask 255.255.255.128</strong>
- [Router-ip-pool-po1] <strong>gateway-list 100.1.1.1</strong>
- [Router-ip-pool-po1] <strong>quit</strong>
- [Router] <strong>aaa</strong>
- [Router-aaa] <strong>service-scheme schemetest </strong>
- [Router-aaa-service-schemetest] <strong>ip-pool po1</strong>
- [Router-aaa-service-schemetest] <strong>dns-name mydomain.com.cn</strong>
- [Router-aaa-service-schemetest] <strong>dns 2.2.2.2</strong>
- [Router-aaa-service-schemetest] <strong>dns 2.2.2.3 secondary</strong>
- [Router-aaa-service-schemetest] <strong>wins 3.3.3.2</strong>
- [Router-aaa-service-schemetest] <strong>wins 3.3.3.3 secondary</strong>
- [Router-aaa-service-schemetest] <strong>quit</strong>
- [Router-aaa] <strong>quit</strong></span></span></span>
# 配置IKE安全提议和IKE对等体,并将AAA业务模板绑定在IKE对等体中。
- <span style="color:#333333"><span style="background-color:#ffffff"><span style="background-color:#dddddd">[Router] <strong>ike proposal 5</strong>
- [Router-ike-proposal-5] <strong>dh group14</strong>
- [Router-ike-proposal-5] <strong>authentication-algorithm sha2-256</strong>
- [Router-ike-proposal-5] <strong>encryption-algorithm aes-128</strong>
- [Router-ike-proposal-5] <strong>quit</strong>
- [Router] <strong>ike peer rut3</strong>
- [Router-ike-peer-rut3] <strong>undo version 2</strong>
- [Router-ike-peer-rut3] <strong>exchange-mode aggressive</strong>
- [Router-ike-peer-rut3] <strong>pre-shared-key cipher Example@123</strong>
- [Router-ike-peer-rut3] <strong>ike-proposal 5</strong>
- [Router-ike-peer-rut3] <strong>service-scheme schemetest</strong>
- [Router-ike-peer-rut3] <strong>quit</strong></span></span></span>
# 配置IPSec安全提议、策略模板方式的安全策略。
- <span style="color:#333333"><span style="background-color:#ffffff"><span style="background-color:#dddddd">[Router] <strong>ipsec proposal prop1</strong>
- [Router-ipsec-proposal-prop1] <strong>esp authentication-algorithm sha2-256</strong>
- [Router-ipsec-proposal-prop1] <strong>esp encryption-algorithm aes 128</strong>
- [Router-ipsec-proposal-prop1] <strong>quit</strong>
- [Router] <strong>ipsec policy-template temp1 10</strong>
- [Router-ipsec-policy-templet-temp1-10] <strong>ike-peer rut3</strong>
- [Router-ipsec-policy-templet-temp1-10] <strong>proposal prop1</strong>
- [Router-ipsec-policy-templet-temp1-10] <strong>quit</strong>
- [Router] <strong>ipsec policy policy1 10 isakmp template temp1</strong></span></span></span>
# 开启SHA-2算法兼容RFC标准算法功能。
<span style="color:#333333"><span style="background-color:#ffffff"><span style="background-color:#dddddd">[Router] <strong>ipsec authentication sha2 compatible enable</strong></span></span></span># 在接口上应用安全策略组。
- <span style="color:#333333"><span style="background-color:#ffffff"><span style="background-color:#dddddd">[Router] <strong>interface gigabitethernet 1/0/0</strong>
- [Router-GigabitEthernet1/0/0] <strong>ipsec policy policy1</strong>
- [Router-GigabitEthernet1/0/0] <strong>quit</strong></span></span></span>
- 在Switch上采用Client方式配置Efficient VPN,建立IPSec隧道。
# 配置Efficient VPN的模式为Client模式,并在模式视图下指定IKE协商时的对端地址和预共享密钥。
- <span style="color:#333333"><span style="background-color:#ffffff"><span style="background-color:#dddddd">[Switch] <strong>ipsec efficient-vpn evpn mode client</strong>
- [Switch-ipsec-efficient-vpn-evpn] <strong>remote-address 11.11.12.11 v2</strong>
- [Switch-ipsec-efficient-vpn-evpn] <strong>pre-shared-key cipher Example@123</strong>
- [Switch-ipsec-efficient-vpn-evpn] <strong>dh group14</strong>
- [Switch-ipsec-efficient-vpn-evpn] <strong>quit</strong></span></span></span>
# 在接口上应用Efficient VPN。
- <span style="color:#333333"><span style="background-color:#ffffff"><span style="background-color:#dddddd">[Switch] <strong>interface vlanif 10</strong>
- [Switch-Vlanif10] <strong>ipsec efficient-vpn evpn</strong>
- [Switch-Vlanif10] <strong>quit</strong></span></span></span>
- 检查配置结果
# 配置成功后,总部Ping分支网关IP地址时,执行命令display ipsec packet statistics可以查看数据包的统计信息。
# 在Switch上执行display ike sa操作,结果如下。
- <span style="color:#333333"><span style="background-color:#ffffff"><span style="background-color:#dddddd">[Switch] <strong id="ZH-CN_TASK_0176374932__b32377308180218">display ike sa</strong>
- Conn-ID Peer VPN Flag(s) Phase RemoteType RemoteID
- ------------------------------------------------------------------------------
- 26 11.11.12.11 0 RD|ST v2:2 IP 11.11.12.11
- 25 11.11.12.11 0 RD|ST v2:1 IP 11.11.12.11
- Number of IKE SA : 2
- ------------------------------------------------------------------------------
- Flag Description:
- RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT
- HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP
- M--ACTIVE S--STANDBY A--ALONE NEG--NEGOTIATING </span></span></span>
配置文件
-
Switch的配置文件
- <span style="color:#333333"><span style="background-color:#ffffff"><span style="background-color:#dddddd">#
- sysname Switch
- #
- vlan batch 10 20
- #
- ipsec efficient-vpn evpn mode client
- remote-address 11.11.12.11 v2
- pre-shared-key cipher %^%#`[OXA]:r)798<)(J~%z-#<3+XezdN'h<O$IZvadN%^%#
- dh group14
- #
- interface Vlanif10
- ip address dhcp-alloc
- ipsec efficient-vpn evpn
- #
- interface Vlanif20
- ip address 10.1.1.1 255.255.255.0
- #
- interface GigabitEthernet0/0/1
- port link-type trunk
- port trunk allow-pass vlan 10
- #
- interface GigabitEthernet0/0/2
- port link-type trunk
- port trunk allow-pass vlan 20
- #
- ip route-static 0.0.0.0 0.0.0.0 11.11.11.12
- #
- return
- </span></span></span>
-
Router的配置文件
- <span style="color:#333333"><span style="background-color:#ffffff"><span style="background-color:#dddddd">#
- sysname Router
- #
- ipsec authentication sha2 compatible enable
- #
- ipsec proposal prop1
- esp authentication-algorithm sha2-256
- esp encryption-algorithm aes 128
- #
- ike proposal 5
- encryption-algorithm aes-128
- dh group14
- authentication-algorithm sha2-256
- authentication-method pre-share
- integrity-algorithm hmac-sha2-256
- prf hmac-sha2-256
- #
- ike peer rut3
- undo version 2
- exchange-mode aggressive
- pre-shared-key cipher %^%#0Y:SO]e%1MLLlY2v\bk~S]LxLau_yPzpUr>C%TO3%^%#
- ike-proposal 5
- service-scheme schemetest
- #
- ipsec policy-template temp1 10
- ike-peer rut3
- proposal prop1
- #
- ipsec policy policy1 10 isakmp template temp1
- #
- ip pool po1
- gateway-list 100.1.1.1
- network 100.1.1.0 mask 255.255.255.128
- #
- aaa
- service-scheme schemetest
- dns 2.2.2.2
- dns 2.2.2.3 secondary
- ip-pool po1
- wins 3.3.3.2
- wins 3.3.3.3 secondary
- dns-name mydomain.com.cn
- #
- interface GigabitEthernet1/0/0
- ip address 11.11.12.11 255.255.255.0
- ipsec policy policy1
- #
- interface GigabitEthernet2/0/0
- ip address 10.1.2.1 255.255.255.0
- #
- ip route-static 10.1.1.0 255.255.255.0 11.11.12.12
- ip route-static 11.11.11.0 255.255.255.0 11.11.12.12
- ip route-static 100.1.1.0 255.255.255.0 11.11.12.12
- #
- return</span></span></span>
周工这里还有很多实验:关注+点赞+发送私信“题库”领取
HCIA实验拓扑
HCIP实验拓扑
关注+点赞+发送私信“题库”领取