- 1Centos 8 stream安装snort3(2023年2月3日更新部分问题)_flatbuffers安装
- 2免费AI开源引擎:在电力电网工单系统中智能解析的应用场景_开源电力分析系统
- 3基于微信小程序开发的酒店管理系统_酒店微信小程序界面
- 4算法训练营day60
- 5声临其境!当ChatTTS遇上腾讯云HAI,定制你的专属智能语音服务_chat-tts可以用自己的声音吗
- 6如何把自己写的驱动编进内核_编写一个字符设备驱动,编译进内核驱动
- 7第7章 大模型的数据与标注7.2 标注工具与方法7.2.2 自动化标注与半监督学习_大模型数据标注
- 810款在线网站原型设计工具 总有一款适合你_在线web原型
- 9FinClip小程序+Rust(五):用内联SVG实现二维码_svg二维码生成
- 10vue和element ui用el-switch滑动开关改变每行的状态,源码例子_element滑动开关
网络安全之IPSEC路由基本配置_ipsec 喷段路由
赞
踩
目录
网络安全之IPSEC路由基本配置
IPSEC配置的前提分析
协议分析
传输模式分析编辑
IPSEC路由中的配置
图谱图
配置公网可达
R1配置IKE SA的安全提议
R1配置 IKE SA 的身份认证信息
R3配置IKE SA的安全提议
R3配置 IKE SA 的身份认证信息
R1配置IPSEC的安全提议
R1配置感兴趣流
R1配置安全策略集
R3配置IPSEC的安全提议
R3配置感兴趣流
R3配置安全策略集
在接口调安全策略集
启动
测试
网络安全之IPSEC路由基本配置
IPSEC配置的前提分析
协议分析
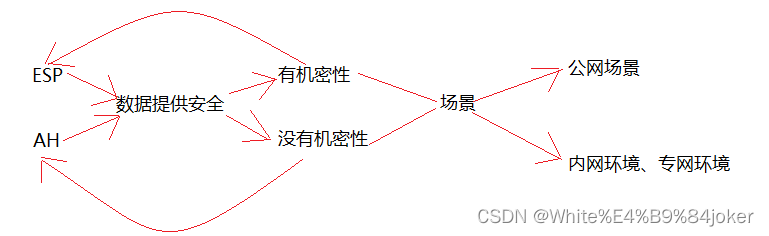
传输模式分析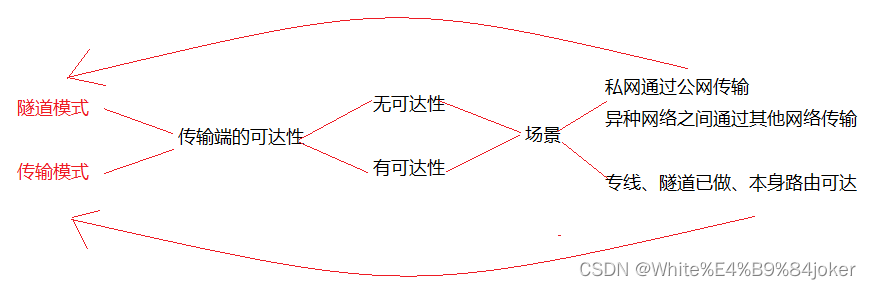
IPSEC路由中的配置
图谱图
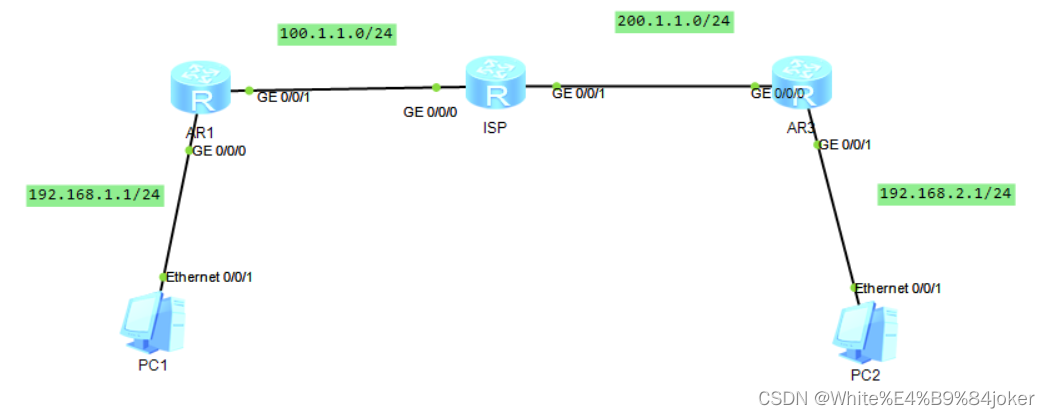
注意:
此场景为私网之间配置
配置公网可达
R1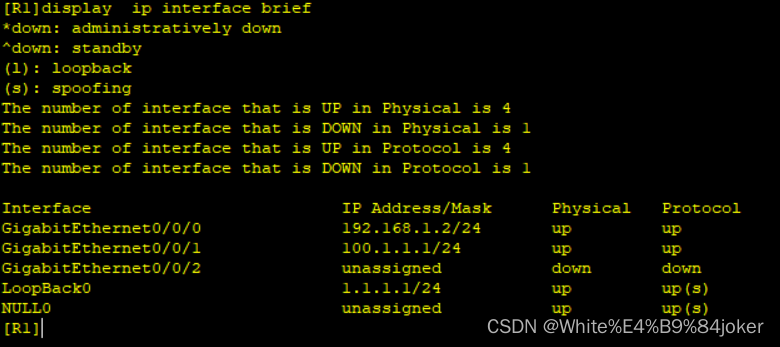
ISP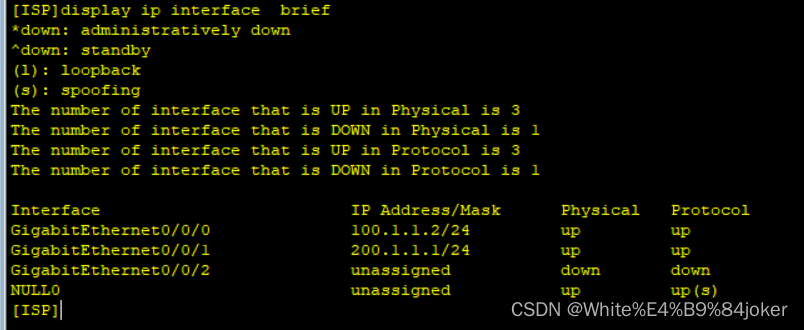
R3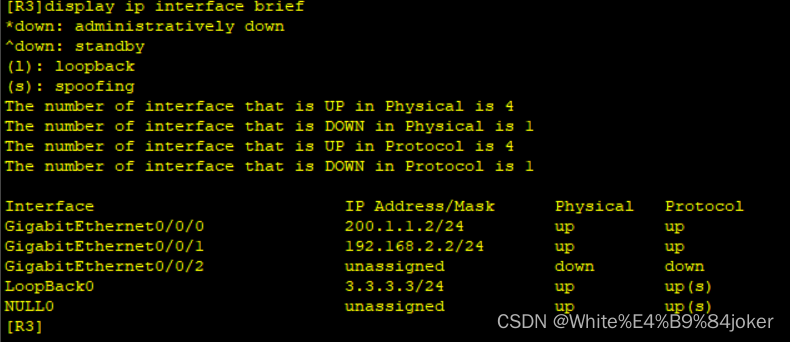
配置静态路由使得公网可达
[R1]ip route-static 192.168.2.0 24 100.1.1.2
[R1]ip route-static 200.1.1.0 24 100.1.1.2
[R3]ip route-static 100.1.1.0 24 200.1.1.1
[R3]ip route-static 192.168.1.0 24 200.1.1.1
- 1
- 2
- 3
- 4
- 5
R1配置IKE SA的安全提议
[R1]ike proposal 1 --- 选择安全提议编号 [R1-ike-proposal-1]encryption-algorithm ? 3des-cbc 168 bits 3DES-CBC aes-cbc-128 Use AES-128 aes-cbc-192 Use AES-192 aes-cbc-256 Use AES-256 des-cbc 56 bits DES-CBC --- 比较弱,一般不选 [R1-ike-proposal-1]encryption-algorithm 3des-cbc [R1-ike-proposal-1]authentication-algorithm ? --- 认证加密算法 aes-xcbc-mac-96 Select aes-xcbc-mac-96 as the hash algorithm md5 Select MD5 as the hash algorithm sha1 Select SHA as the hash algorithm sm3 Select sm3 as the hash algorithm [R1-ike-proposal-1]authentication-algorithm sha1 --- 选择哈希算法 [R1-ike-proposal-1]authentication-method ? --- 认证模式 digital-envelope Select digital envelope key as the authentication method pre-share Select pre-shared key as the authentication method rsa-signature Select rsa-signature key as the authentication method [R1-ike-proposal-1]authentication-method pre-share --- 域共享 [R1-ike-proposal-1]dh ? --- 选择DH算法 group1 768 bits Diffie-Hellman group group14 2048 bits Diffie-Hellman group group2 1024 bits Diffie-Hellman group group5 1536 bits Diffie-Hellman group [R1-ike-proposal-1]dh group5 --- 一般选2以上强度,1太低 [R1-ike-proposal-1]sa duration ? --- 安全联盟周期 INTEGER<60-604800> Value of time(in seconds), default is 86400 [R1-ike-proposal-1]sa duration 3600
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- 31
- 32
R1配置 IKE SA 的身份认证信息
[R1]ike peer 1 ? --- 选择ike版本 v1 Only V1 SA's can be created v2 Only V2 SA's can be created <cr> Please press ENTER to execute command [R1]ike peer 1 v1 [R1-ike-peer-1]exchange-mode ? --- 选择模式 aggressive Aggressive mode --- 野蛮 main Main mode --- 主模式 [R1-ike-peer-1]exchange-mode main --- 主模式 [R1-ike-peer-1]pre-shared-key ? --- 预共享密钥 cipher Pre-shared-key with cipher text --- 本地不加密 simple Pre-shared-key with plain text --- 本地加密 [R1-ike-peer-1]pre-shared-key cipher 123 [R1-ike-peer-1]ike-proposal 1 --- 调用安全提议编号 [R1-ike-peer-1]remote-address 200.1.1.2 --- 对方IP
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
野蛮模式配置
ike peer yyy v1 exchange-mode aggressive //设置为野蛮模式 pre-shared-key simple 999 ike-proposal 1 local-id-type name //定义本地ID为name remote-name kkk //远程ID是 kkk remote-address 200.1.1.1
- 1
- 2
- 3
- 4
- 5
- 6
- 7
R3配置IKE SA的安全提议
[R3]ike proposal 1
[R3-ike-proposal-1]encryption-algorithm 3des-cbc
[R3-ike-proposal-1]dh group5
[R3-ike-proposal-1]authentication-algorithm sha1
[R3-ike-proposal-1]sa duration 3600
[R3-ike-proposal-1]q
- 1
- 2
- 3
- 4
- 5
- 6
R3配置 IKE SA 的身份认证信息
[R3]ike peer 1 v1
[R3-ike-peer-1]exchange-mode main
[R3-ike-peer-1]pre-shared-key cipher 123
[R3-ike-peer-1]ike-proposal 1
[R3-ike-peer-1]remote-address 100.1.1.1
[R3-ike-peer-1]
- 1
- 2
- 3
- 4
- 5
- 6
R1配置IPSEC的安全提议
[R1]ipsec proposal 1 --- 选择安全协议号 [R1-ipsec-proposal-1] [R1-ipsec-proposal-1]transform ? --- 选择封装协议 ah AH protocol defined in RFC2402 ah-esp ESP protocol first, then AH protocol esp ESP protocol defined in RFC2406 [R1-ipsec-proposal-1]transform esp --- 选择ESP协议 [R1-ipsec-proposal-1]esp authentication-algorithm ? --- 选择认证算法 md5 Use HMAC-MD5-96 algorithm sha1 Use HMAC-SHA1-96 algorithm sha2-256 Use SHA2-256 algorithm sha2-384 Use SHA2-384 algorithm sha2-512 Use SHA2-512 algorithm sm3 Use SM3 algorithm [R1-ipsec-proposal-1]esp authentication-algorithm sha2-512 [R1-ipsec-proposal-1]esp encryption-algorithm ? --- 加密算法 3des Use 3DES aes-128 Use AES-128 aes-192 Use AES-192 aes-256 Use AES-256 des Use DES sm1 Use SM1 <cr> Please press ENTER to execute command [R1-ipsec-proposal-1]esp encryption-algorithm aes-128 [R1-ipsec-proposal-1]encapsulation-mode tunnel --- 选择隧道模式
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
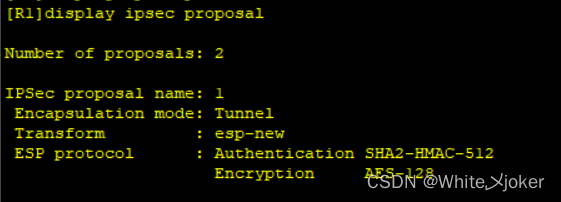
[R1]display ipsec proposal — 查询配置的IPSEC
R1配置感兴趣流
[R1]acl 3000
[R1-acl-adv-3000]rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.1
68.2.0 0.0.0.255
- 1
- 2
- 3
R1配置安全策略集
[R1]ipsec policy k 1 ? --- 选择协议
isakmp Indicates use IKE to establish the IPSec SA
manual Indicates use manual to establish the IPSec SA
<cr> Please press ENTER to execute command
[R1]ipsec policy k 1 isakmp --- 定义安全策略编号与协议
[R1-ipsec-policy-isakmp-k-1]proposal 1 --- 调用IPSEC SA 提议
[R1-ipsec-policy-isakmp-k-1]ike-peer 1 --- 调用身份认证信息
[R1-ipsec-policy-isakmp-k-1]security acl 3000 --- 调用感兴趣流
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
R3配置IPSEC的安全提议
[R3]ipsec proposal 1
[R3-ipsec-proposal-1]transform esp
[R3-ipsec-proposal-1]esp authentication-algorithm sha2-512
[R3-ipsec-proposal-1]esp encryption-algorithm aes-128
[R3-ipsec-proposal-1]encapsulation-mode tunnel
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
R3配置感兴趣流
[R3]acl 3000
[R3-acl-adv-3000]rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 192.1
68.1.0 0.0.0.255
- 1
- 2
- 3
- 4
R3配置安全策略集
[R3]ipsec policy k 1 isakmp
[R3-ipsec-policy-isakmp-k-1]proposal 1
[R3-ipsec-policy-isakmp-k-1]ike-peer 1
[R3-ipsec-policy-isakmp-k-1]security acl 3000
- 1
- 2
- 3
- 4
- 5
- 6
- 7
在接口调安全策略集
[R1-GigabitEthernet0/0/1]ipsec policy k
[R3-GigabitEthernet0/0/0]ipsec policy k
- 1
- 2
- 3
启动
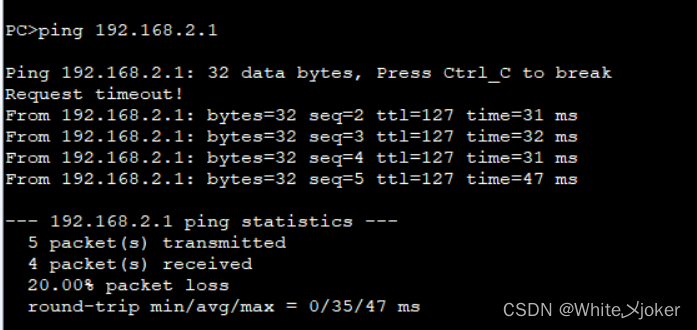
测试
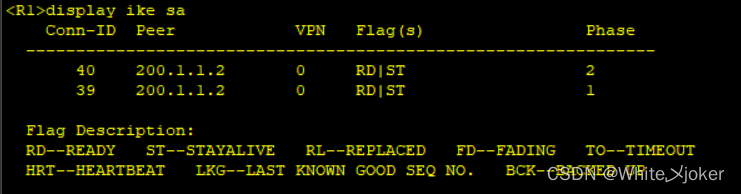
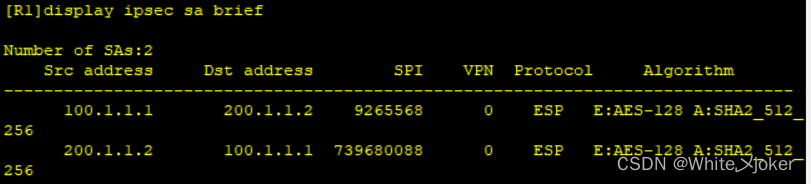
最后
从时代发展的角度看,网络安全的知识是学不完的,而且以后要学的会更多,同学们要摆正心态,既然选择入门网络安全,就不能仅仅只是入门程度而已,能力越强机会才越多。
因为入门学习阶段知识点比较杂,所以我讲得比较笼统,大家如果有不懂的地方可以找我咨询,我保证知无不言言无不尽,需要相关资料也可以找我要,我的网盘里一大堆资料都在吃灰呢。
干货主要有:
①1000+CTF历届题库(主流和经典的应该都有了)
②CTF技术文档(最全中文版)
③项目源码(四五十个有趣且经典的练手项目及源码)
④ CTF大赛、web安全、渗透测试方面的视频(适合小白学习)
⑤ 网络安全学习路线图(告别不入流的学习)
⑥ CTF/渗透测试工具镜像文件大全
⑦ 2023密码学/隐身术/PWN技术手册大全
如果你对网络安全入门感兴趣,那么你需要的话可以点击这里 本文内容由网友自发贡献,转载请注明出处:【wpsshop博客】
Copyright © 2003-2013 www.wpsshop.cn 版权所有,并保留所有权利。