热门标签
热门文章
- 1jdk1.8下载与安装教程(2023最新版)
- 2多模态生理信号情感识别 附代码+报告_eeg与ecg的多模态融合代码
- 3熵与自然语言处理:理解自然语言处理的基本原理
- 4课代表:ChatGPT及大模型专题研讨会_chatgpt研讨会
- 5【开题报告】Springboot仓储管理系统设计与开发x8w11计算机毕业设计源码、研究背景、意义、目的、内容、方案和预期成果_基于springboot的童年零食公司信息仓储管理系统的设计与实现的研究方向
- 6paddleocr的基本使用_paddleocr zlibwapi.dll
- 7大模型ChatGLM-6B实现本地部署_chatglm-6b-int4下载
- 8Machine Learning机器学习之文本分析的词法分析、句法分析、语义分析(详细讲解)
- 92020国赛C题_2020年国赛c题
- 10【pytorch】从入门到构建一个分类网络超长超详细教程(附代码)_
当前位置: article > 正文
基于yolov7开发构建学生课堂行为检测识别系统_scb学生行为识别yolo代码
作者:Monodyee | 2024-03-29 15:07:27
赞
踩
scb学生行为识别yolo代码
yolov7也是一款非常出众的目标检测模型,在我之前的文章中也有非常详细的教程系列的文章,感兴趣的话可以自行移步阅读即可。
《YOLOv7基于自己的数据集从零构建模型完整训练、推理计算超详细教程》
《基于YOLOv7融合轻量级网络MobileOne的表格检测识别分析系统》
《助力安全作业生产,基于YOLOv7融合Transformer开发构建安全帽检测识别分析系统》
《助力不文明行文识别,基于YOLOv7融合RepVGG的遛狗牵绳行为检测识别分析系统》
学生课堂行为检测是一个比较有实际意义也比较有趣的应用场景,在我之前的一些文章中也有过相关方面的实践如下:
《yolov4-tiny目标检测模型实战——学生姿势行为检测》
可以看到:这里模型选用的大都是yolov5及之前的系列模型,对于新款模型的使用则有所欠缺。
这里主要就是基于yolov7来开发构建学生课堂行为检测识别分析系统,首先看下效果图:

如果对yolov7的使用有问题可以看我超详细的教程:
YOLOv7基于自己的数据集从零构建模型完整训练、推理计算超详细教程_Together_CZ的博客-CSDN博客
接下来简单看下数据集情况:

数据来源于真实场景拍摄录制采集。
标注文件如下:

实例标注内容如下所示:
- 1 0.546875 0.5487132352941176 0.09166666666666666 0.10477941176470588
- 0 0.40208333333333335 0.5873161764705882 0.14583333333333334 0.3841911764705882
训练数据配置文件如下:
- # txt path
- train: ./dataset/images/train
- val: ./dataset/images/test
- test: ./dataset/images/test
-
-
-
- # number of classes
- nc: 3
-
- # class names
- names: ['study','sleep','phone']
模型文件如下:
- # parameters
- nc: 80 # number of classes
- depth_multiple: 1.0 # model depth multiple
- width_multiple: 1.0 # layer channel multiple
-
-
- # anchors
- anchors:
- - [10,13, 16,30, 33,23] # P3/8
- - [30,61, 62,45, 59,119] # P4/16
- - [116,90, 156,198, 373,326] # P5/32
-
-
- # backbone
- backbone:
- # [from, number, module, args] c2, k=1, s=1, p=None, g=1, act=True
- [[-1, 1, Conv, [32, 3, 2, None, 1, nn.LeakyReLU(0.1)]], # 0-P1/2
- [-1, 1, Conv, [64, 3, 2, None, 1, nn.LeakyReLU(0.1)]], # 1-P2/4
- [-1, 1, Conv, [32, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-2, 1, Conv, [32, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [32, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [32, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [[-1, -2, -3, -4], 1, Concat, [1]],
- [-1, 1, Conv, [64, 1, 1, None, 1, nn.LeakyReLU(0.1)]], # 7
- [-1, 1, MP, []], # 8-P3/8
- [-1, 1, Conv, [64, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-2, 1, Conv, [64, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [64, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [64, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [[-1, -2, -3, -4], 1, Concat, [1]],
- [-1, 1, Conv, [128, 1, 1, None, 1, nn.LeakyReLU(0.1)]], # 14
- [-1, 1, MP, []], # 15-P4/16
- [-1, 1, Conv, [128, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-2, 1, Conv, [128, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [128, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [128, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [[-1, -2, -3, -4], 1, Concat, [1]],
- [-1, 1, Conv, [256, 1, 1, None, 1, nn.LeakyReLU(0.1)]], # 21
- [-1, 1, MP, []], # 22-P5/32
- [-1, 1, Conv, [256, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-2, 1, Conv, [256, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [256, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [256, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [[-1, -2, -3, -4], 1, Concat, [1]],
- [-1, 1, Conv, [512, 1, 1, None, 1, nn.LeakyReLU(0.1)]], # 28
- ]
-
-
- # head
- head:
- [[-1, 1, Conv, [256, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-2, 1, Conv, [256, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, SP, [5]],
- [-2, 1, SP, [9]],
- [-3, 1, SP, [13]],
- [[-1, -2, -3, -4], 1, Concat, [1]],
- [-1, 1, Conv, [256, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [[-1, -7], 1, Concat, [1]],
- [-1, 1, Conv, [256, 1, 1, None, 1, nn.LeakyReLU(0.1)]], # 37
- [-1, 1, Conv, [128, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, nn.Upsample, [None, 2, 'nearest']],
- [21, 1, Conv, [128, 1, 1, None, 1, nn.LeakyReLU(0.1)]], # route backbone P4
- [[-1, -2], 1, Concat, [1]],
- [-1, 1, Conv, [64, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-2, 1, Conv, [64, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [64, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [64, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [[-1, -2, -3, -4], 1, Concat, [1]],
- [-1, 1, Conv, [128, 1, 1, None, 1, nn.LeakyReLU(0.1)]], # 47
- [-1, 1, Conv, [64, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, nn.Upsample, [None, 2, 'nearest']],
- [14, 1, Conv, [64, 1, 1, None, 1, nn.LeakyReLU(0.1)]], # route backbone P3
- [[-1, -2], 1, Concat, [1]],
- [-1, 1, Conv, [32, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-2, 1, Conv, [32, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [32, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [32, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [[-1, -2, -3, -4], 1, Concat, [1]],
- [-1, 1, Conv, [64, 1, 1, None, 1, nn.LeakyReLU(0.1)]], # 57
- [-1, 1, Conv, [128, 3, 2, None, 1, nn.LeakyReLU(0.1)]],
- [[-1, 47], 1, Concat, [1]],
- [-1, 1, Conv, [64, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-2, 1, Conv, [64, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [64, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [64, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [[-1, -2, -3, -4], 1, Concat, [1]],
- [-1, 1, Conv, [128, 1, 1, None, 1, nn.LeakyReLU(0.1)]], # 65
- [-1, 1, Conv, [256, 3, 2, None, 1, nn.LeakyReLU(0.1)]],
- [[-1, 37], 1, Concat, [1]],
- [-1, 1, Conv, [128, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-2, 1, Conv, [128, 1, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [128, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [-1, 1, Conv, [128, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [[-1, -2, -3, -4], 1, Concat, [1]],
- [-1, 1, Conv, [256, 1, 1, None, 1, nn.LeakyReLU(0.1)]], # 73
- [57, 1, Conv, [128, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [65, 1, Conv, [256, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [73, 1, Conv, [512, 3, 1, None, 1, nn.LeakyReLU(0.1)]],
- [[74,75,76], 1, IDetect, [nc, anchors]], # Detect(P3, P4, P5)
- ]
默认是100次epochde迭代计算,结果详情如下:
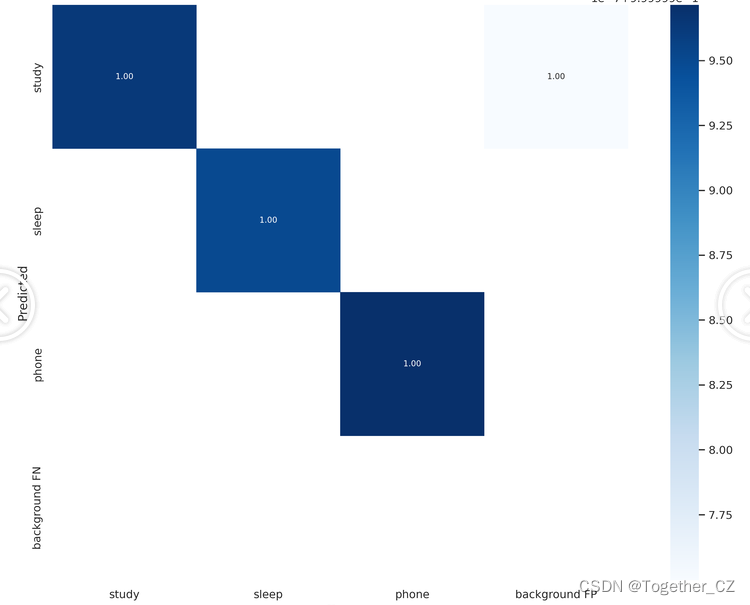
【混淆矩阵】
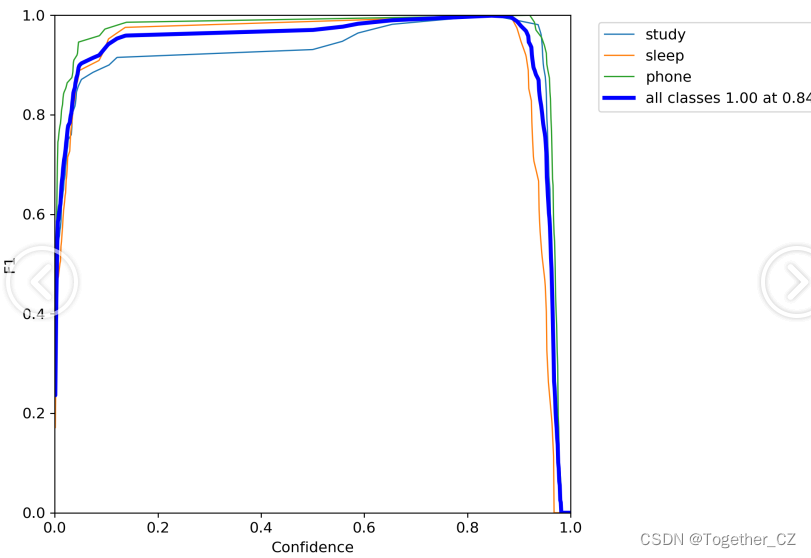
【F1值曲线】
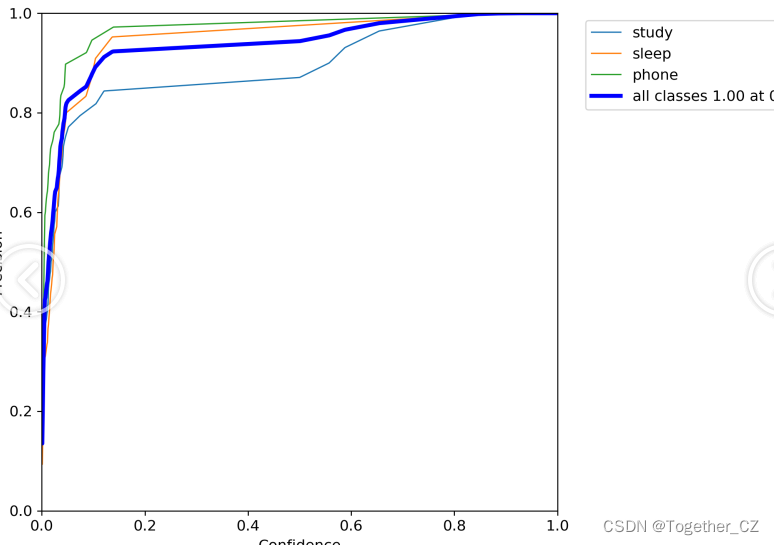
【精确率曲线】
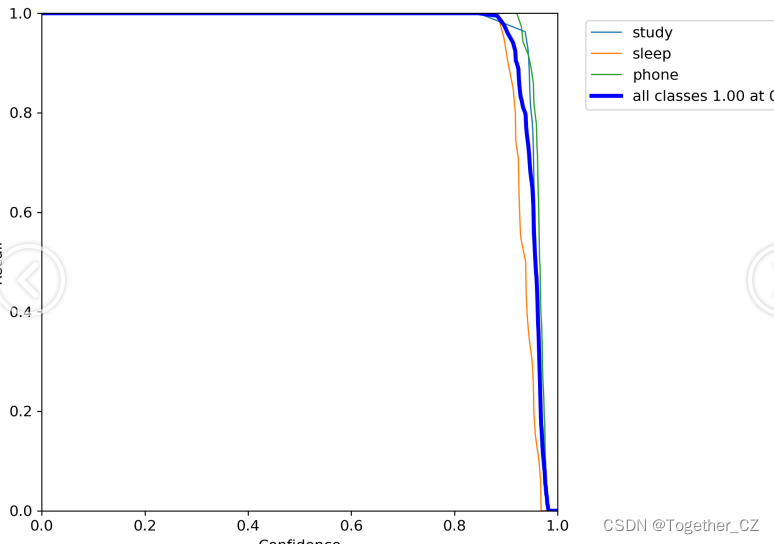
【召回率曲线】
【训练可视化】

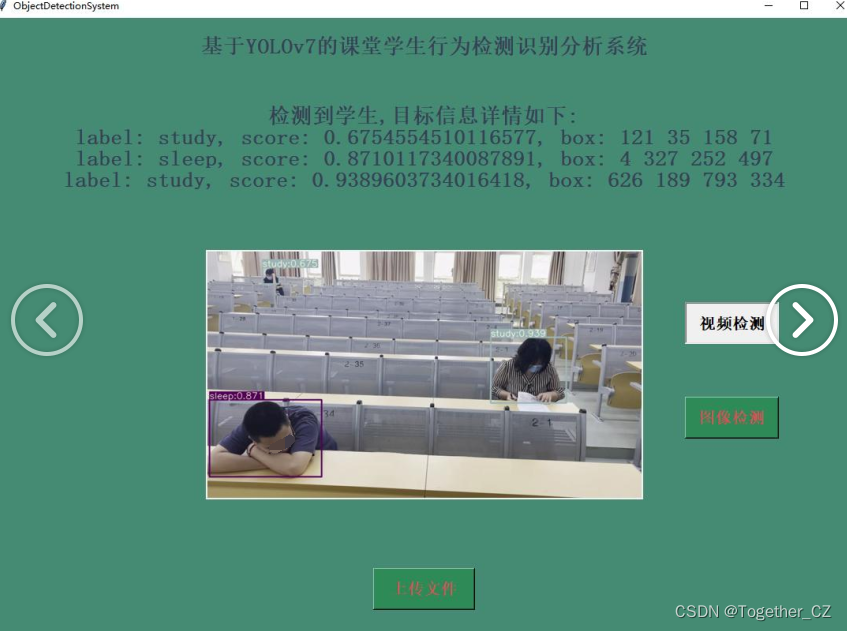
最后将整体模型的推理计算集成到可视化界面中,同时实现图像推理检测和视频推理检测,效果实例如下所示:
【图像推理】

【视频推理】
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/Monodyee/article/detail/335774
推荐阅读
相关标签


